mirror of
https://github.com/cotes2020/chirpy-starter.git
synced 2025-10-14 10:04:38 +10:00
4075 lines
78 KiB
HTML
4075 lines
78 KiB
HTML
<!doctype html>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- `site.alt_lang` can specify a language different from the UI -->
|
||
<html lang="en"
|
||
|
||
>
|
||
<!-- The Head -->
|
||
|
||
<head>
|
||
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
|
||
<meta name="theme-color" media="(prefers-color-scheme: light)" content="#f7f7f7">
|
||
<meta name="theme-color" media="(prefers-color-scheme: dark)" content="#1b1b1e">
|
||
<meta name="apple-mobile-web-app-capable" content="yes">
|
||
<meta name="apple-mobile-web-app-status-bar-style" content="black-translucent">
|
||
<meta
|
||
name="viewport"
|
||
content="width=device-width, user-scalable=no initial-scale=1, shrink-to-fit=no, viewport-fit=cover"
|
||
>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- Begin Jekyll SEO tag v2.8.0 -->
|
||
<meta name="generator" content="Jekyll v4.3.2" />
|
||
<meta property="og:title" content="Building a Custom Malware Analysis Lab Enviornment" />
|
||
<meta property="og:locale" content="en" />
|
||
<meta name="description" content="https://www.sentinelone.com/labs/building-a-custom-malware-analysis-lab-environment/" />
|
||
<meta property="og:description" content="https://www.sentinelone.com/labs/building-a-custom-malware-analysis-lab-environment/" />
|
||
<link rel="canonical" href="http://localhost:4000/posts/Building-a-Custom-Malware-Analysis-Lab-Environment/" />
|
||
<meta property="og:url" content="http://localhost:4000/posts/Building-a-Custom-Malware-Analysis-Lab-Environment/" />
|
||
<meta property="og:site_name" content="neo’s brain" />
|
||
<meta property="og:type" content="article" />
|
||
<meta property="article:published_time" content="2023-08-23T15:33:46-05:00" />
|
||
<meta name="twitter:card" content="summary" />
|
||
<meta property="twitter:title" content="Building a Custom Malware Analysis Lab Enviornment" />
|
||
<script type="application/ld+json">
|
||
{"@context":"https://schema.org","@type":"BlogPosting","dateModified":"2023-08-23T15:37:29-05:00","datePublished":"2023-08-23T15:33:46-05:00","description":"https://www.sentinelone.com/labs/building-a-custom-malware-analysis-lab-environment/","headline":"Building a Custom Malware Analysis Lab Enviornment","mainEntityOfPage":{"@type":"WebPage","@id":"http://localhost:4000/posts/Building-a-Custom-Malware-Analysis-Lab-Environment/"},"url":"http://localhost:4000/posts/Building-a-Custom-Malware-Analysis-Lab-Environment/"}</script>
|
||
<!-- End Jekyll SEO tag -->
|
||
|
||
|
||
|
||
<title>Building a Custom Malware Analysis Lab Enviornment | neo's brain
|
||
</title>
|
||
|
||
<!--
|
||
The Favicons for Web, Android, Microsoft, and iOS (iPhone and iPad) Apps
|
||
Generated by: https://realfavicongenerator.net/
|
||
-->
|
||
|
||
|
||
|
||
<link rel="apple-touch-icon" sizes="180x180" href="/assets/img/favicons/apple-touch-icon.png">
|
||
<link rel="icon" type="image/png" sizes="32x32" href="/assets/img/favicons/favicon-32x32.png">
|
||
<link rel="icon" type="image/png" sizes="16x16" href="/assets/img/favicons/favicon-16x16.png">
|
||
<link rel="manifest" href="/assets/img/favicons/site.webmanifest">
|
||
<link rel="shortcut icon" href="/assets/img/favicons/favicon.ico">
|
||
<meta name="apple-mobile-web-app-title" content="neo's brain">
|
||
<meta name="application-name" content="neo's brain">
|
||
<meta name="msapplication-TileColor" content="#da532c">
|
||
<meta name="msapplication-config" content="/assets/img/favicons/browserconfig.xml">
|
||
<meta name="theme-color" content="#ffffff">
|
||
|
||
|
||
|
||
|
||
<link rel="preconnect" href="https://fonts.googleapis.com" >
|
||
<link rel="dns-prefetch" href="https://fonts.googleapis.com" >
|
||
|
||
<link rel="preconnect" href="https://fonts.gstatic.com" crossorigin>
|
||
<link rel="dns-prefetch" href="https://fonts.gstatic.com" crossorigin>
|
||
|
||
<link rel="preconnect" href="https://fonts.googleapis.com" >
|
||
<link rel="dns-prefetch" href="https://fonts.googleapis.com" >
|
||
|
||
<link rel="preconnect" href="https://cdn.jsdelivr.net" >
|
||
<link rel="dns-prefetch" href="https://cdn.jsdelivr.net" >
|
||
|
||
|
||
<link rel="stylesheet" href="https://fonts.googleapis.com/css2?family=Lato&family=Source+Sans+Pro:wght@400;600;700;900&display=swap">
|
||
|
||
|
||
<!-- GA -->
|
||
|
||
|
||
<!-- Bootstrap -->
|
||
<link rel="stylesheet" href="https://cdn.jsdelivr.net/npm/bootstrap@5.2.3/dist/css/bootstrap.min.css">
|
||
|
||
<!-- Font Awesome -->
|
||
<link rel="stylesheet" href="https://cdn.jsdelivr.net/npm/@fortawesome/fontawesome-free@6.4.0/css/all.min.css">
|
||
|
||
<link rel="stylesheet" href="/assets/css/style.css">
|
||
|
||
|
||
<link rel="stylesheet" href="https://cdn.jsdelivr.net/npm/tocbot@4.21.0/dist/tocbot.min.css">
|
||
|
||
|
||
|
||
<!-- Manific Popup -->
|
||
<link rel="stylesheet" href="https://cdn.jsdelivr.net/npm/magnific-popup@1.1.0/dist/magnific-popup.min.css">
|
||
|
||
|
||
<!-- JavaScript -->
|
||
|
||
|
||
<!-- Switch the mode between dark and light. -->
|
||
|
||
<script type="text/javascript">
|
||
class ModeToggle {
|
||
static get MODE_KEY() {
|
||
return 'mode';
|
||
}
|
||
static get MODE_ATTR() {
|
||
return 'data-mode';
|
||
}
|
||
static get DARK_MODE() {
|
||
return 'dark';
|
||
}
|
||
static get LIGHT_MODE() {
|
||
return 'light';
|
||
}
|
||
static get ID() {
|
||
return 'mode-toggle';
|
||
}
|
||
|
||
constructor() {
|
||
if (this.hasMode) {
|
||
if (this.isDarkMode) {
|
||
if (!this.isSysDarkPrefer) {
|
||
this.setDark();
|
||
}
|
||
} else {
|
||
if (this.isSysDarkPrefer) {
|
||
this.setLight();
|
||
}
|
||
}
|
||
}
|
||
|
||
let self = this;
|
||
|
||
/* always follow the system prefers */
|
||
this.sysDarkPrefers.addEventListener('change', () => {
|
||
if (self.hasMode) {
|
||
if (self.isDarkMode) {
|
||
if (!self.isSysDarkPrefer) {
|
||
self.setDark();
|
||
}
|
||
} else {
|
||
if (self.isSysDarkPrefer) {
|
||
self.setLight();
|
||
}
|
||
}
|
||
|
||
self.clearMode();
|
||
}
|
||
|
||
self.notify();
|
||
});
|
||
} /* constructor() */
|
||
|
||
get sysDarkPrefers() {
|
||
return window.matchMedia('(prefers-color-scheme: dark)');
|
||
}
|
||
|
||
get isSysDarkPrefer() {
|
||
return this.sysDarkPrefers.matches;
|
||
}
|
||
|
||
get isDarkMode() {
|
||
return this.mode === ModeToggle.DARK_MODE;
|
||
}
|
||
|
||
get isLightMode() {
|
||
return this.mode === ModeToggle.LIGHT_MODE;
|
||
}
|
||
|
||
get hasMode() {
|
||
return this.mode != null;
|
||
}
|
||
|
||
get mode() {
|
||
return sessionStorage.getItem(ModeToggle.MODE_KEY);
|
||
}
|
||
|
||
/* get the current mode on screen */
|
||
get modeStatus() {
|
||
if (this.isDarkMode || (!this.hasMode && this.isSysDarkPrefer)) {
|
||
return ModeToggle.DARK_MODE;
|
||
} else {
|
||
return ModeToggle.LIGHT_MODE;
|
||
}
|
||
}
|
||
|
||
setDark() {
|
||
document.documentElement.setAttribute(ModeToggle.MODE_ATTR, ModeToggle.DARK_MODE);
|
||
sessionStorage.setItem(ModeToggle.MODE_KEY, ModeToggle.DARK_MODE);
|
||
}
|
||
|
||
setLight() {
|
||
document.documentElement.setAttribute(ModeToggle.MODE_ATTR, ModeToggle.LIGHT_MODE);
|
||
sessionStorage.setItem(ModeToggle.MODE_KEY, ModeToggle.LIGHT_MODE);
|
||
}
|
||
|
||
clearMode() {
|
||
document.documentElement.removeAttribute(ModeToggle.MODE_ATTR);
|
||
sessionStorage.removeItem(ModeToggle.MODE_KEY);
|
||
}
|
||
|
||
/* Notify another plugins that the theme mode has changed */
|
||
notify() {
|
||
window.postMessage(
|
||
{
|
||
direction: ModeToggle.ID,
|
||
message: this.modeStatus
|
||
},
|
||
'*'
|
||
);
|
||
}
|
||
|
||
flipMode() {
|
||
if (this.hasMode) {
|
||
if (this.isSysDarkPrefer) {
|
||
if (this.isLightMode) {
|
||
this.clearMode();
|
||
} else {
|
||
this.setLight();
|
||
}
|
||
} else {
|
||
if (this.isDarkMode) {
|
||
this.clearMode();
|
||
} else {
|
||
this.setDark();
|
||
}
|
||
}
|
||
} else {
|
||
if (this.isSysDarkPrefer) {
|
||
this.setLight();
|
||
} else {
|
||
this.setDark();
|
||
}
|
||
}
|
||
|
||
this.notify();
|
||
} /* flipMode() */
|
||
} /* ModeToggle */
|
||
|
||
const modeToggle = new ModeToggle();
|
||
</script>
|
||
|
||
|
||
|
||
<!-- A placeholder to allow defining custom metadata -->
|
||
|
||
</head>
|
||
|
||
|
||
<body>
|
||
<!-- The Side Bar -->
|
||
|
||
<div id="sidebar" class="d-flex flex-column align-items-end">
|
||
<div class="profile-wrapper">
|
||
<a href="/" id="avatar" class="rounded-circle">
|
||
|
||
</a>
|
||
|
||
<div class="site-title">
|
||
<a href="/">neo's brain</a>
|
||
</div>
|
||
<div class="site-subtitle fst-italic">just a bunch of technical write ups and notes.</div>
|
||
</div>
|
||
<!-- .profile-wrapper -->
|
||
|
||
<ul class="nav flex-column flex-grow-1 w-100 ps-0">
|
||
<!-- home -->
|
||
<li class="nav-item">
|
||
<a href="/" class="nav-link">
|
||
<i class="fa-fw fas fa-home"></i>
|
||
<span>HOME</span>
|
||
</a>
|
||
</li>
|
||
<!-- the real tabs -->
|
||
|
||
<li class="nav-item">
|
||
<a href="/categories/" class="nav-link">
|
||
<i class="fa-fw fas fa-stream"></i>
|
||
|
||
|
||
<span>CATEGORIES</span>
|
||
</a>
|
||
</li>
|
||
<!-- .nav-item -->
|
||
|
||
<li class="nav-item">
|
||
<a href="/tags/" class="nav-link">
|
||
<i class="fa-fw fas fa-tags"></i>
|
||
|
||
|
||
<span>TAGS</span>
|
||
</a>
|
||
</li>
|
||
<!-- .nav-item -->
|
||
|
||
<li class="nav-item">
|
||
<a href="/archives/" class="nav-link">
|
||
<i class="fa-fw fas fa-archive"></i>
|
||
|
||
|
||
<span>ARCHIVES</span>
|
||
</a>
|
||
</li>
|
||
<!-- .nav-item -->
|
||
|
||
<li class="nav-item">
|
||
<a href="/about/" class="nav-link">
|
||
<i class="fa-fw fas fa-info-circle"></i>
|
||
|
||
|
||
<span>ABOUT</span>
|
||
</a>
|
||
</li>
|
||
<!-- .nav-item -->
|
||
|
||
</ul>
|
||
<!-- ul.nav.flex-column -->
|
||
|
||
<div class="sidebar-bottom d-flex flex-wrap align-items-center w-100">
|
||
|
||
<button class="mode-toggle btn" aria-label="Switch Mode">
|
||
<i class="fas fa-adjust"></i>
|
||
</button>
|
||
|
||
|
||
<span class="icon-border"></span>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<a
|
||
href="https://github.com/ericlikedis"
|
||
aria-label="github"
|
||
|
||
|
||
|
||
target="_blank"
|
||
|
||
|
||
|
||
|
||
|
||
|
||
rel="noopener noreferrer"
|
||
|
||
>
|
||
<i class="fab fa-github"></i>
|
||
</a>
|
||
|
||
|
||
|
||
|
||
|
||
<a
|
||
href="https://twitter.com/"
|
||
aria-label="twitter"
|
||
|
||
|
||
|
||
target="_blank"
|
||
|
||
|
||
|
||
|
||
|
||
|
||
rel="noopener noreferrer"
|
||
|
||
>
|
||
<i class="fab fa-twitter"></i>
|
||
</a>
|
||
|
||
|
||
|
||
|
||
|
||
<a
|
||
href="javascript:location.href = 'mailto:' + ['ereymundo2013','gmail.com'].join('@')"
|
||
aria-label="email"
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
>
|
||
<i class="fas fa-envelope"></i>
|
||
</a>
|
||
|
||
|
||
|
||
|
||
|
||
<a
|
||
href="/feed.xml"
|
||
aria-label="rss"
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
>
|
||
<i class="fas fa-rss"></i>
|
||
</a>
|
||
|
||
|
||
</div>
|
||
<!-- .sidebar-bottom -->
|
||
</div>
|
||
<!-- #sidebar -->
|
||
|
||
|
||
<div id="main-wrapper" class="d-flex justify-content-center">
|
||
<div id="main" class="container px-xxl-5">
|
||
<!-- The Top Bar -->
|
||
|
||
<div id="topbar-wrapper">
|
||
<div
|
||
id="topbar"
|
||
class="container d-flex align-items-center justify-content-between h-100"
|
||
>
|
||
<span id="breadcrumb">
|
||
|
||
|
||
|
||
|
||
|
||
<span>
|
||
<a href="/">
|
||
Home
|
||
</a>
|
||
</span>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<span>Building a Custom Malware Analysis Lab Enviornment</span>
|
||
|
||
|
||
|
||
|
||
|
||
</span>
|
||
<!-- endof #breadcrumb -->
|
||
|
||
<i id="sidebar-trigger" class="fas fa-bars fa-fw"></i>
|
||
|
||
<div id="topbar-title">
|
||
Post
|
||
</div>
|
||
|
||
<i id="search-trigger" class="fas fa-search fa-fw"></i>
|
||
<span id="search-wrapper" class="align-items-center">
|
||
<i class="fas fa-search fa-fw"></i>
|
||
<input
|
||
class="form-control"
|
||
id="search-input"
|
||
type="search"
|
||
aria-label="search"
|
||
autocomplete="off"
|
||
placeholder="Search..."
|
||
>
|
||
</span>
|
||
<span id="search-cancel">Cancel</span>
|
||
</div>
|
||
</div>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<div class="row">
|
||
<!-- core -->
|
||
<div id="core-wrapper" class="col-12 col-lg-11 col-xl-9 pe-xl-4">
|
||
|
||
|
||
<div class="post px-1 px-md-2">
|
||
|
||
|
||
|
||
|
||
|
||
<!-- Refactor the HTML structure -->
|
||
|
||
|
||
|
||
<!--
|
||
In order to allow a wide table to scroll horizontally,
|
||
we suround the markdown table with `<div class="table-wrapper">` and `</div>`
|
||
-->
|
||
|
||
|
||
|
||
<!--
|
||
Fixed kramdown code highlight rendering:
|
||
https://github.com/penibelst/jekyll-compress-html/issues/101
|
||
https://github.com/penibelst/jekyll-compress-html/issues/71#issuecomment-188144901
|
||
-->
|
||
|
||
|
||
|
||
<!-- Change the icon of checkbox -->
|
||
|
||
|
||
<!-- images -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- CDN URL -->
|
||
|
||
|
||
<!-- Add image path -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- take out classes -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- lazy-load images <https://github.com/aFarkas/lazysizes#readme> -->
|
||
|
||
|
||
|
||
<!-- add image placeholder -->
|
||
|
||
|
||
|
||
|
||
<!-- Bypass the HTML-proofer test -->
|
||
|
||
|
||
|
||
<!-- make sure the `<img>` is wrapped by `<a>` -->
|
||
|
||
|
||
|
||
<!-- create the image wrapper -->
|
||
|
||
|
||
|
||
|
||
<!-- combine -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- Add header for code snippets -->
|
||
|
||
|
||
|
||
<!-- Create heading anchors -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- return -->
|
||
|
||
|
||
|
||
|
||
<h1 data-toc-skip>Building a Custom Malware Analysis Lab Enviornment</h1>
|
||
|
||
<div class="post-meta text-muted">
|
||
<!-- published date -->
|
||
<span>
|
||
Posted
|
||
<!--
|
||
Date format snippet
|
||
See: ${JS_ROOT}/utils/locale-dateime.js
|
||
-->
|
||
|
||
|
||
|
||
|
||
|
||
<em
|
||
class=""
|
||
data-ts="1692822826"
|
||
data-df="ll"
|
||
|
||
data-bs-toggle="tooltip" data-bs-placement="bottom"
|
||
|
||
>
|
||
Aug 23, 2023
|
||
</em>
|
||
|
||
</span>
|
||
|
||
<!-- lastmod date -->
|
||
|
||
<span>
|
||
Updated
|
||
<!--
|
||
Date format snippet
|
||
See: ${JS_ROOT}/utils/locale-dateime.js
|
||
-->
|
||
|
||
|
||
|
||
|
||
|
||
<em
|
||
class=""
|
||
data-ts="1692823049"
|
||
data-df="ll"
|
||
|
||
data-bs-toggle="tooltip" data-bs-placement="bottom"
|
||
|
||
>
|
||
Aug 23, 2023
|
||
</em>
|
||
|
||
</span>
|
||
|
||
|
||
|
||
|
||
<div class="d-flex justify-content-between">
|
||
<!-- author(s) -->
|
||
<span>
|
||
|
||
|
||
By
|
||
|
||
<em>
|
||
|
||
<a href="https://github.com/username">Eric Reymundo</a>
|
||
|
||
</em>
|
||
</span>
|
||
|
||
<div>
|
||
<!-- read time -->
|
||
<!-- Calculate the post's reading time, and display the word count in tooltip -->
|
||
|
||
|
||
|
||
<!-- words per minute -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- return element -->
|
||
<span
|
||
class="readtime"
|
||
data-bs-toggle="tooltip"
|
||
data-bs-placement="bottom"
|
||
title="2924 words"
|
||
>
|
||
<em>16 min</em> read</span>
|
||
|
||
</div>
|
||
|
||
</div> <!-- .d-flex -->
|
||
|
||
</div> <!-- .post-meta -->
|
||
|
||
<div class="post-content">
|
||
<pre><code class="language-ad-note">https://www.sentinelone.com/labs/building-a-custom-malware-analysis-lab-environment/
|
||
</code></pre>
|
||
|
||
<h2 id="introduction"><span class="me-2">Introduction</span><a href="#introduction" class="anchor text-muted"><i class="fas fa-hashtag"></i></a></h2>
|
||
|
||
<p>Building the right <a href="https://www.sentinelone.com/cybersecurity-101/malware-analysis/">malware analysis</a> environment is the first step for every malware researcher. When all system configurations and software installations are complete, you’re able to analyze and investigate malware properly. In this post, I wanted to share my own experiences and scripts to help ease the workload of setting up a malware environment to explore malicious software.</p>
|
||
|
||
<p>In this post, you will learn how to:</p>
|
||
|
||
<ol>
|
||
<li>download, install and configure a free Windows 10 and a free REMnux Linux virtual machine</li>
|
||
<li>set up a virtual private network for communication between virtual machines</li>
|
||
<li>build a custom Windows malware environment with SentinelLabs RevCore Tools</li>
|
||
<li>learn how to capture network traffic from a Windows 10 virtual machine</li>
|
||
</ol>
|
||
|
||
<h2 id="installing-virtual-machines"><span class="me-2">Installing Virtual Machines</span><a href="#installing-virtual-machines" class="anchor text-muted"><i class="fas fa-hashtag"></i></a></h2>
|
||
|
||
<p>When running multiple virtual machines, the host operating system will begin slowing down, so it is critical to set each virtual machine’s best requirements to optimize its performance. To set up the virtual machines in this post, I recommend that the Windows 10 virtual machine be set with the minimum requirements of two processor cores with 4GB of RAM and the Linux virtual machine with two processor cores with 2GB of RAM.</p>
|
||
|
||
<h2 id="downloading-a-free-windows-10-installation"><span class="me-2">Downloading a Free Windows 10 Installation</span><a href="#downloading-a-free-windows-10-installation" class="anchor text-muted"><i class="fas fa-hashtag"></i></a></h2>
|
||
|
||
<p>Microsoft provides a free virtual machine which is intended for testing IE and Edge web browsers. To download the Microsoft virtual machine go to <a href="https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/">https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/</a> and download the MSEdge on Windows 10 zip file and select your preferred VM platform, currently I’m using VM Fusion.</p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/1.-MSEdge-VM.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/1.-MSEdge-VM.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<h2 id="downloading-remnux-linux"><span class="me-2">Downloading REMnux Linux</span><a href="#downloading-remnux-linux" class="anchor text-muted"><i class="fas fa-hashtag"></i></a></h2>
|
||
|
||
<p>The next virtual machine we want to download is REMnux Linux. The REMnux distro is a Linux distribution based on Ubuntu. It has excellent tools for exploring network interactions for behavioral analysis and investigating system-level interactions of malware. To download REMnux go to <a href="https://docs.remnux.org/install-distro/get-virtual-appliance">https://docs.remnux.org/install-distro/get-virtual-appliance</a> and download the Virtual Machine platform of your choice.</p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/2.-Download-REMNux.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/2.-Download-REMNux.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<h2 id="installing-and-configuring-a-private-isolated-custom-network"><span class="me-2">Installing and Configuring a Private Isolated Custom Network</span><a href="#installing-and-configuring-a-private-isolated-custom-network" class="anchor text-muted"><i class="fas fa-hashtag"></i></a></h2>
|
||
|
||
<p>Creating an isolated, controlled network environment when analyzing malware is extremely important due to the level of interaction it gives you with malware. VMware Fusion gives you the capabilities to change key networking settings and add a virtual private network configuration to use for analysis between hosts. We will only add two virtual machines to this lab environment, but you can add many virtual machines to this network. The procedures to create this network is as follows:</p>
|
||
|
||
<ul>
|
||
<li>Select the tab <strong>VMware Fusion->Preferences->Network</strong>; click the lock icon to make changes</li>
|
||
<li>Select the “<strong>+</strong>” button which creates a <code class="language-plaintext highlighter-rouge">vmnet#</code> under the <strong>Custom</strong> section.</li>
|
||
<li>Do <strong><em>not</em></strong> select the <em>“Allow Virtual machines on this network to connect to external networks (using NAT)”</em> option.</li>
|
||
<li>Add a <em>Subnet IP</em>: I’ve entered <code class="language-plaintext highlighter-rouge">10.1.2.0</code></li>
|
||
<li>Click <strong>Apply</strong></li>
|
||
</ul>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/3.-VMware-Network-settings.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/3.-VMware-Network-settings.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<h2 id="windows-10-setup"><span class="me-2">Windows 10 Setup</span><a href="#windows-10-setup" class="anchor text-muted"><i class="fas fa-hashtag"></i></a></h2>
|
||
|
||
<p>Once you’ve created a custom network and both virtual machines have been downloaded, begin by unzipping the MSEdge Windows 10. Since I’m using VMware Fusion, I will go through how to import the virtual image; the process for importing the virtual machine with other platforms is similar.</p>
|
||
|
||
<p>Open up VMware Fusion and follow these steps:</p>
|
||
|
||
<ol>
|
||
<li>After the zip has been unpacked enter the MSEdge-Win10-VMware folder.</li>
|
||
<li>Select in VMware Fusion <strong>File->Import MSEdge_Win10_VMware</strong>, hit <strong>Continue</strong> and save the Virtual Machine; it will take a few minutes to import the image.</li>
|
||
<li>Click on <strong>Customize Settings</strong> after the image has been imported.</li>
|
||
<li>Click into the <strong>Processors & Memory</strong> tab and confirm that the settings has two processor cores and the memory is 4096MB.</li>
|
||
<li>Before powering on the MSEdge Win10 virtual machine, take a snapshot and name it something like “VM Clean Import”.</li>
|
||
<li>When starting the virtual machine, if prompted to upgrade the virtual machine to greater feature compatibility support, choose <strong>Upgrade</strong>.</li>
|
||
<li>The password to the virtual machine is <code class="language-plaintext highlighter-rouge">Passw0rd!</code></li>
|
||
<li>Open the command prompt to activate the virtual machine, type <code class="language-plaintext highlighter-rouge">slmgr.vbs /ato</code>.</li>
|
||
<li>When prompted, install VMware’s “Virtual Tools” and reboot.</li>
|
||
<li>Once the virtual machine has rebooted, complete login and immediately take a snapshot. Give it a descriptive name, such as “Activation and VM Tools Install” snapshot.</li>
|
||
</ol>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/4.-VMware-memory-settings.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/4.-VMware-memory-settings.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<h2 id="remnux-setup"><span class="me-2">REMnux Setup</span><a href="#remnux-setup" class="anchor text-muted"><i class="fas fa-hashtag"></i></a></h2>
|
||
|
||
<p>The REMnux virtual machine downloads as an <code class="language-plaintext highlighter-rouge">.ova</code> file. I recommend you browse to <a href="https://docs.remnux.org/install-distro/get-virtual-appliance">docs.REMnux.org</a> to confirm the hash of the downloaded OVA file.</p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/5.-check-the-hash.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/5.-check-the-hash.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>If you are using VirtualBox, you can just import REMnux, but if you are using VMware Fusion or VMware Workstation, follow these instructions to import the REMnux:</p>
|
||
|
||
<ol>
|
||
<li>Select <strong>File->Import->Choose File…</strong> and select <em>remnux-v7</em>, hit <strong>Continue</strong> and then <strong>Save</strong>.</li>
|
||
<li>When the import is complete, click on <strong>Customize Settings</strong>.</li>
|
||
<li>Click into the <strong>Processors & Memory</strong> pane under <em>System Settings</em> and leave the settings with two processor cores; reduce the memory from 4096MB to 2048MB.</li>
|
||
<li>For the REMnux network configuration, the setup is slightly different. We want to add an additional network adapter.<em>Note</em>: There are multiple reasons why I configure this virtual machine this way. If I need to update or download other software having the network adapter configured saves me time; the second is if I want to allow malware callouts.Once the import is complete and you’re in the “Settings” menu, select <strong>Network Adapter</strong>. The next step is to click <strong>Add Device…</strong> and select <strong>Network Adapter</strong> and <strong>Add…</strong>. Make sure the <em>Share with my Mac</em> radio button is set. Return to the main “Settings” panel and select <strong>Network Adapter 2</strong>. Click the <em>vmnet2</em> radio button, then choose <strong>Show All</strong> to go back to Settings.</li>
|
||
<li>When starting the REMnux virtual machine, if prompted to upgrade the virtual machine to greater feature compatibility support, choose <strong>Upgrade</strong>.</li>
|
||
<li>Once REMnux boots, the credentials are: Username: <code class="language-plaintext highlighter-rouge">remnux</code> Password: <code class="language-plaintext highlighter-rouge">malware</code>.</li>
|
||
<li>I always change the password on my virtual machines:
|
||
<ol>
|
||
<li>$passwd
|
||
UNIX password: malware
|
||
Enter new UNIX password: (your choice)</li>
|
||
</ol>
|
||
</li>
|
||
<li>The next step is to configure the network settings. If you type <code class="language-plaintext highlighter-rouge">ifconfig -a</code> you should see two network adapters:
|
||
<ol>
|
||
<li>Select NAT for the first network adapter. The virtual machine will get an address on that network from the VMware virtual DHCP server. You can ping google to see if you have connectivity or open the Firefox browser and connect to any website to confirm that you have internet access. If you do not, then type this command in terminal: <code class="language-plaintext highlighter-rouge">$ sudo dhclient -r</code> This should allow you to fetch an IP.</li>
|
||
<li>For the second adapter, ens37, type in this command:<code class="language-plaintext highlighter-rouge">$ sudo ifconfig ens37 10.1.2.1 netmask 255.255.255.0</code><a href="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/7.-ifconfig.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/7.-ifconfig.jpg" alt="" class="lazyload" data-proofer-ignore></a></li>
|
||
</ol>
|
||
</li>
|
||
<li>Hit the “Snapshot” button and name it something like “Clean Snapshot”.</li>
|
||
<li>Update and upgrade REMnux:<code class="language-plaintext highlighter-rouge">$ sudo apt-get update; sudo apt-get upgrade</code></li>
|
||
</ol>
|
||
|
||
<h2 id="installing-sentinellabs-revcore-tools"><span class="me-2">Installing SentinelLabs RevCore Tools</span><a href="#installing-sentinellabs-revcore-tools" class="anchor text-muted"><i class="fas fa-hashtag"></i></a></h2>
|
||
|
||
<p>One of the reasons I wanted to create a SentinelLabs VM Bare Bones malware analysis toolkit was that when installing FlareVM, I find it contains many tools that I do not use, and it takes a minimum of 40 minutes to install. I wanted to create a script of the core tools and system configurations that I need to be able to analyze malware.</p>
|
||
|
||
<p>Follow this procedure to instal SentinelLabs RevCore Tools on MSEdge WIndows 10:</p>
|
||
|
||
<ol>
|
||
<li>Browse to the <a href="https://github.com/SentineLabs/SentinelLabs_RevCore_Tools">SentinelLabs RevCore Tools</a> github page and download the zip.</li>
|
||
<li>Unzip it and drag the <code class="language-plaintext highlighter-rouge">SentinelLabs_RevCore_Tools_codeSnippet.ps1</code> script onto your desktop.</li>
|
||
<li>If you are using the free downloaded Windows 10 virtual machine that I’ve mentioned above go to Step 4; if you are using your own Windows virtual machine continue with these substeps:
|
||
<ol>
|
||
<li>Instead of dragging just the <code class="language-plaintext highlighter-rouge">SentinelLabs_RevCore_Tools_codeSnippet.ps1</code>, drag the entire folder onto your virtual machine desktop.</li>
|
||
<li>Open the <code class="language-plaintext highlighter-rouge">SentinelLabs_RevCore_Tools_codeSnpippet.ps1</code> file and modify line 4 after <code class="language-plaintext highlighter-rouge">-PackageName.</code> You will modify the url and change it to the directory location on your desktop. E.g., <code class="language-plaintext highlighter-rouge">'https://raw.githubusercontent.com/SentineLabs/SentinelLabs_RevCore_Tools/master/SentinelLabs_RevCore_Tools.ps1'</code> to <code class="language-plaintext highlighter-rouge">'c:UsersyourUsernameDesktopSentinelLabs_RevCore_Tools-mainSentinelLabRevCoreTools.ps1'</code><code class="language-plaintext highlighter-rouge">;</code></li>
|
||
<li>
|
||
<p>The final thing to do is to modify the <code class="language-plaintext highlighter-rouge">SentinelLabsRevCoreTools.ps1.</code> On lines 105-117, replace <code class="language-plaintext highlighter-rouge">IEUser</code> with the User profiles name you are using. Save all files and run the script. E.g.,</p>
|
||
|
||
<p>Install-ChocolateyShortcut -ShortcutFilePath “C:\Users\IEUser\Desktop\HxD.lnk” -TargetPath “C:\Program Files\HxD\HxD.exe”</p>
|
||
|
||
<p>Install-ChocolateyShortcut -ShortcutFilePath “C:\Users\YourUser Profile\Desktop\HxD.lnk” -TargetPath “C:\Program Files\HxD\HxD.exe”</p>
|
||
</li>
|
||
<li>Go to Step 5.</li>
|
||
</ol>
|
||
</li>
|
||
<li>In the Windows 10 search bar, type <code class="language-plaintext highlighter-rouge">powershell</code>, right click and run as administrator. Browse to the location of the <code class="language-plaintext highlighter-rouge">SentinelLabs_RevCore_Tools_codeSnippet.ps1</code> powershell script, then run the script:<br />
|
||
<code class="language-plaintext highlighter-rouge">.SentinelLabs_RevCore_Tools_codeSnippet.ps1</code>.</li>
|
||
<li>
|
||
<p>The script will cause two automatic reboots, and you’ll need to log in again with your user password after each. The first reboot will continue disabling various system services that could otherwise hinder your malware analysis and continue to install the core tools. After the second reboot, the script will finalize and confirm all of the configurations and installations.The installed tools and modified system configurations are listed below. Don’t forget to take a snapshot when it’s finished and you’ve reached the “Type ENTER to exit” point.</p>
|
||
|
||
<ol>
|
||
<li><strong>Tools:</strong><br />
|
||
Checksum, 7zip, Process Explorer, Autoruns, TCPview, Sysmon, HxD, PEbear, PEStudio, PEsieve, Cmder, NXlog, X64dbg, X32dbg, Ollydbg, IDA-Free, Cutter, Ghidra, Openjdk11, Python3, PIP, PIP pefile, PIP YaraA tool that I frequently use is <a href="http://www.hiew.ru/">Hiew</a>, Chocolatey does not have Hiew in its collection. My recommendation is to download and try out the free version, once you see the power of Hiew you should definitely purchase lifetime access because it is worth every penny.</li>
|
||
<li><strong>System Configuration:</strong><br />
|
||
Disabling – Bing Search, Game Bar Tips, Computer Restore, UAC, Update, Firewall, Windows Defender, Action Center<br />
|
||
Set Window Theme, Set Wallpaper, Create Shortcuts For Tools</li>
|
||
</ol>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/8.-script-running.gif" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/labs/2020/12/8.-script-running.gif" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/9.-wallpaper-1024x889.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/9.-wallpaper-1024x889.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>## Network Traffic Collection</p>
|
||
|
||
<p>When analyzing malware, often the malware operation and the C2s are still active, so an excellent way to stay under the radar is to run malware in a controlled environment. Analyzing network traffic is a trivial process in detecting malicious software callouts in real time network traffic. This section will help you configure your virtual machines to capture the detonated malicious software’s network traffic or statically step through debugged code, which allows your investigation to understand the potential threat at hand.</p>
|
||
|
||
<p>The first thing that must be configured is the virtual private network communication between the MSEdge Windows 10 and REMnux:</p>
|
||
|
||
<ol>
|
||
<li>On the Windows 10 virtual machine, select the custom <code class="language-plaintext highlighter-rouge">vmnet2</code> network (<strong>Virtual Machine->Network Adapter->Custom (vmnet2)</strong>).</li>
|
||
<li>On the Windows 10 VM, right click on the network adapter in the taskbar and choose <em>Open Network & Internet settings</em>.</li>
|
||
<li>Select <em>Ethernet</em> and click on <strong>Change adapter options</strong>.</li>
|
||
<li>Right click on <em>Ethernet0</em> and select <strong>Properties</strong>.</li>
|
||
<li>Double click on <em>Internet Protocol Version 4 (TCP/IPv4)</em>.</li>
|
||
<li>Click the radio button to select “<em>Use the following IP address:</em>”, then add the IP address, Subnet mask, Default gateway, and Preferred DNS server as follows:
|
||
<ol>
|
||
<li>IP Address: 10.1.2.100</li>
|
||
<li>Subnet mask: 255.255.255.0</li>
|
||
<li>Default Gateway: 10.1.2.1</li>
|
||
<li>Click the radio button to select <em>“Use the following DNS server address:”</em> and add:
|
||
<ul>
|
||
<li>Preferred DNS Server: 10.1.2.1</li>
|
||
</ul>
|
||
</li>
|
||
<li>Click <strong>OK</strong> to complete configuration of the network settings.</li>
|
||
</ol>
|
||
</li>
|
||
</ol>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/10.-Win-10-network-settings-1024x799.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/10.-Win-10-network-settings-1024x799.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>The REMnux adapter for the virtual private network has already been configured from the previous section.</p>
|
||
|
||
<p>Now that the virtual machines are networked and can communicate with each other, it is time to configure a few tools on the REMnux virtual machine to capture traffic.</p>
|
||
|
||
<p>Installed on REMnux are various tools you can use to capture network traffic. We will configure Burp Suite and INetSim. Burp Suite is typically used to test web application firewalls, but in our case we want to configure it so that when Windows 10 detonates malware, it will try to establish a connection to a domain or C2. The traffic will potentially use HTTPS and pass through Burp Suite, which will be bound to INetSim. INetSim is a software suite that simulates common services for lab environments to analyze malware’s network behavior.</p>
|
||
|
||
<p>## Burp Suite Configuration</p>
|
||
|
||
<p>The Burp Suite setup is straightforward, but there are a couple of steps that we must configure before we can begin using it.</p>
|
||
|
||
<ul>
|
||
<li>Open a command prompt and type: <code class="language-plaintext highlighter-rouge">$ sudo Burp Suite</code>.</li>
|
||
<li>select <em>Temporary project</em>, then hit <strong>Next</strong> and then <strong>Start Burp</strong>.</li>
|
||
<li>Select the <strong>Proxy</strong> tab and then “Options”. Under <em>Proxy Listeners</em>, select the default interface and click the <strong>Edit</strong> button.</li>
|
||
<li>Under the <strong>Binding</strong> tab, set <em>Bind to address</em> to <em>Specific address: 10.1.2.1</em> and click <strong>OK</strong>.</li>
|
||
</ul>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/11.-setting-up-burp-suite-790x1024.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/11.-setting-up-burp-suite-790x1024.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<ul>
|
||
<li>IMPORTANT STEP:
|
||
<ul>
|
||
<li>Go back to you MSEDGE Windows 10 virtual machine and open up the Edge browser.</li>
|
||
<li>Type in the address bar: <a href="http://10.1.2.1:8080/"><code class="language-plaintext highlighter-rouge">http://10.1.2.1:8080</code></a>. You should see “Burp Suite Community Edition”.</li>
|
||
<li>Download the CA Certificate on the top right side of the page.</li>
|
||
<li>Open the location of the file and double click on the certificate file.</li>
|
||
<li>Select <code class="language-plaintext highlighter-rouge">Install Certificate...</code>.</li>
|
||
<li>Select <code class="language-plaintext highlighter-rouge">Current User</code> as the Store Location and click <code class="language-plaintext highlighter-rouge">Next</code>.</li>
|
||
<li>Select <code class="language-plaintext highlighter-rouge">Automatically select the certificate store based on the type of certificate</code>. Click <code class="language-plaintext highlighter-rouge">Next</code> and then click <code class="language-plaintext highlighter-rouge">Finish</code>.</li>
|
||
<li>Go into the settings of the EDGE Browser and disable all security functionalities; this will help with testing the connection to INetSim in the next section.</li>
|
||
<li>Make sure you take a snapshot.</li>
|
||
</ul>
|
||
</li>
|
||
</ul>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/12.-Import-BS-Cert-1024x796.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/12.-Import-BS-Cert-1024x796.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>Go back to the REMnux virtual machine. You should still be in Burp Suite Proxy tab, <em>Edit proxy listener</em> options.</p>
|
||
|
||
<ul>
|
||
<li>Under the <strong>Request handling</strong> tab, set <em>Redirect to host</em> to <code class="language-plaintext highlighter-rouge">localhost</code> and <em>Redirect to port</em> to <code class="language-plaintext highlighter-rouge">4443</code>. Select <em>support for invisible proxying</em>.</li>
|
||
<li>Now go to the <strong>Intercept</strong> tab and make sure <em>intercept</em> is <strong>off</strong>.</li>
|
||
<li>Under <strong>Proxy Listeners</strong>, select the default and click <code class="language-plaintext highlighter-rouge">Edit</code></li>
|
||
<li>Under the Binding tab, <code class="language-plaintext highlighter-rouge">Bind to address: Specific address: 10.1.2.1</code> should still be kept, but change the <em>Bind</em> to port <code class="language-plaintext highlighter-rouge">443</code></li>
|
||
<li>Click on the <strong>Request handling</strong> tab and set the <em>Redirect to host</em> option to <code class="language-plaintext highlighter-rouge">localhost</code> and <code class="language-plaintext highlighter-rouge">Redirect to port</code> to <code class="language-plaintext highlighter-rouge">4443.</code></li>
|
||
<li>Select the <em>Support invisible proxying (enable only if needed.)</em> and click <strong>OK</strong>.</li>
|
||
</ul>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/13.-Edit-Proxy-Listener-1024x506.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/13.-Edit-Proxy-Listener-1024x506.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>## INetSim Configuration Setup</p>
|
||
|
||
<p>REMnux has INetSim preinstalled. Use your favorite text editor and open up the <code class="language-plaintext highlighter-rouge">inetsim.conf</code> file located in <code class="language-plaintext highlighter-rouge">/etc/inetsim/</code>. Follow the steps to configure INetSim:</p>
|
||
|
||
<ol>
|
||
<li><code class="language-plaintext highlighter-rouge">$ sudo vi /etc/inetsim/inetsim.conf</code> and enable all the services by uncommenting out the services by deleting the <code class="language-plaintext highlighter-rouge">#</code> character.<em>Pro Tip:</em> Be aware that malware could potentially detect it is running in a virtual environment by checking whether everything in this file is uncommented. I have yet to come across this, but it is good to be aware of the possibility. You could take a more conservative approach and only uncomment services you intend to use.<a href="https://www.sentinelone.com/wp-content/uploads/2021/01/14.-Edit-Inet-config-1024x780.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/14.-Edit-Inet-config-1024x780.jpg" alt="" class="lazyload" data-proofer-ignore></a></li>
|
||
<li>The next step is to bind the REMnux network adapter IP in the <code class="language-plaintext highlighter-rouge">inetsim.conf</code> file. The next section after the services menu is the <code class="language-plaintext highlighter-rouge">service_bind_address</code>. Uncomment the <code class="language-plaintext highlighter-rouge">#</code> and change the default IP address from 10.10.10.1 to <code class="language-plaintext highlighter-rouge">0.0.0.0</code>.</li>
|
||
<li>Scroll down to the <code class="language-plaintext highlighter-rouge">dns_default_ip</code> section, uncomment the <code class="language-plaintext highlighter-rouge">#</code> and change the IP address from 10.10.10.1 to <code class="language-plaintext highlighter-rouge">10.1.2.1</code>.</li>
|
||
<li>The last thing to do is to bind the HTTPS port so Burp Suite can route the traffic to the port 4443. Scroll down to the <code class="language-plaintext highlighter-rouge">https_bind_port</code> section, uncomment the <code class="language-plaintext highlighter-rouge">#</code> character and replace 443 with <code class="language-plaintext highlighter-rouge">4443</code>.</li>
|
||
<li>Save the changes and exit the editor.<a href="https://www.sentinelone.com/wp-content/uploads/2021/01/15.-Service-bind-address.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/15.-Service-bind-address.jpg" alt="" class="lazyload" data-proofer-ignore></a></li>
|
||
<li>
|
||
<p>The next step is to run the following commands which are VERY IMPORTANT to execute or INetSim will not work correctly. Ubuntu has a system-resolved system service which provides network name resolution to local applications. This conflicts with INetSim so we need to disable the service.We have to disable <code class="language-plaintext highlighter-rouge">system-resolve</code> and also mask it so that it doesn’t auto start on reboot. Finally, we will stop the service.</p>
|
||
|
||
<p>$ sudo systemctl disable systemd-resolved
|
||
$ sudo systemctl mask systemd-resolved
|
||
$ sudo systemctl stop systemd-resolved</p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/16.-systemctl.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/16.-systemctl.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
</li>
|
||
<li>The final step is to run INetSim:<br />
|
||
<code class="language-plaintext highlighter-rouge">$ sudo inetsim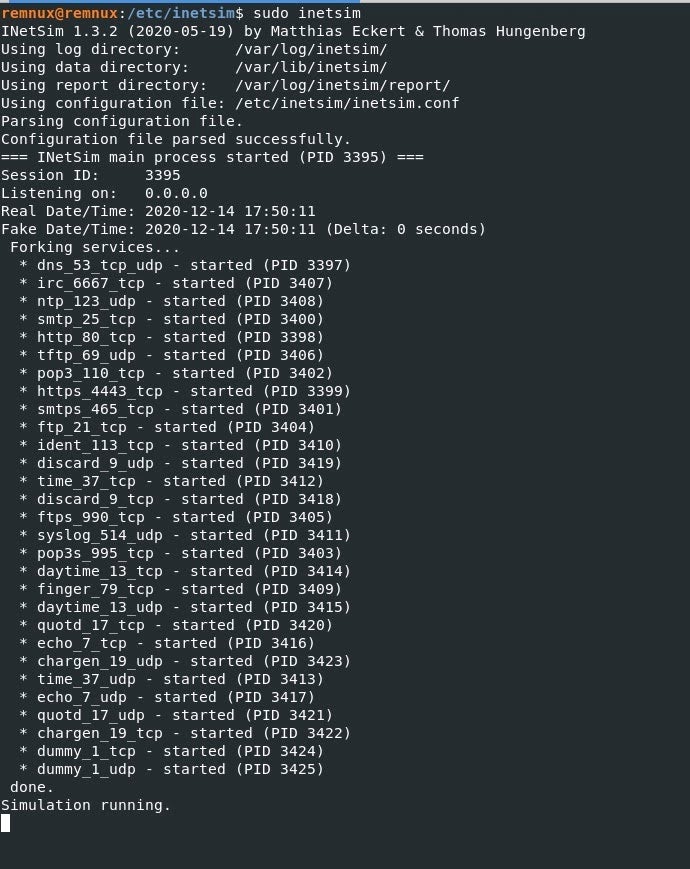</code></li>
|
||
</ol>
|
||
|
||
<p>To test network connectivity from your Windows 10 virtual machine, open a command prompt and ping 10.1.2.1, then open Edge browser and type 10.1.2.1. You should see the following message “<em>This is the default HTML page for INetSim HTTP server fake mode.</em>”</p>
|
||
|
||
<p>The final test is to make sure the DNS is working correctly and serving up requests. For this example, I type in the search bar <code class="language-plaintext highlighter-rouge">https://www.mymaliciousdomain.com/malwaretrojan.exe</code>. If everything is working, you should see a web page warning that the requested site is not secure.</p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/18.-ping-test-1009x1024.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/18.-ping-test-1009x1024.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>I also like using Wireshark to capture packets to analyze the pcaps when investigating malware.</p>
|
||
|
||
<p>Open a new tab in your terminal in REMnux and type <code class="language-plaintext highlighter-rouge">$ wireshark</code>.</p>
|
||
|
||
<p>Once the application has opened, click on the shark fin icon on the far left of the toolbar to begin capturing packets.</p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/19.-wireshark.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/19.-wireshark.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>## Detonating Malware</p>
|
||
|
||
<p>When malware is executed, it usually makes some request to a domain or IP address. INetSim helps with this by spoofing the responses to the malware that is waiting for a response. An example would be if malware was executed and reached out to a domain and will not proceed without a response unless the conditions were met, which is the response. If the malware doesn’t receive the response, it would terminate and not continue its malicious actions. This is where the live environment assists us with responding to callouts and capturing network traffic.</p>
|
||
|
||
<p>For the final step of the lab environment setup, we will detonate a notorious binary trojan (or any malware you choose) to test the configuration is working correctly.</p>
|
||
|
||
<p>I’m testing with a Trickbot binary (<strong>SHA256:</strong> <code class="language-plaintext highlighter-rouge">49d95cae096f7f73b3539568b450076227b4ca42c0240044a7588ddc1f1b6985</code>). I’ve opened Process Explorer and TCPView to monitor the execution of this variant of Trickbot.</p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/20.-trickbot-test-1024x581.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/20.-trickbot-test-1024x581.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/21.-trickbot-capture-1024x602.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/21.-trickbot-capture-1024x602.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>Detonating malware can save a lot of time before diving deep into reverse engineering as it allows you to gather insight and create an unbiased hypothesis. In this example, when we detonated this trickbot sample there were three callouts that stuck out:</p>
|
||
|
||
<ul>
|
||
<li>The callouts were to fetch files from Microsoft Updates site; these cab files called were automatic updaters of untrusted certificates. A certificate trust list is a predefined list of items signed by a trusted entity. These requested cab files are used to update and expand the existing functionality by adding known untrusted certificates to the untrusted certificate store by using a certificate trust list.</li>
|
||
</ul>
|
||
|
||
<p><a href="https://www.sentinelone.com/wp-content/uploads/2021/01/22.-malware-c2-activity-1024x441.jpg" class="popup img-link "><img data-src="https://www.sentinelone.com/wp-content/uploads/2021/01/22.-malware-c2-activity-1024x441.jpg" alt="" class="lazyload" data-proofer-ignore></a></p>
|
||
|
||
<p>Although Trickbot is one of the more prolific malware strains today and is more complex than a few callouts, it is a good starting point if you are in the beginning stages of research and have never encountered this binary.</p>
|
||
|
||
<p>I’ve been successfully using this lab setup for many years. A real-world example of using this lab setup occurred when I was brought in to help with an incident at short notice back in 2016. I didn’t have time for an initial triage of the binary as I was joining a war room call for the briefing by the investigation team lead. I started both VMs from snapshots and detonated the binary while being brought up to speed about the incident. Within 5 minutes, I informed the investigation lead about an IP that the specific binary was calling out to, which was enough to give the threat hunters a place to begin. After the war room call, I started reversing the malware and extracting additional IOCs and TTPs.</p>
|
||
|
||
<p>## Conclusion</p>
|
||
|
||
<p>A lab environment setup and configuration varies during malware analysis. When analyzing malware you need different tools to dissect and do deep analysis. I hope the SentinelLabs RevCore Tools and configurations in this setup assists, but there might be a time that you need to analyze something different, like a dot net file, and may need an additional tool to fully disassemble the binary. The journey of reversing malware is a marathon and not a sprint; growing your skill and learning from every malware analyzed should be the goal.</p>
|
||
|
||
<p>## Resources</p>
|
||
|
||
<p><a href="https://support.microsoft.com/en-us/help/2677070/an-automatic-updater-of-untrusted-certificates-is-available-for-window">https://support.microsoft.com/en-us/help/2677070/an-automatic-updater-of-untrusted-certificates-is-available-for-window</a></p>
|
||
|
||
<p><a href="https://askubuntu.com/questions/191226/dnsmasq-failed-to-create-listening-socket-for-port-53-address-already-in-use">https://askubuntu.com/questions/191226/dnsmasq-failed-to-create-listening-socket-for-port-53-address-already-in-use</a></p>
|
||
|
||
<p><a href="https://gallery.technet.microsoft.com/scriptcenter/Change-the-Desktop-b5b2141c">https://gallery.technet.microsoft.com/scriptcenter/Change-the-Desktop-b5b2141c</a></p>
|
||
|
||
<p><a href="https://gist.github.com/trietptm/b84ccad9db01f459ac7e">https://gist.github.com/trietptm/b84ccad9db01f459ac7e</a></p>
|
||
</li>
|
||
</ol>
|
||
|
||
<p>https://www.amazon.com/Building-Virtual-Machine-Labs-Hands/dp/1546932631</p>
|
||
|
||
|
||
</div>
|
||
|
||
<div class="post-tail-wrapper text-muted">
|
||
|
||
<!-- categories -->
|
||
|
||
|
||
<!-- tags -->
|
||
|
||
<div class="post-tags">
|
||
<i class="fa fa-tags fa-fw me-1"></i>
|
||
|
||
<a href="/tags/cybersecurity/"
|
||
class="post-tag no-text-decoration" >cybersecurity</a>
|
||
|
||
<a href="/tags/red-teaming/"
|
||
class="post-tag no-text-decoration" >Red Teaming</a>
|
||
|
||
</div>
|
||
|
||
|
||
<div class="post-tail-bottom
|
||
d-flex justify-content-between align-items-center mt-3 pt-5 pb-2">
|
||
<div class="license-wrapper">
|
||
|
||
|
||
|
||
|
||
|
||
This post is licensed under
|
||
<a href="https://creativecommons.org/licenses/by/4.0/">
|
||
CC BY 4.0
|
||
</a>
|
||
by the author.
|
||
|
||
|
||
</div>
|
||
|
||
<!-- Post sharing snippet -->
|
||
|
||
<div class="share-wrapper">
|
||
<span class="share-label text-muted me-1">Share</span>
|
||
<span class="share-icons">
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<a
|
||
href="https://twitter.com/intent/tweet?text=Building%20a%20Custom%20Malware%20Analysis%20Lab%20Enviornment%20-%20neo's%20brain&url=http%3A%2F%2Flocalhost%3A4000%2Fposts%2FBuilding-a-Custom-Malware-Analysis-Lab-Environment%2F"
|
||
data-bs-toggle="tooltip"
|
||
data-bs-placement="top"
|
||
title="Twitter"
|
||
target="_blank"
|
||
rel="noopener"
|
||
aria-label="Twitter"
|
||
>
|
||
<i class="fa-fw fab fa-twitter"></i>
|
||
</a>
|
||
|
||
|
||
<a
|
||
href="https://www.facebook.com/sharer/sharer.php?title=Building%20a%20Custom%20Malware%20Analysis%20Lab%20Enviornment%20-%20neo's%20brain&u=http%3A%2F%2Flocalhost%3A4000%2Fposts%2FBuilding-a-Custom-Malware-Analysis-Lab-Environment%2F"
|
||
data-bs-toggle="tooltip"
|
||
data-bs-placement="top"
|
||
title="Facebook"
|
||
target="_blank"
|
||
rel="noopener"
|
||
aria-label="Facebook"
|
||
>
|
||
<i class="fa-fw fab fa-facebook-square"></i>
|
||
</a>
|
||
|
||
|
||
<a
|
||
href="https://t.me/share/url?url=http%3A%2F%2Flocalhost%3A4000%2Fposts%2FBuilding-a-Custom-Malware-Analysis-Lab-Environment%2F&text=Building%20a%20Custom%20Malware%20Analysis%20Lab%20Enviornment%20-%20neo's%20brain"
|
||
data-bs-toggle="tooltip"
|
||
data-bs-placement="top"
|
||
title="Telegram"
|
||
target="_blank"
|
||
rel="noopener"
|
||
aria-label="Telegram"
|
||
>
|
||
<i class="fa-fw fab fa-telegram"></i>
|
||
</a>
|
||
|
||
|
||
<i
|
||
id="copy-link"
|
||
class="fa-fw fas fa-link small"
|
||
data-bs-toggle="tooltip"
|
||
data-bs-placement="top"
|
||
title="Copy link"
|
||
data-title-succeed="Link copied successfully!"
|
||
>
|
||
</i>
|
||
</span>
|
||
</div>
|
||
|
||
|
||
</div><!-- .post-tail-bottom -->
|
||
|
||
</div><!-- div.post-tail-wrapper -->
|
||
|
||
|
||
|
||
|
||
|
||
</div>
|
||
</div>
|
||
<!-- #core-wrapper -->
|
||
|
||
<!-- panel -->
|
||
<div id="panel-wrapper" class="col-xl-3 ps-2 text-muted">
|
||
<div class="access">
|
||
<!-- Get the last 5 posts from lastmod list. -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<div id="access-lastmod" class="post">
|
||
<div class="panel-heading">Recently Updated</div>
|
||
<ul class="post-content list-unstyled ps-0 pb-1 ms-1 mt-2">
|
||
|
||
|
||
|
||
|
||
<li class="text-truncate lh-lg">
|
||
<a href="/posts/Mac-M1-Run-Diablo-4/">Mac M1 Run Diablo 4 - Links</a>
|
||
</li>
|
||
|
||
|
||
|
||
|
||
<li class="text-truncate lh-lg">
|
||
<a href="/posts/text-and-typography/">Text and Typography</a>
|
||
</li>
|
||
|
||
|
||
|
||
|
||
<li class="text-truncate lh-lg">
|
||
<a href="/posts/Flaws.cloud-AWS/">Flaws.cloud walkthrough</a>
|
||
</li>
|
||
|
||
|
||
|
||
|
||
<li class="text-truncate lh-lg">
|
||
<a href="/posts/M1-Mac-How-to-switch-the-Terminal-between-x86_64-and-arm64/">M1 Mac - How to Switch the Terminal between x86_64 and arm64</a>
|
||
</li>
|
||
|
||
|
||
|
||
|
||
<li class="text-truncate lh-lg">
|
||
<a href="/posts/Admonitions-Documentation/">Admonitions Documentation</a>
|
||
</li>
|
||
|
||
</ul>
|
||
</div>
|
||
<!-- #access-lastmod -->
|
||
|
||
|
||
<!-- The trending tags list -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<div id="access-tags">
|
||
<div class="panel-heading">Trending Tags</div>
|
||
<div class="d-flex flex-wrap mt-3 mb-1 me-3">
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/cybersecurity/">cybersecurity</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/diablo-4/">diablo 4</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/docs/">docs</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/terminal/">terminal</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/diablo/">diablo</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/m1/">M1</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/apple-silicon/">apple silicon</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/cheatsheets/">cheatsheets</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/cloud/">cloud</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/gcih/">GCIH</a>
|
||
|
||
</div>
|
||
</div>
|
||
|
||
|
||
</div>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<div id="toc-wrapper" class="ps-0 pe-4 mb-5">
|
||
<div class="panel-heading ps-3 pt-2 mb-2">Contents</div>
|
||
<nav id="toc"></nav>
|
||
</div>
|
||
|
||
|
||
|
||
</div>
|
||
</div>
|
||
|
||
<!-- tail -->
|
||
|
||
<div class="row">
|
||
<div id="tail-wrapper" class="col-12 col-lg-11 col-xl-9 px-3 pe-xl-4 mt-5">
|
||
|
||
|
||
<!--
|
||
Recommend the other 3 posts according to the tags and categories of the current post,
|
||
if the number is not enough, use the other latest posts to supplement.
|
||
-->
|
||
|
||
<!-- The total size of related posts -->
|
||
|
||
|
||
<!-- An random integer that bigger than 0 -->
|
||
|
||
|
||
<!-- Equals to TAG_SCORE / {max_categories_hierarchy} -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!-- Fill with the other newlest posts -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<div id="related-posts" class="mb-2 mb-sm-4">
|
||
<h3 class="pt-2 mb-4 ms-1" data-toc-skip>
|
||
Further Reading
|
||
</h3>
|
||
<div class="row row-cols-1 row-cols-md-2 row-cols-xl-3 g-4 mb-4">
|
||
|
||
|
||
|
||
<div class="col">
|
||
<a href="/posts/SANS-SEC-504-Resources/" class="card post-preview h-100">
|
||
<div class="card-body">
|
||
<!--
|
||
Date format snippet
|
||
See: ${JS_ROOT}/utils/locale-dateime.js
|
||
-->
|
||
|
||
|
||
|
||
|
||
|
||
<em
|
||
class="small"
|
||
data-ts="1692804956"
|
||
data-df="ll"
|
||
|
||
>
|
||
Aug 23, 2023
|
||
</em>
|
||
|
||
<h4 class="pt-0 my-2" data-toc-skip>SANS SEC 504 - Resources</h4>
|
||
<div class="text-muted small">
|
||
<p>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
Malware stuff
|
||
https://digitalcommons.lsu.edu/cgi/viewcontent.cgi?article=6527&amp;context=gradschool_theses
|
||
|
||
https://github.com/volatilityfoundation/volatility/wiki/Mac
|
||
|
||
Volatility
|
||
A few volatility...
|
||
</p>
|
||
</div>
|
||
</div>
|
||
</a>
|
||
</div>
|
||
|
||
|
||
|
||
<div class="col">
|
||
<a href="/posts/Flaws.cloud-AWS/" class="card post-preview h-100">
|
||
<div class="card-body">
|
||
<!--
|
||
Date format snippet
|
||
See: ${JS_ROOT}/utils/locale-dateime.js
|
||
-->
|
||
|
||
|
||
|
||
|
||
|
||
<em
|
||
class="small"
|
||
data-ts="1692822983"
|
||
data-df="ll"
|
||
|
||
>
|
||
Aug 23, 2023
|
||
</em>
|
||
|
||
<h4 class="pt-0 my-2" data-toc-skip>Flaws.cloud walkthrough</h4>
|
||
<div class="text-muted small">
|
||
<p>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
Flaws.cloud walkthrough
|
||
|
||
DayCyberWox Walkthrough: https://www.youtube.com/watch?v=fEjAryrzLSQ
|
||
Write up: https://daycyberwox.com/exploiting-aws-1-a-beginners-guide-flawscloud#heading-level1
|
||
|
||
1
|
||
2
|
||
3
|
||
4...
|
||
</p>
|
||
</div>
|
||
</div>
|
||
</a>
|
||
</div>
|
||
|
||
|
||
|
||
<div class="col">
|
||
<a href="/posts/Mac-M1-Run-Diablo-4/" class="card post-preview h-100">
|
||
<div class="card-body">
|
||
<!--
|
||
Date format snippet
|
||
See: ${JS_ROOT}/utils/locale-dateime.js
|
||
-->
|
||
|
||
|
||
|
||
|
||
|
||
<em
|
||
class="small"
|
||
data-ts="1692804979"
|
||
data-df="ll"
|
||
|
||
>
|
||
Aug 23, 2023
|
||
</em>
|
||
|
||
<h4 class="pt-0 my-2" data-toc-skip>Mac M1 Run Diablo 4 - Links</h4>
|
||
<div class="text-muted small">
|
||
<p>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
Resources that can help you get started with the Game Porting Tool Kit to run Diablo 4 on Mac M1 architecture.
|
||
|
||
|
||
Resources:
|
||
|
||
https://www.outcoldman.com/en/archive/2023/06/07/playing-diablo-4-on-...
|
||
</p>
|
||
</div>
|
||
</div>
|
||
</a>
|
||
</div>
|
||
|
||
</div>
|
||
<!-- .card-deck -->
|
||
</div>
|
||
<!-- #related-posts -->
|
||
|
||
|
||
|
||
|
||
<!-- Navigation buttons at the bottom of the post. -->
|
||
|
||
<div class="post-navigation d-flex justify-content-between">
|
||
|
||
<a
|
||
href="/posts/Mac-M1-Run-Diablo-4/"
|
||
class="btn btn-outline-primary"
|
||
prompt="Older"
|
||
>
|
||
<p>Mac M1 Run Diablo 4 - Links</p>
|
||
</a>
|
||
|
||
|
||
|
||
<a
|
||
href="/posts/Flaws.cloud-AWS/"
|
||
class="btn btn-outline-primary"
|
||
prompt="Newer"
|
||
>
|
||
<p>Flaws.cloud walkthrough</p>
|
||
</a>
|
||
|
||
</div>
|
||
|
||
|
||
|
||
<!-- The comments switcher -->
|
||
|
||
|
||
|
||
</div>
|
||
</div>
|
||
|
||
|
||
<!-- The Search results -->
|
||
|
||
<div id="search-result-wrapper" class="d-flex justify-content-center unloaded">
|
||
<div class="col-11 post-content">
|
||
<div id="search-hints">
|
||
<!-- The trending tags list -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<div id="access-tags">
|
||
<div class="panel-heading">Trending Tags</div>
|
||
<div class="d-flex flex-wrap mt-3 mb-1 me-3">
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/cybersecurity/">cybersecurity</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/diablo-4/">diablo 4</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/docs/">docs</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/terminal/">terminal</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/diablo/">diablo</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/m1/">M1</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/apple-silicon/">apple silicon</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/cheatsheets/">cheatsheets</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/cloud/">cloud</a>
|
||
|
||
|
||
<a class="post-tag btn btn-outline-primary" href="/tags/gcih/">GCIH</a>
|
||
|
||
</div>
|
||
</div>
|
||
|
||
|
||
</div>
|
||
<div id="search-results" class="d-flex flex-wrap justify-content-center text-muted mt-3"></div>
|
||
</div>
|
||
</div>
|
||
|
||
</div>
|
||
</div>
|
||
|
||
<!-- The Footer -->
|
||
|
||
<footer>
|
||
<div class="container px-lg-4">
|
||
<div class="d-flex justify-content-center align-items-center text-muted mx-md-3">
|
||
<p>Using the <a href="https://jekyllrb.com" target="_blank" rel="noopener">Jekyll</a> theme <a href="https://github.com/cotes2020/jekyll-theme-chirpy" target="_blank" rel="noopener">Chirpy</a>
|
||
</p>
|
||
|
||
<p>©
|
||
2023
|
||
<a href="https://github.com/username">Eric Reymundo</a>.
|
||
|
||
<span
|
||
data-bs-toggle="tooltip"
|
||
data-bs-placement="top"
|
||
title="Except where otherwise noted, the blog posts on this site are licensed under the Creative Commons Attribution 4.0 International (CC BY 4.0) License by the author."
|
||
>Some rights reserved.</span>
|
||
|
||
</p>
|
||
</div>
|
||
</div>
|
||
</footer>
|
||
|
||
|
||
<div id="mask"></div>
|
||
|
||
<button id="back-to-top" aria-label="back-to-top" class="btn btn-lg btn-box-shadow">
|
||
<i class="fas fa-angle-up"></i>
|
||
</button>
|
||
|
||
|
||
<div
|
||
id="notification"
|
||
class="toast"
|
||
role="alert"
|
||
aria-live="assertive"
|
||
aria-atomic="true"
|
||
data-bs-animation="true"
|
||
data-bs-autohide="false"
|
||
>
|
||
<div class="toast-header">
|
||
<button
|
||
type="button"
|
||
class="btn-close ms-auto"
|
||
data-bs-dismiss="toast"
|
||
aria-label="Close"
|
||
></button>
|
||
</div>
|
||
<div class="toast-body text-center pt-0">
|
||
<p class="px-2 mb-3">A new version of content is available.</p>
|
||
<button type="button" class="btn btn-primary" aria-label="Update">
|
||
Update
|
||
</button>
|
||
</div>
|
||
</div>
|
||
|
||
|
||
<!-- JS selector for site. -->
|
||
|
||
<!-- commons -->
|
||
|
||
|
||
|
||
<!-- layout specified -->
|
||
|
||
|
||
|
||
|
||
|
||
<!-- image lazy-loading & popup & clipboard -->
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<script src="https://cdn.jsdelivr.net/combine/npm/jquery@3.7.0/dist/jquery.min.js,npm/bootstrap@5.2.3/dist/js/bootstrap.bundle.min.js,npm/simple-jekyll-search@1.10.0/dest/simple-jekyll-search.min.js,npm/lazysizes@5.3.2/lazysizes.min.js,npm/magnific-popup@1.1.0/dist/jquery.magnific-popup.min.js,npm/clipboard@2.0.11/dist/clipboard.min.js,npm/dayjs@1.11.7/dayjs.min.js,npm/dayjs@1.11.7/locale/en.min.js,npm/dayjs@1.11.7/plugin/relativeTime.min.js,npm/dayjs@1.11.7/plugin/localizedFormat.min.js,npm/tocbot@4.21.0/dist/tocbot.min.js"></script>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<script defer src="/assets/js/dist/post.min.js"></script>
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
<!--
|
||
Jekyll Simple Search loader
|
||
See: <https://github.com/christian-fei/Simple-Jekyll-Search>
|
||
-->
|
||
|
||
|
||
|
||
|
||
|
||
<script>
|
||
/* Note: dependent library will be loaded in `js-selector.html` */
|
||
SimpleJekyllSearch({
|
||
searchInput: document.getElementById('search-input'),
|
||
resultsContainer: document.getElementById('search-results'),
|
||
json: '/assets/js/data/search.json',
|
||
searchResultTemplate: '<div class="px-1 px-sm-2 px-lg-4 px-xl-0"> <a href="{url}">{title}</a> <div class="post-meta d-flex flex-column flex-sm-row text-muted mt-1 mb-1"> {categories} {tags} </div> <p>{snippet}</p></div>',
|
||
noResultsText: '<p class="mt-5"></p>',
|
||
templateMiddleware: function(prop, value, template) {
|
||
if (prop === 'categories') {
|
||
if (value === '') {
|
||
return `${value}`;
|
||
} else {
|
||
return `<div class="me-sm-4"><i class="far fa-folder fa-fw"></i>${value}</div>`;
|
||
}
|
||
}
|
||
|
||
if (prop === 'tags') {
|
||
if (value === '') {
|
||
return `${value}`;
|
||
} else {
|
||
return `<div><i class="fa fa-tag fa-fw"></i>${value}</div>`;
|
||
}
|
||
}
|
||
}
|
||
});
|
||
</script>
|
||
|
||
</body>
|
||
</html>
|
||
|