mirror of
https://github.com/cotes2020/chirpy-starter.git
synced 2025-09-14 12:26:21 +10:00
added articles
This commit is contained in:
BIN
_posts/.DS_Store
vendored
Normal file
BIN
_posts/.DS_Store
vendored
Normal file
Binary file not shown.
150
_posts/2023-03-Markdown Cheatsheet.md
Normal file
150
_posts/2023-03-Markdown Cheatsheet.md
Normal file
@ -0,0 +1,150 @@
|
|||||||
|
---
|
||||||
|
title: Markdown Cheatsheet
|
||||||
|
date: 2023-03-16
|
||||||
|
catagories: [documentation, cheatsheets]
|
||||||
|
tags: [docs, cheatsheet, markdown]
|
||||||
|
---
|
||||||
|
|
||||||
|
# Markdown Cheat Sheet
|
||||||
|
|
||||||
|
>**Note**
|
||||||
|
>Use `source mode` to view the source for easier guidance on markdown syntax.
|
||||||
|
|
||||||
|
Ad-note syntax:
|
||||||
|
|
||||||
|
```ad-note
|
||||||
|
color: 83, 188, 109
|
||||||
|
Hello this is a note.
|
||||||
|
```
|
||||||
|
|
||||||
|
you can change the color by using the RGB color picker: https://g.co/kgs/Mig2hN
|
||||||
|
|
||||||
|
|
||||||
|
## Text highlight
|
||||||
|
```
|
||||||
|
<span style="color:yellow">Insert text here.</span>
|
||||||
|
```
|
||||||
|
|
||||||
|
Thanks for visiting [The Markdown Guide](https://www.markdownguide.org)!
|
||||||
|
|
||||||
|
This Markdown cheat sheet provides a quick overview of all the Markdown syntax elements. It can’t cover every edge case, so if you need more information about any of these elements, refer to the reference guides for [basic syntax](https://www.markdownguide.org/basic-syntax) and [extended syntax](https://www.markdownguide.org/extended-syntax).
|
||||||
|
|
||||||
|
## Basic Syntax
|
||||||
|
|
||||||
|
These are the elements outlined in John Gruber’s original design document. All Markdown applications support these elements.
|
||||||
|
|
||||||
|
### Heading
|
||||||
|
|
||||||
|
# H1
|
||||||
|
## H2
|
||||||
|
### H3
|
||||||
|
|
||||||
|
### Bold
|
||||||
|
|
||||||
|
**bold text**
|
||||||
|
|
||||||
|
### Italic
|
||||||
|
|
||||||
|
*italicized text*
|
||||||
|
|
||||||
|
### Blockquote
|
||||||
|
|
||||||
|
> blockquote
|
||||||
|
|
||||||
|
### Ordered List
|
||||||
|
|
||||||
|
1. First item
|
||||||
|
2. Second item
|
||||||
|
3. Third item
|
||||||
|
|
||||||
|
### Unordered List
|
||||||
|
|
||||||
|
- First item
|
||||||
|
- Second item
|
||||||
|
- Third item
|
||||||
|
|
||||||
|
### Code
|
||||||
|
|
||||||
|
`code`
|
||||||
|
|
||||||
|
### Horizontal Rule
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
### Link
|
||||||
|
|
||||||
|
[Markdown Guide](https://www.markdownguide.org)
|
||||||
|
|
||||||
|
### Image
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## Extended Syntax
|
||||||
|
|
||||||
|
These elements extend the basic syntax by adding additional features. Not all Markdown applications support these elements.
|
||||||
|
|
||||||
|
### Table
|
||||||
|
|
||||||
|
| Syntax | Description |
|
||||||
|
| ----------- | ----------- |
|
||||||
|
| Header | Title |
|
||||||
|
| Paragraph | Text |
|
||||||
|
|
||||||
|
### Fenced Code Block
|
||||||
|
|
||||||
|
```
|
||||||
|
{
|
||||||
|
"firstName": "John",
|
||||||
|
"lastName": "Smith",
|
||||||
|
"age": 25
|
||||||
|
}
|
||||||
|
```
|
||||||
|
|
||||||
|
### Footnote
|
||||||
|
|
||||||
|
Here's a sentence with a footnote. [^1]
|
||||||
|
|
||||||
|
[^1]: This is the footnote.
|
||||||
|
|
||||||
|
### Heading ID
|
||||||
|
|
||||||
|
### My Great Heading {#custom-id}
|
||||||
|
|
||||||
|
### Definition List
|
||||||
|
|
||||||
|
term
|
||||||
|
: definition
|
||||||
|
|
||||||
|
### Strikethrough
|
||||||
|
|
||||||
|
~~The world is flat.~~
|
||||||
|
|
||||||
|
### Task List
|
||||||
|
|
||||||
|
- [x] Write the press release
|
||||||
|
- [ ] Update the website
|
||||||
|
- [ ] Contact the media
|
||||||
|
|
||||||
|
### Emoji
|
||||||
|
|
||||||
|
That is so funny! :joy:
|
||||||
|
|
||||||
|
(See also [Copying and Pasting Emoji](https://www.markdownguide.org/extended-syntax/#copying-and-pasting-emoji))
|
||||||
|
|
||||||
|
### Highlight
|
||||||
|
|
||||||
|
I need to highlight these ==very important words==.
|
||||||
|
|
||||||
|
### Subscript
|
||||||
|
|
||||||
|
H~2~O
|
||||||
|
|
||||||
|
### Superscript
|
||||||
|
|
||||||
|
X^2^
|
||||||
|
|
||||||
|
### Additional Resources
|
||||||
|
|
||||||
|
- [Highlight a note or warning in blockquote](https://github.com/community/community/discussions/16925)
|
||||||
|
|
||||||
|
![[Pasted image 20230330125153.png]]
|
||||||
682
_posts/2023-05-05-Admonitions Documentation.md
Normal file
682
_posts/2023-05-05-Admonitions Documentation.md
Normal file
@ -0,0 +1,682 @@
|
|||||||
|
---
|
||||||
|
title: Admonitions Documentation
|
||||||
|
date: 08-23-2023
|
||||||
|
catagories: [cheatsheets, documentation]
|
||||||
|
tags: [docs, cheatsheets]
|
||||||
|
---
|
||||||
|
|
||||||
|
> **Note**
|
||||||
|
> It appears a note in MarkDown is not possible currently.
|
||||||
|
> Reference: https://talk.commonmark.org/t/github-is-beta-testing-their-own-admonition-syntax-we-should-weigh-in/4173
|
||||||
|
|
||||||
|
GitHub Link: https://github.com/javalent/admonitions
|
||||||
|
|
||||||
|
# Obsidian Admonition
|
||||||
|
|
||||||
|
Adds admonition block-styled content to Obsidian.md, styled after [Material for MkDocs](https://squidfunk.github.io/mkdocs-material/reference/admonitions/)
|
||||||
|
|
||||||
|
## Please note!
|
||||||
|
|
||||||
|
Obsidian 0.14 adds support for [Callout boxes](https://help.obsidian.md/Editing+and+formatting/Callouts)!
|
||||||
|
|
||||||
|
**With this change, Admonitions will be transitioning to a plugin that enhances the core callout box feature.**
|
||||||
|
|
||||||
|
What does this mean, you might ask?
|
||||||
|
|
||||||
|
1. All of your existing code block admonitions will continue to work, and will always work!
|
||||||
|
2. You can continue to use Admonitions to create custom types, and all of your custom types will just work as a callout, without you having to do anything!
|
||||||
|
3. If you have any Microsoft Document syntax admonitions, they will have to be converted to the new callout box syntax - there is a button in Admonition settings to auto-convert these for you.
|
||||||
|
4. You can use Admonitions to set default titles, default collapse states, or defaulting to not having a title.
|
||||||
|
5. Admonitions adds helpful editor suggestors for quickly entering your custom callout boxes.
|
||||||
|
6. Admonitions adds helpful commands for inserting callout boxes, including the ability to register commands for specific types.
|
||||||
|
|
||||||
|
## Usage
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/all.gif)
|
||||||
|
|
||||||
|
Place a code block with the admonition type:
|
||||||
|
|
||||||
|
```ad-important
|
||||||
|
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla et euismod nulla.
|
||||||
|
```
|
||||||
|
|
||||||
|
Becomes:
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/default.png)
|
||||||
|
|
||||||
|
## Options
|
||||||
|
|
||||||
|
```ad-<type> # Admonition type. See below for a list of available types.
|
||||||
|
title: # Admonition title.
|
||||||
|
collapse: # Create a collapsible admonition.
|
||||||
|
icon: # Override the icon.
|
||||||
|
color: # Override the color.
|
||||||
|
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla et euismod nulla.
|
||||||
|
```
|
||||||
|
|
||||||
|
Please note that as of **4.4.1**, the `title`, `collapse`, `icon` and `color` parameters must be at the _top_ of the block, in any order.
|
||||||
|
|
||||||
|
### Title
|
||||||
|
|
||||||
|
The admonition will render with the type of admonition by default. If you wish to customize the title, you can do so this way:
|
||||||
|
|
||||||
|
```ad-note
|
||||||
|
title: Title
|
||||||
|
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla et euismod nulla.
|
||||||
|
```
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/title.png)
|
||||||
|
|
||||||
|
Custom titles are rendered as Markdown, so they support the full Obsidian Markdown syntax.
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/title-markdown.png)
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/rendered-title-markdown.png)
|
||||||
|
|
||||||
|
Leave the title field blank to only display the admonition.
|
||||||
|
|
||||||
|
```ad-note
|
||||||
|
title:
|
||||||
|
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla et euismod nulla.
|
||||||
|
```
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/no-title.png)
|
||||||
|
|
||||||
|
### Collapsible
|
||||||
|
|
||||||
|
Use the `collapse` parameter to create a collapsible admonition.
|
||||||
|
|
||||||
|
`collapse: open` will start the admonition opened on render, but allow collapse on click.
|
||||||
|
|
||||||
|
If a blank title is provided, the collapse parameter will not do anything.
|
||||||
|
|
||||||
|
Admonitions may be set to be collapsible by default in settings.
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/collapse.gif)
|
||||||
|
|
||||||
|
### Icon
|
||||||
|
|
||||||
|
The admonition icon can be overridden using the `icon` parameter. **The icon name entered must be the exact icon name from FontAwesome or RPGAwesome.**
|
||||||
|
|
||||||
|
````
|
||||||
|
```ad-note
|
||||||
|
icon: triforce
|
||||||
|
|
||||||
|
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla et euismod nulla.
|
||||||
|
|
||||||
|
```
|
||||||
|
````
|
||||||
|
|
||||||
|
### Color
|
||||||
|
|
||||||
|
The admonition color can be overridden using the `color` parameter. **The color entered must be an RGB triad.**
|
||||||
|
|
||||||
|
````
|
||||||
|
```ad-note
|
||||||
|
color: 200, 200, 200
|
||||||
|
|
||||||
|
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla et euismod nulla.
|
||||||
|
|
||||||
|
```
|
||||||
|
````
|
||||||
|
|
||||||
|
### No Content
|
||||||
|
|
||||||
|
An admonition with no content will render as just the title block.
|
||||||
|
|
||||||
|
````
|
||||||
|
```ad-note
|
||||||
|
```
|
||||||
|
````
|
||||||
|
|
||||||
|
## Nesting Admonitions
|
||||||
|
|
||||||
|
Nesting admonitions may be done by increasing the number of backticks.
|
||||||
|
|
||||||
|
Example:
|
||||||
|
|
||||||
|
``````
|
||||||
|
`````ad-note
|
||||||
|
title: Nested Admonitions
|
||||||
|
collapse: open
|
||||||
|
|
||||||
|
Hello!
|
||||||
|
|
||||||
|
````ad-note
|
||||||
|
title: This admonition is nested.
|
||||||
|
This is a nested admonition!
|
||||||
|
|
||||||
|
```ad-warning
|
||||||
|
title: This admonition is closed.
|
||||||
|
collapse: close
|
||||||
|
```
|
||||||
|
|
||||||
|
````
|
||||||
|
|
||||||
|
This is in the original admonition.
|
||||||
|
`````
|
||||||
|
``````
|
||||||
|
|
||||||
|
## Rendering Code Blocks inside Admonitions
|
||||||
|
|
||||||
|
Code blocks may be nested inside admonitions using a method similar to [Nesting Admonitions](https://github.com/javalent/admonitions#Nesting-Admonitions) above.
|
||||||
|
|
||||||
|
Additionally, for a single layer, the `~~~` markdown codeblock syntax may be used:
|
||||||
|
|
||||||
|
`````
|
||||||
|
````ad-info
|
||||||
|
|
||||||
|
```ad-bug
|
||||||
|
title: I'm Nested!
|
||||||
|
~~~javascript
|
||||||
|
throw new Error("Oops, I'm a bug.");
|
||||||
|
~~~
|
||||||
|
```
|
||||||
|
|
||||||
|
```javascript
|
||||||
|
console.log("Hello!");
|
||||||
|
```
|
||||||
|
|
||||||
|
````
|
||||||
|
`````
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/nested-code.png)
|
||||||
|
|
||||||
|
## Admonition Types
|
||||||
|
|
||||||
|
The following admonition types are currently supported:
|
||||||
|
|
||||||
|
Type
|
||||||
|
|
||||||
|
Aliases
|
||||||
|
|
||||||
|
note
|
||||||
|
|
||||||
|
note, seealso
|
||||||
|
|
||||||
|
abstract
|
||||||
|
|
||||||
|
abstract, summary, tldr
|
||||||
|
|
||||||
|
info
|
||||||
|
|
||||||
|
info, todo
|
||||||
|
|
||||||
|
tip
|
||||||
|
|
||||||
|
tip, hint, important
|
||||||
|
|
||||||
|
success
|
||||||
|
|
||||||
|
success, check, done
|
||||||
|
|
||||||
|
question
|
||||||
|
|
||||||
|
question, help, faq
|
||||||
|
|
||||||
|
warning
|
||||||
|
|
||||||
|
warning, caution, attention
|
||||||
|
|
||||||
|
failure
|
||||||
|
|
||||||
|
failure, fail, missing
|
||||||
|
|
||||||
|
danger
|
||||||
|
|
||||||
|
danger, error
|
||||||
|
|
||||||
|
bug
|
||||||
|
|
||||||
|
bug
|
||||||
|
|
||||||
|
example
|
||||||
|
|
||||||
|
example
|
||||||
|
|
||||||
|
quote
|
||||||
|
|
||||||
|
quote, cite
|
||||||
|
|
||||||
|
See [this](https://squidfunk.github.io/mkdocs-material/reference/admonitions/) for a reference of what these admonitions look like.
|
||||||
|
|
||||||
|
The default admonitions are customizable by creating a user-defined admonition of the same name.
|
||||||
|
|
||||||
|
## Custom Admonitions & Callouts
|
||||||
|
|
||||||
|
Custom admonitions may be created in settings. Creating a custom admonition will also enable it to be used as an Obsidian callout.
|
||||||
|
|
||||||
|
Creating a new admonition requires three things: the type, the icon to use, and the color of the admonition.
|
||||||
|
|
||||||
|
Only one admonition of each type may exist at any given time; if another admonition of the same type is created, it will override the previously created one.
|
||||||
|
|
||||||
|
If a default admonition is overridden, it can be restored by deleting the user-defined admonition.
|
||||||
|
|
||||||
|
Please note that by default, the background color of the title is simply the color of the admonition at 10% opacity. CSS must be used to update this.
|
||||||
|
|
||||||
|
### Images as Icons
|
||||||
|
|
||||||
|
Images can be uploaded to use as an admonition icon instead of an icon from a downloaded icon set.
|
||||||
|
|
||||||
|
These images will be resized to 24px x 24px to be stored in the plugin's saved data.
|
||||||
|
|
||||||
|
To remove an image icon, simply choose an icon in the icon chooser text box.
|
||||||
|
|
||||||
|
## Global Commands
|
||||||
|
|
||||||
|
Several commands are available for the plugin by default.
|
||||||
|
|
||||||
|
### Collapse and Open All Admonitions In Note
|
||||||
|
|
||||||
|
If these two commands are triggered with an open note, all collapsible admonitions will be collapsed or open respectively.
|
||||||
|
|
||||||
|
### Insert Admonition
|
||||||
|
|
||||||
|
This will open a modal where the admonition type, title and collapse behavior can be set, then the generated admonition code block will be inserted into the open editor.
|
||||||
|
|
||||||
|
### Admonition-specific commands
|
||||||
|
|
||||||
|
Commands may be registered for each [custom admonition](https://github.com/javalent/admonitions#custom-admonition-types) type to insert them into an open note by clicking the `Register Commands` button in [Settings](https://github.com/javalent/admonitions#custom-admonition-types).
|
||||||
|
|
||||||
|
3 commands will be registered: `Insert <type> Callout`, `Insert <type>`, and `Insert <type> with Title`.
|
||||||
|
|
||||||
|
#### Insert Callout
|
||||||
|
|
||||||
|
The selected type will be inserted as an Obsidian callout, and any selected text will be included with it.
|
||||||
|
|
||||||
|
#### Insert
|
||||||
|
|
||||||
|
The selected type will be inserted as a codeblock admonition, and any selected text will be included with it.
|
||||||
|
|
||||||
|
#### Insert with Title
|
||||||
|
|
||||||
|
The selected type will be inserted as a codeblock admonition, and any selected text will be included with it. The `title:` parameter will also be added and the cursor will be placed at that line.
|
||||||
|
|
||||||
|
### Mermaid Graphs
|
||||||
|
|
||||||
|
Mermaid graphs are supported by Admonitions, but with some caveats:
|
||||||
|
|
||||||
|
1. You cannot combine mermaid graphs and embeds/transclusions.
|
||||||
|
2. Mermaid graphs do not work in collapsed-by-default admonitions.
|
||||||
|
|
||||||
|
## Non-code block Admonitions
|
||||||
|
|
||||||
|
> ❗ This syntax has been officially removed as of Admonitions 7.0.0.
|
||||||
|
>
|
||||||
|
> Use the [Obsidian Callout box](https://help.obsidian.md/Editing+and+formatting/Callouts) syntax instead!
|
||||||
|
|
||||||
|
As of version 6.0.0, there is a new setting: Enable Non-codeblock Admonitions.
|
||||||
|
|
||||||
|
This setting is highly experimental and may not work as expected, and there are a few caveats listed at the end of this section to keep in mind.
|
||||||
|
|
||||||
|
This setting allows for creating an admonition without wrapping it in a code block, which means that links and tags will sync into Obsidian's cache. A non-codeblock admonition may be created using the following syntax:
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
!!! ad-<type> Title goes here!
|
||||||
|
|
||||||
|
content
|
||||||
|
|
||||||
|
--- admonition
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
This will create the appropriate admonition type, embed the content, and give it the supplied title.
|
||||||
|
|
||||||
|
### Titles
|
||||||
|
|
||||||
|
Titles should be placed after the admonition block. Currently, markdown in titles is not supported.
|
||||||
|
|
||||||
|
An empty title can be created by either placing two spaces after the admonition type:
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
!!! ad-<type>
|
||||||
|
|
||||||
|
content
|
||||||
|
|
||||||
|
--- admonition
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
or by placing empty double quotes:
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
!!! ad-<type> ""
|
||||||
|
|
||||||
|
content
|
||||||
|
|
||||||
|
--- admonition
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
### Collapsible
|
||||||
|
|
||||||
|
A collapsible admonition may be created using the following syntax:
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
??? ad-<type> Title goes here!
|
||||||
|
|
||||||
|
content
|
||||||
|
|
||||||
|
--- admonition
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
A collapsible admonition may default to "open" by appending a +:
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
???+ ad-<type> Title goes here!
|
||||||
|
|
||||||
|
content
|
||||||
|
|
||||||
|
--- admonition
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
### Caveats
|
||||||
|
|
||||||
|
1. Changes to the admonition after render require the cache to be cleared. The note must be closed and re-opened (and sometimes, a different note must be opened first).
|
||||||
|
1. This is _all_ changes, including the admonition type, title, content, even whether or not a collapsible admonition is open or closed initially.
|
||||||
|
2. Nested admonitions are not currently supported.
|
||||||
|
|
||||||
|
If you experience any bugs using this setting, please create an issue and I will look into them.
|
||||||
|
|
||||||
|
## Microsoft Document Syntax
|
||||||
|
|
||||||
|
> ❗ This syntax has been officially removed as of version **8.0.0**.
|
||||||
|
>
|
||||||
|
> Use the [Obsidian Callout box](https://help.obsidian.md/Editing+and+formatting/Callouts) syntax instead!
|
||||||
|
|
||||||
|
As of v6.8.0, an additional non-code block syntax can be used that is inspired by the [Microsoft Document Syntax](https://docs.microsoft.com/en-us/contribute/markdown-reference) to render admonitions.
|
||||||
|
|
||||||
|
> **⚠️ Please note:**
|
||||||
|
>
|
||||||
|
> Unlike the Microsoft Document Syntax, the type is not required to be upper case.
|
||||||
|
>
|
||||||
|
> The plugin will use an exact-match first, then try to find a case-insensitive match.
|
||||||
|
|
||||||
|
> [!quote]
|
||||||
|
> This is an admonition!
|
||||||
|
|
||||||
|
[](https://raw.githubusercontent.com/valentine195/obsidian-admonition/master/images/msdocs.png)
|
||||||
|
|
||||||
|
This syntax can also be used on indented code blocks:
|
||||||
|
|
||||||
|
[!quote]
|
||||||
|
This is an admonition!
|
||||||
|
|
||||||
|
### Title
|
||||||
|
|
||||||
|
A title can be added to the MSDoc-style admonition by appending it after the type.
|
||||||
|
|
||||||
|
> [!quote: This is the title!]
|
||||||
|
> This is an admonition!
|
||||||
|
|
||||||
|
Like the code block syntax, providing an empty title will remove the title from the rendered admonition.
|
||||||
|
|
||||||
|
> [!quote:]
|
||||||
|
> This admonition won't have a title!
|
||||||
|
|
||||||
|
### Collapse
|
||||||
|
|
||||||
|
Collapse can be set by appending the following characters after the brackets:
|
||||||
|
|
||||||
|
Character
|
||||||
|
|
||||||
|
Collapse Type
|
||||||
|
|
||||||
|
`+`
|
||||||
|
|
||||||
|
`open`
|
||||||
|
|
||||||
|
`-`
|
||||||
|
|
||||||
|
`closed`
|
||||||
|
|
||||||
|
`x`
|
||||||
|
|
||||||
|
`none`
|
||||||
|
|
||||||
|
## Publish
|
||||||
|
|
||||||
|
Obsidian plugins do not work on publish sites; however, version 6.4.0+ has an option to generate a JavaScript file that can be used on Publish sites with **custom domains**.
|
||||||
|
|
||||||
|
**Obsidian Publish only allows external JavaScript on publish sites with custom domains. If your Publish is ran through Obsidian, this will not work.**
|
||||||
|
|
||||||
|
Instructions:
|
||||||
|
|
||||||
|
1. Go the Admonition settings tab and click the "Generate JS for Publish" button.
|
||||||
|
2. Save the JavaScript file.
|
||||||
|
3. Copy the contents of the JS file to your `publish.js` file.
|
||||||
|
4. Add the contents of the `assets/main.css` file to your `publish.css` file.
|
||||||
|
|
||||||
|
Please note that I can give no guarantees of stability on your publish site. Other JavaScript you include may conflict with this file. If you run into an issue using it, please create an issue on this repository and I will try to help you.
|
||||||
|
|
||||||
|
## Icon Packs
|
||||||
|
|
||||||
|
Additional icon packs can be downloaded in settings.
|
||||||
|
|
||||||
|
### Adding Icon Packs
|
||||||
|
|
||||||
|
Want to add an existing icon pack? Make a pull request with the following:
|
||||||
|
|
||||||
|
1. Add a new folder in the [icons](https://github.com/javalent/admonitions/blob/main/icons) folder with the name of your icon set.
|
||||||
|
2. Create an `icons.json` file that has the icons defined as an Object. Please see the [Octicons json](https://github.com/javalent/admonitions/blob/main/icons/octicons/icons.json) for reference.
|
||||||
|
3. Put your icon pack's information in the two variables in the [Icon Packs](https://github.com/javalent/admonitions/blob/main/src/icons/packs.ts) file.
|
||||||
|
|
||||||
|
# Settings
|
||||||
|
|
||||||
|
## Custom Admonition Types
|
||||||
|
|
||||||
|
[Custom admonition](https://github.com/javalent/admonitions#custom-admonitions--callouts) types can be created and managed in this section of the settings.
|
||||||
|
|
||||||
|
### Export Custom Types as CSS
|
||||||
|
|
||||||
|
This button will generate a CSS snippet that you can save and use for your custom callout types.
|
||||||
|
|
||||||
|
## Importing Custom Admonitions
|
||||||
|
|
||||||
|
Custom admonitions can be imported in settings from a JSON array of definitions.
|
||||||
|
|
||||||
|
At a _minimum_, you only need a valid admonition type:
|
||||||
|
|
||||||
|
[
|
||||||
|
{
|
||||||
|
"type": "my-custom-type"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
|
||||||
|
This will use the `pencil-alt` FontAwesome icon and a random color, and set all other properties as false.
|
||||||
|
|
||||||
|
However, you can specify an icon and color as well:
|
||||||
|
|
||||||
|
[
|
||||||
|
{
|
||||||
|
"type": "my-custom-type",
|
||||||
|
"icon": "globe",
|
||||||
|
"color": "120,120,120"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
|
||||||
|
If you want to specify an icon pack, you can do so like this:
|
||||||
|
|
||||||
|
[
|
||||||
|
{
|
||||||
|
"type": "my-custom-type",
|
||||||
|
"icon": {
|
||||||
|
"name": "globe",
|
||||||
|
"type": "font-awesome"
|
||||||
|
},
|
||||||
|
"color": "120,120,120"
|
||||||
|
}
|
||||||
|
]
|
||||||
|
|
||||||
|
All of the possible fields are defined [here](https://github.com/valentine195/obsidian-admonition/blob/2fb38ccc0b39ada8d3d0a4476e9ff3333c52c3ae/src/%40types/index.d.ts#L5).
|
||||||
|
|
||||||
|
## Admonition Settings
|
||||||
|
|
||||||
|
Settings specific to admonitions are managed in this section.
|
||||||
|
|
||||||
|
### Add Drop Shadow
|
||||||
|
|
||||||
|
A drop shadow will be added to admonitions by default.
|
||||||
|
|
||||||
|
If this setting is off, rendered admonitions will receive the `.no-drop` class.
|
||||||
|
|
||||||
|
### Collapsible By Default
|
||||||
|
|
||||||
|
All admonitions will be collapsible by default, unless `collapse: none` is set in the admonition parameters.
|
||||||
|
|
||||||
|
### Default Collapse Type
|
||||||
|
|
||||||
|
> ⚠️ This setting is only available when Collapsible By Default is true.
|
||||||
|
|
||||||
|
Set the default collapse type used when setting an admonition collapsible by default.
|
||||||
|
|
||||||
|
### Add Copy Button
|
||||||
|
|
||||||
|
A "Copy Content" button will be added to the top-right corner of the admonition & callout content.
|
||||||
|
|
||||||
|
### Parse Titles as Markdown
|
||||||
|
|
||||||
|
Turn this setting off to prevent admonition titles from being rendered as markdown.
|
||||||
|
|
||||||
|
### Set Admonition Colors
|
||||||
|
|
||||||
|
Controls whether or not a rendered admonition will receive a color.
|
||||||
|
|
||||||
|
Turn this off to totally control color via CSS.
|
||||||
|
|
||||||
|
### Hide Empty Admonitions
|
||||||
|
|
||||||
|
Admonitions with no content are hidden by default.
|
||||||
|
|
||||||
|
> ⚠️ Please note that this only works for Admonitions that have _no text content whatsoever_.
|
||||||
|
|
||||||
|
## Icon Packs
|
||||||
|
|
||||||
|
### Use Font Awesome Icons
|
||||||
|
|
||||||
|
The plugin comes pre-bundled with the entire [Font Awesome Free](https://fontawesome.com/search?m=free&s=brands%2Cregular%2Csolid) icon set. Turn this setting off to not include them in the icon picker.
|
||||||
|
|
||||||
|
Existing custom Admonitions that use Font Awesome icons will continue to work.
|
||||||
|
|
||||||
|
### Additional Icon Packs
|
||||||
|
|
||||||
|
Additional icon packs can be downloaded to supplement the included Font Awesome Free icon set.
|
||||||
|
|
||||||
|
**Downloading an icon pack requires an internet connection.**
|
||||||
|
|
||||||
|
Current additional icon packs available are the [Octicons](https://primer.style/octicons/) set and the [RPG Awesome](https://nagoshiashumari.github.io/Rpg-Awesome/) set.
|
||||||
|
|
||||||
|
> 📝 For backwards compability, if an Admonition was created prior to version **7.0.0** using an RPG Awesome icon, the pack will try to be downloaded.
|
||||||
|
|
||||||
|
## Additional Syntaxes
|
||||||
|
|
||||||
|
Obsidian 0.14 has introduced [Callout boxes](https://help.obsidian.md/Editing+and+formatting/Callouts) to its core functionality using a similar syntax to the Microsoft Document callouts.
|
||||||
|
|
||||||
|
This has rendered the Microsoft Document syntax for Admonitions obsolete, but Admonitions can still be used to create and manage your custom callout types.
|
||||||
|
|
||||||
|
Your existing code block Admonitions will always work!
|
||||||
|
|
||||||
|
### Enable Non-codeblock Admonitions
|
||||||
|
|
||||||
|
> ❗ This setting has been removed as of version **7.0.0**.
|
||||||
|
>
|
||||||
|
> It is recommended to use the [Obsidian Callout box](https://help.obsidian.md/Editing+and+formatting/Callouts) instead.
|
||||||
|
|
||||||
|
Enabled use of `!!! ad-<type>` style admonitions. No longer supported, will be removed in a future version.
|
||||||
|
|
||||||
|
### Allow Microsoft Document Syntax
|
||||||
|
|
||||||
|
> ❗ This syntax has been officially removed as of version **8.0.0**.
|
||||||
|
>
|
||||||
|
> Use the [Obsidian Callout box](https://help.obsidian.md/Editing+and+formatting/Callouts) syntax instead!
|
||||||
|
|
||||||
|
Enables use of the [Microsoft Document Syntax](https://github.com/javalent/admonitions#microsoft-document-syntax) for blockquote admonitions.
|
||||||
|
|
||||||
|
### Use Microsoft Document Syntax for Indented Code Blocks
|
||||||
|
|
||||||
|
> ❗ This syntax has been officially removed as of version **8.0.0**.
|
||||||
|
>
|
||||||
|
> Use the [Obsidian Callout box](https://help.obsidian.md/Editing+and+formatting/Callouts) syntax instead!
|
||||||
|
|
||||||
|
Enables use of the [Microsoft Document Syntax](https://github.com/javalent/admonitions#microsoft-document-syntax) for indented code blocks.
|
||||||
|
|
||||||
|
### Render Microsoft Document Syntax in Live Preview
|
||||||
|
|
||||||
|
> ❗ This syntax has been officially removed as of version **8.0.0**.
|
||||||
|
>
|
||||||
|
> Use the [Obsidian Callout box](https://help.obsidian.md/Editing+and+formatting/Callouts) syntax instead!
|
||||||
|
|
||||||
|
Enables use of the [Microsoft Document Syntax](https://github.com/javalent/admonitions#microsoft-document-syntax) in live preview.
|
||||||
|
|
||||||
|
This feature is still under development and you may experience rendering bugs.
|
||||||
|
|
||||||
|
### Convert MSDoc Admonitions to Callouts (**v8.0.0+**)
|
||||||
|
|
||||||
|
This button can be used to convert any existing Microsoft Document syntax Admonitions to the new [Callout box](https://help.obsidian.md/Editing+and+formatting/Callouts) syntax.
|
||||||
|
|
||||||
|
## Advanced Settings
|
||||||
|
|
||||||
|
### Markdown Syntax Highlighting
|
||||||
|
|
||||||
|
Enable syntax highlighting when editing admonition code blocks.
|
||||||
|
|
||||||
|
### Sync Links to Metadata Cache
|
||||||
|
|
||||||
|
The plugin will attempt to syncronize links to the metadata cache to be displayed in graph view.
|
||||||
|
|
||||||
|
This setting is experimental. Links will only be synced when rendered in an admonition and they will not persist if you close and re-open Obsidian.
|
||||||
|
|
||||||
|
Please see [this issue](https://github.com/valentine195/obsidian-admonition/issues/144) for more information.
|
||||||
|
|
||||||
|
If you require links to be fully synced, it is recommended to use the [Microsoft Document Syntax](https://github.com/javalent/admonitions#microsoft-document-syntax).
|
||||||
|
|
||||||
|
### Generate JS for Publish
|
||||||
|
|
||||||
|
Use this setting to enable Admonitions on custom-domain Obsidian Publish websites.
|
||||||
|
|
||||||
|
See [Publish] for more information.
|
||||||
|
|
||||||
|
# Todo
|
||||||
|
|
||||||
|
No additional features are planned at this time. If there is a feature missing that you would like to see, please open an issue.
|
||||||
|
|
||||||
|
- Add the ability to collapse the admonition
|
||||||
|
- Custom admonitions
|
||||||
|
- Settings tab to customize icon and color of all admonitions
|
||||||
|
- Ability to render markdown inside an admonition
|
||||||
|
|
||||||
|
# Installation
|
||||||
|
|
||||||
|
## From within Obsidian
|
||||||
|
|
||||||
|
From Obsidian v0.9.8, you can activate this plugin within Obsidian by doing the following:
|
||||||
|
|
||||||
|
- Open Settings > Third-party plugin
|
||||||
|
- Make sure Safe mode is **off**
|
||||||
|
- Click Browse community plugins
|
||||||
|
- Search for this plugin
|
||||||
|
- Click Install
|
||||||
|
- Once installed, close the community plugins window and activate the newly installed plugin
|
||||||
|
|
||||||
|
## From GitHub
|
||||||
|
|
||||||
|
- Download the Latest Release from the Releases section of the GitHub Repository
|
||||||
|
- Extract the plugin folder from the zip to your vault's plugins folder: `<vault>/.obsidian/plugins/`
|
||||||
|
Note: On some machines the `.obsidian` folder may be hidden. On MacOS you should be able to press `Command+Shift+Dot` to show the folder in Finder.
|
||||||
|
- Reload Obsidian
|
||||||
|
- If prompted about Safe Mode, you can disable safe mode and enable the plugin. Otherwise head to Settings, third-party plugins, make sure safe mode is off and enable the plugin from there.
|
||||||
|
|
||||||
|
### Updates
|
||||||
|
|
||||||
|
You can follow the same procedure to update the plugin
|
||||||
|
|
||||||
|
# Warning
|
||||||
|
|
||||||
|
This plugin comes with no guarantee of stability and bugs may delete data. Please ensure you have automated backups.
|
||||||
@ -0,0 +1,260 @@
|
|||||||
|
---
|
||||||
|
title: Building a Custom Malware Analysis Lab Enviornment
|
||||||
|
date: 06-05-2023
|
||||||
|
catagories: [malware, cybersecurity]
|
||||||
|
tags: [cybersecurity, Red Teaming]
|
||||||
|
---
|
||||||
|
|
||||||
|
```ad-note
|
||||||
|
https://www.sentinelone.com/labs/building-a-custom-malware-analysis-lab-environment/
|
||||||
|
```
|
||||||
|
|
||||||
|
## Introduction
|
||||||
|
|
||||||
|
Building the right [malware analysis](https://www.sentinelone.com/cybersecurity-101/malware-analysis/) environment is the first step for every malware researcher. When all system configurations and software installations are complete, you’re able to analyze and investigate malware properly. In this post, I wanted to share my own experiences and scripts to help ease the workload of setting up a malware environment to explore malicious software.
|
||||||
|
|
||||||
|
In this post, you will learn how to:
|
||||||
|
|
||||||
|
1. download, install and configure a free Windows 10 and a free REMnux Linux virtual machine
|
||||||
|
2. set up a virtual private network for communication between virtual machines
|
||||||
|
3. build a custom Windows malware environment with SentinelLabs RevCore Tools
|
||||||
|
4. learn how to capture network traffic from a Windows 10 virtual machine
|
||||||
|
|
||||||
|
## Installing Virtual Machines
|
||||||
|
|
||||||
|
When running multiple virtual machines, the host operating system will begin slowing down, so it is critical to set each virtual machine’s best requirements to optimize its performance. To set up the virtual machines in this post, I recommend that the Windows 10 virtual machine be set with the minimum requirements of two processor cores with 4GB of RAM and the Linux virtual machine with two processor cores with 2GB of RAM.
|
||||||
|
|
||||||
|
## Downloading a Free Windows 10 Installation
|
||||||
|
|
||||||
|
Microsoft provides a free virtual machine which is intended for testing IE and Edge web browsers. To download the Microsoft virtual machine go to [https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/](https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/) and download the MSEdge on Windows 10 zip file and select your preferred VM platform, currently I’m using VM Fusion.
|
||||||
|
|
||||||
|
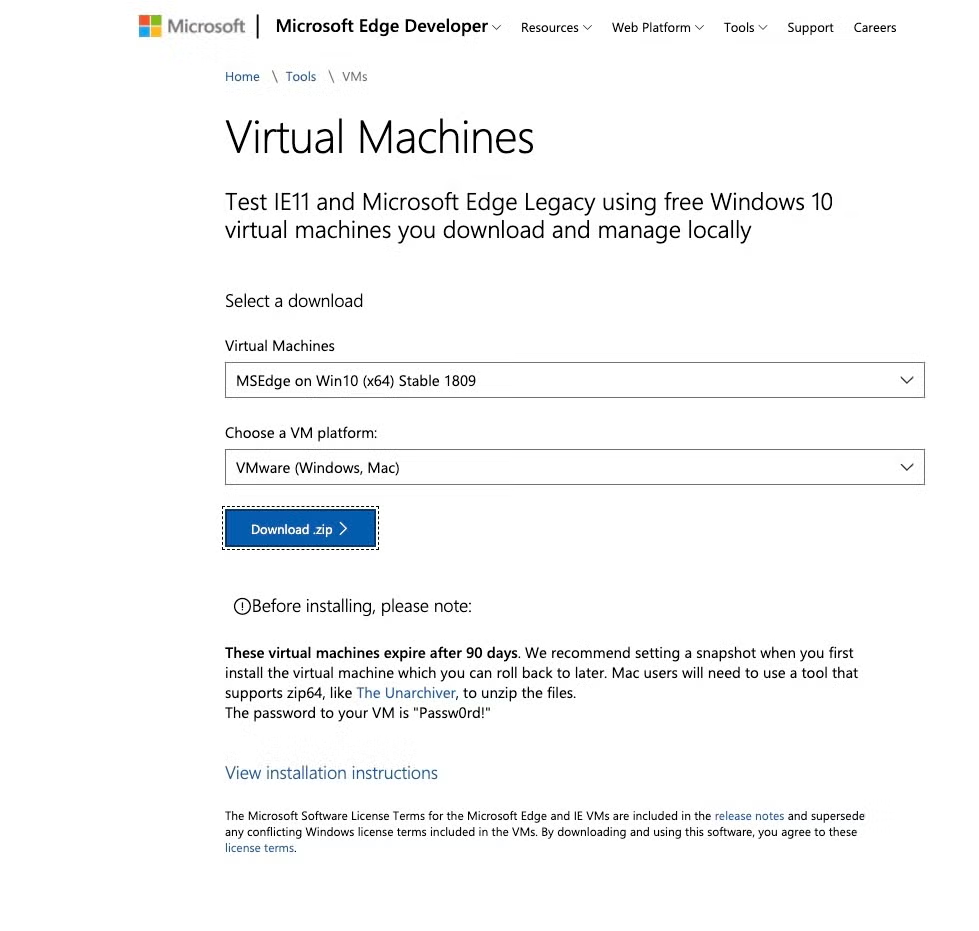
|
||||||
|
|
||||||
|
## Downloading REMnux Linux
|
||||||
|
|
||||||
|
The next virtual machine we want to download is REMnux Linux. The REMnux distro is a Linux distribution based on Ubuntu. It has excellent tools for exploring network interactions for behavioral analysis and investigating system-level interactions of malware. To download REMnux go to [https://docs.remnux.org/install-distro/get-virtual-appliance](https://docs.remnux.org/install-distro/get-virtual-appliance) and download the Virtual Machine platform of your choice.
|
||||||
|
|
||||||
|
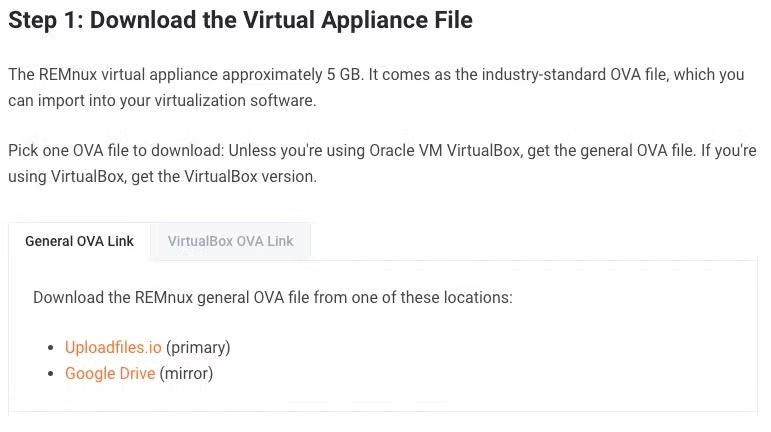
|
||||||
|
|
||||||
|
## Installing and Configuring a Private Isolated Custom Network
|
||||||
|
|
||||||
|
Creating an isolated, controlled network environment when analyzing malware is extremely important due to the level of interaction it gives you with malware. VMware Fusion gives you the capabilities to change key networking settings and add a virtual private network configuration to use for analysis between hosts. We will only add two virtual machines to this lab environment, but you can add many virtual machines to this network. The procedures to create this network is as follows:
|
||||||
|
|
||||||
|
- Select the tab **VMware Fusion->Preferences->Network**; click the lock icon to make changes
|
||||||
|
- Select the “**+**” button which creates a `vmnet#` under the **Custom** section.
|
||||||
|
- Do **_not_** select the _“Allow Virtual machines on this network to connect to external networks (using NAT)”_ option.
|
||||||
|
- Add a _Subnet IP_: I’ve entered `10.1.2.0`
|
||||||
|
- Click **Apply**
|
||||||
|
|
||||||
|
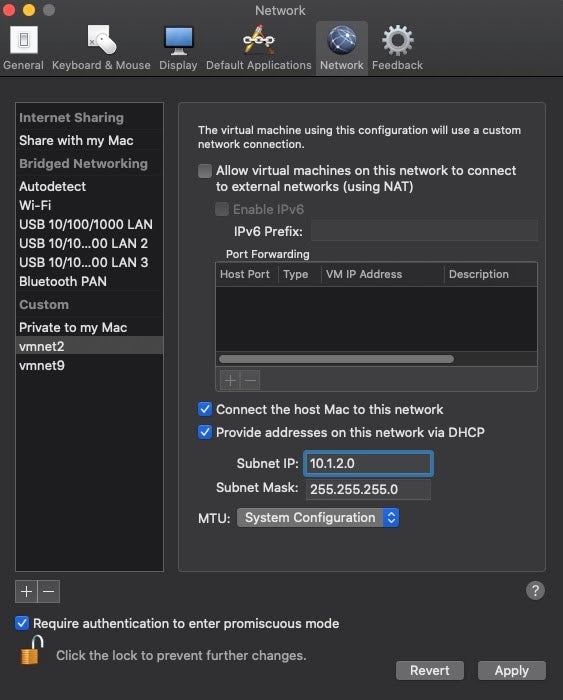
|
||||||
|
|
||||||
|
## Windows 10 Setup
|
||||||
|
|
||||||
|
Once you’ve created a custom network and both virtual machines have been downloaded, begin by unzipping the MSEdge Windows 10. Since I’m using VMware Fusion, I will go through how to import the virtual image; the process for importing the virtual machine with other platforms is similar.
|
||||||
|
|
||||||
|
Open up VMware Fusion and follow these steps:
|
||||||
|
|
||||||
|
1. After the zip has been unpacked enter the MSEdge-Win10-VMware folder.
|
||||||
|
2. Select in VMware Fusion **File->Import MSEdge_Win10_VMware**, hit **Continue** and save the Virtual Machine; it will take a few minutes to import the image.
|
||||||
|
3. Click on **Customize Settings** after the image has been imported.
|
||||||
|
4. Click into the **Processors & Memory** tab and confirm that the settings has two processor cores and the memory is 4096MB.
|
||||||
|
5. Before powering on the MSEdge Win10 virtual machine, take a snapshot and name it something like “VM Clean Import”.
|
||||||
|
6. When starting the virtual machine, if prompted to upgrade the virtual machine to greater feature compatibility support, choose **Upgrade**.
|
||||||
|
7. The password to the virtual machine is `Passw0rd!`
|
||||||
|
8. Open the command prompt to activate the virtual machine, type `slmgr.vbs /ato`.
|
||||||
|
9. When prompted, install VMware’s “Virtual Tools” and reboot.
|
||||||
|
10. Once the virtual machine has rebooted, complete login and immediately take a snapshot. Give it a descriptive name, such as “Activation and VM Tools Install” snapshot.
|
||||||
|
|
||||||
|
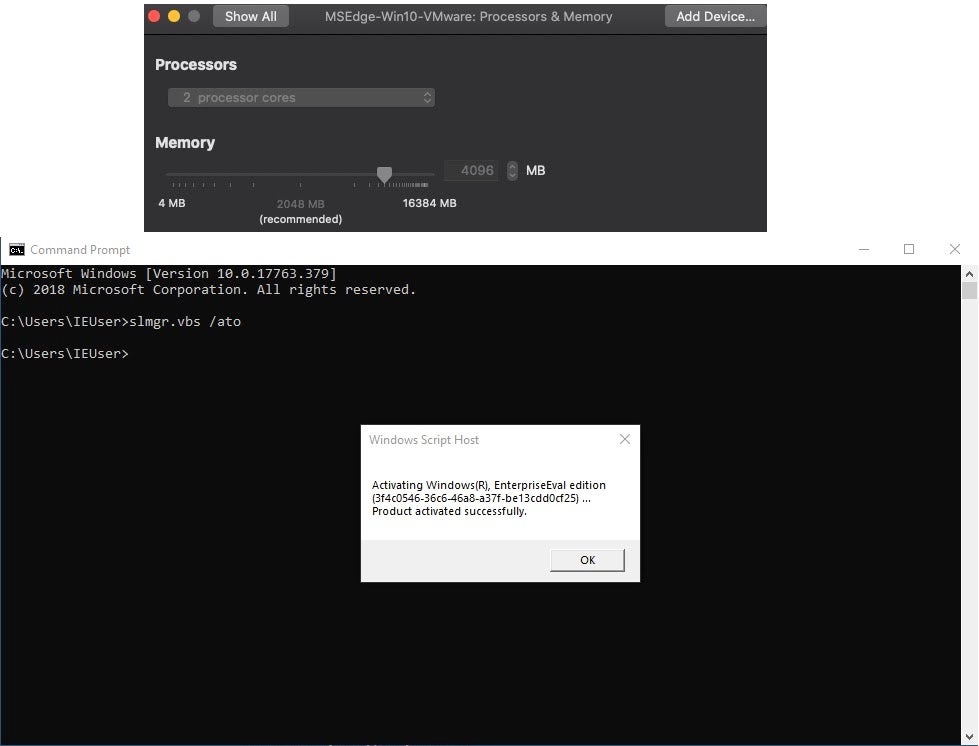
|
||||||
|
|
||||||
|
## REMnux Setup
|
||||||
|
|
||||||
|
The REMnux virtual machine downloads as an `.ova` file. I recommend you browse to [docs.REMnux.org](https://docs.remnux.org/install-distro/get-virtual-appliance) to confirm the hash of the downloaded OVA file.
|
||||||
|
|
||||||
|
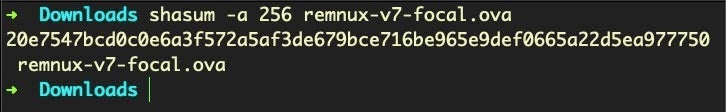
|
||||||
|
|
||||||
|
If you are using VirtualBox, you can just import REMnux, but if you are using VMware Fusion or VMware Workstation, follow these instructions to import the REMnux:
|
||||||
|
|
||||||
|
1. Select **File->Import->Choose File…** and select _remnux-v7_, hit **Continue** and then **Save**.
|
||||||
|
2. When the import is complete, click on **Customize Settings**.
|
||||||
|
3. Click into the **Processors & Memory** pane under _System Settings_ and leave the settings with two processor cores; reduce the memory from 4096MB to 2048MB.
|
||||||
|
4. For the REMnux network configuration, the setup is slightly different. We want to add an additional network adapter._Note_: There are multiple reasons why I configure this virtual machine this way. If I need to update or download other software having the network adapter configured saves me time; the second is if I want to allow malware callouts.Once the import is complete and you’re in the “Settings” menu, select **Network Adapter**. The next step is to click **Add Device…** and select **Network Adapter** and **Add…**. Make sure the _Share with my Mac_ radio button is set. Return to the main “Settings” panel and select **Network Adapter 2**. Click the _vmnet2_ radio button, then choose **Show All** to go back to Settings.
|
||||||
|
5. When starting the REMnux virtual machine, if prompted to upgrade the virtual machine to greater feature compatibility support, choose **Upgrade**.
|
||||||
|
6. Once REMnux boots, the credentials are: Username: `remnux` Password: `malware`.
|
||||||
|
7. I always change the password on my virtual machines:
|
||||||
|
1. $passwd
|
||||||
|
UNIX password: malware
|
||||||
|
Enter new UNIX password: (your choice)
|
||||||
|
|
||||||
|
8. The next step is to configure the network settings. If you type `ifconfig -a` you should see two network adapters:
|
||||||
|
1. Select NAT for the first network adapter. The virtual machine will get an address on that network from the VMware virtual DHCP server. You can ping google to see if you have connectivity or open the Firefox browser and connect to any website to confirm that you have internet access. If you do not, then type this command in terminal: `$ sudo dhclient -r` This should allow you to fetch an IP.
|
||||||
|
2. For the second adapter, ens37, type in this command:`$ sudo ifconfig ens37 10.1.2.1 netmask 255.255.255.0`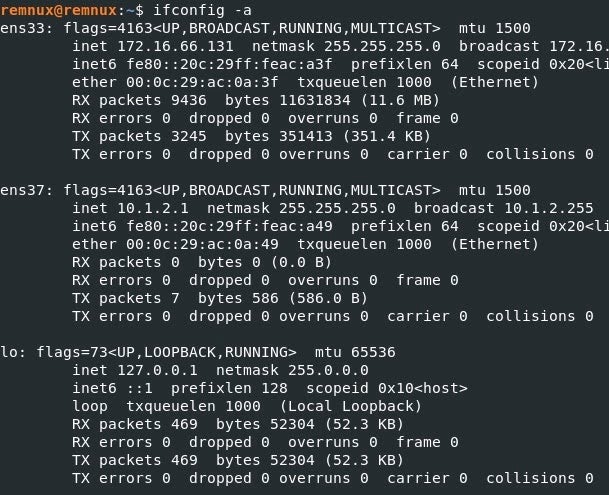
|
||||||
|
9. Hit the “Snapshot” button and name it something like “Clean Snapshot”.
|
||||||
|
10. Update and upgrade REMnux:`$ sudo apt-get update; sudo apt-get upgrade`
|
||||||
|
|
||||||
|
## Installing SentinelLabs RevCore Tools
|
||||||
|
|
||||||
|
One of the reasons I wanted to create a SentinelLabs VM Bare Bones malware analysis toolkit was that when installing FlareVM, I find it contains many tools that I do not use, and it takes a minimum of 40 minutes to install. I wanted to create a script of the core tools and system configurations that I need to be able to analyze malware.
|
||||||
|
|
||||||
|
Follow this procedure to instal SentinelLabs RevCore Tools on MSEdge WIndows 10:
|
||||||
|
|
||||||
|
1. Browse to the [SentinelLabs RevCore Tools](https://github.com/SentineLabs/SentinelLabs_RevCore_Tools) github page and download the zip.
|
||||||
|
2. Unzip it and drag the `SentinelLabs_RevCore_Tools_codeSnippet.ps1` script onto your desktop.
|
||||||
|
3. If you are using the free downloaded Windows 10 virtual machine that I’ve mentioned above go to Step 4; if you are using your own Windows virtual machine continue with these substeps:
|
||||||
|
1. Instead of dragging just the `SentinelLabs_RevCore_Tools_codeSnippet.ps1`, drag the entire folder onto your virtual machine desktop.
|
||||||
|
2. Open the `SentinelLabs_RevCore_Tools_codeSnpippet.ps1` file and modify line 4 after `-PackageName.` You will modify the url and change it to the directory location on your desktop. E.g., `'https://raw.githubusercontent.com/SentineLabs/SentinelLabs_RevCore_Tools/master/SentinelLabs_RevCore_Tools.ps1'` to `'c:UsersyourUsernameDesktopSentinelLabs_RevCore_Tools-mainSentinelLabRevCoreTools.ps1'``;`
|
||||||
|
3. The final thing to do is to modify the `SentinelLabsRevCoreTools.ps1.` On lines 105-117, replace `IEUser` with the User profiles name you are using. Save all files and run the script. E.g.,
|
||||||
|
|
||||||
|
Install-ChocolateyShortcut -ShortcutFilePath "C:\Users\IEUser\Desktop\HxD.lnk" -TargetPath "C:\Program Files\HxD\HxD.exe"
|
||||||
|
|
||||||
|
Install-ChocolateyShortcut -ShortcutFilePath "C:\Users\YourUser Profile\Desktop\HxD.lnk" -TargetPath "C:\Program Files\HxD\HxD.exe"
|
||||||
|
|
||||||
|
4. Go to Step 5.
|
||||||
|
4. In the Windows 10 search bar, type `powershell`, right click and run as administrator. Browse to the location of the `SentinelLabs_RevCore_Tools_codeSnippet.ps1` powershell script, then run the script:
|
||||||
|
`.SentinelLabs_RevCore_Tools_codeSnippet.ps1`.
|
||||||
|
5. The script will cause two automatic reboots, and you’ll need to log in again with your user password after each. The first reboot will continue disabling various system services that could otherwise hinder your malware analysis and continue to install the core tools. After the second reboot, the script will finalize and confirm all of the configurations and installations.The installed tools and modified system configurations are listed below. Don’t forget to take a snapshot when it’s finished and you’ve reached the “Type ENTER to exit” point.
|
||||||
|
|
||||||
|
1. **Tools:**
|
||||||
|
Checksum, 7zip, Process Explorer, Autoruns, TCPview, Sysmon, HxD, PEbear, PEStudio, PEsieve, Cmder, NXlog, X64dbg, X32dbg, Ollydbg, IDA-Free, Cutter, Ghidra, Openjdk11, Python3, PIP, PIP pefile, PIP YaraA tool that I frequently use is [Hiew](http://www.hiew.ru/), Chocolatey does not have Hiew in its collection. My recommendation is to download and try out the free version, once you see the power of Hiew you should definitely purchase lifetime access because it is worth every penny.
|
||||||
|
2. **System Configuration:**
|
||||||
|
Disabling – Bing Search, Game Bar Tips, Computer Restore, UAC, Update, Firewall, Windows Defender, Action Center
|
||||||
|
Set Window Theme, Set Wallpaper, Create Shortcuts For Tools
|
||||||
|
|
||||||
|
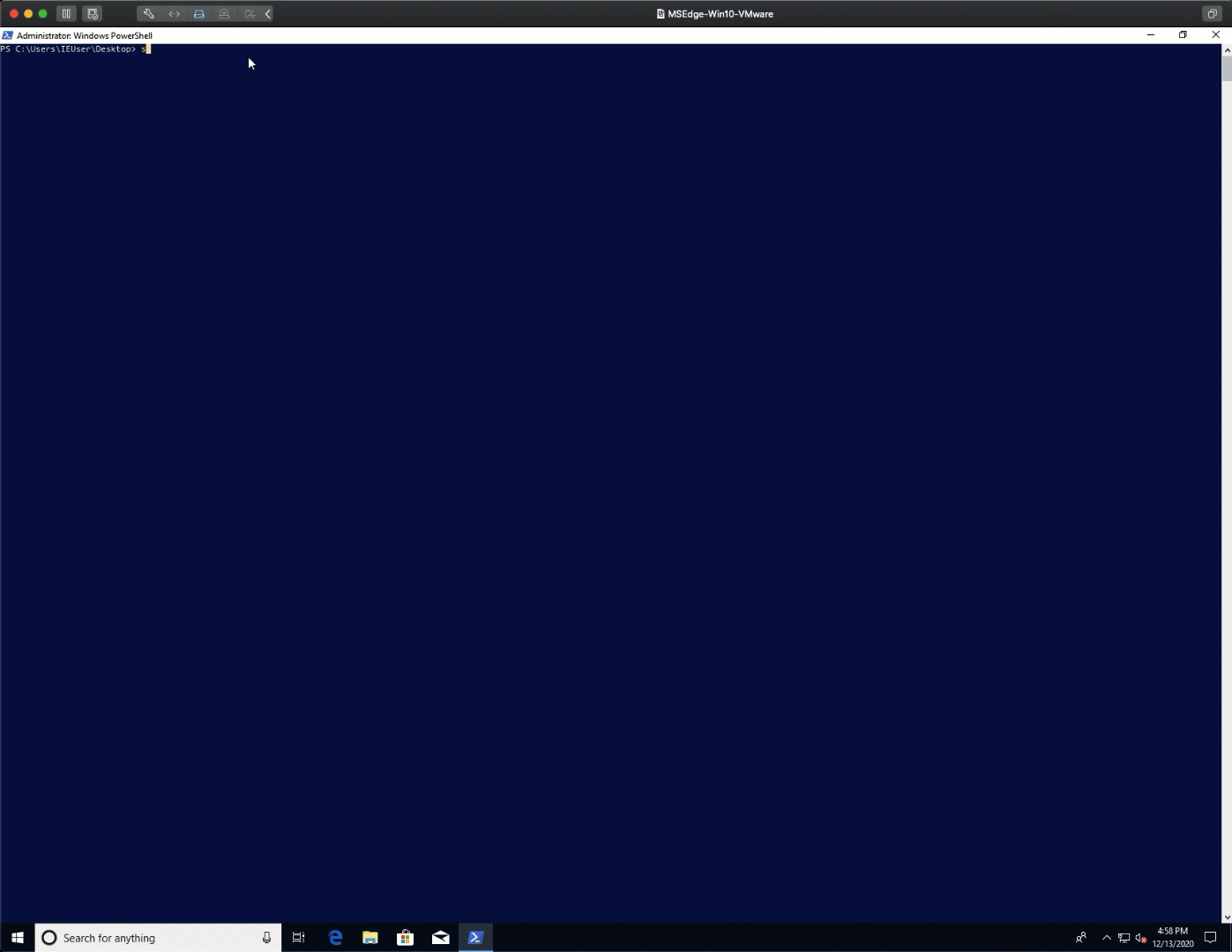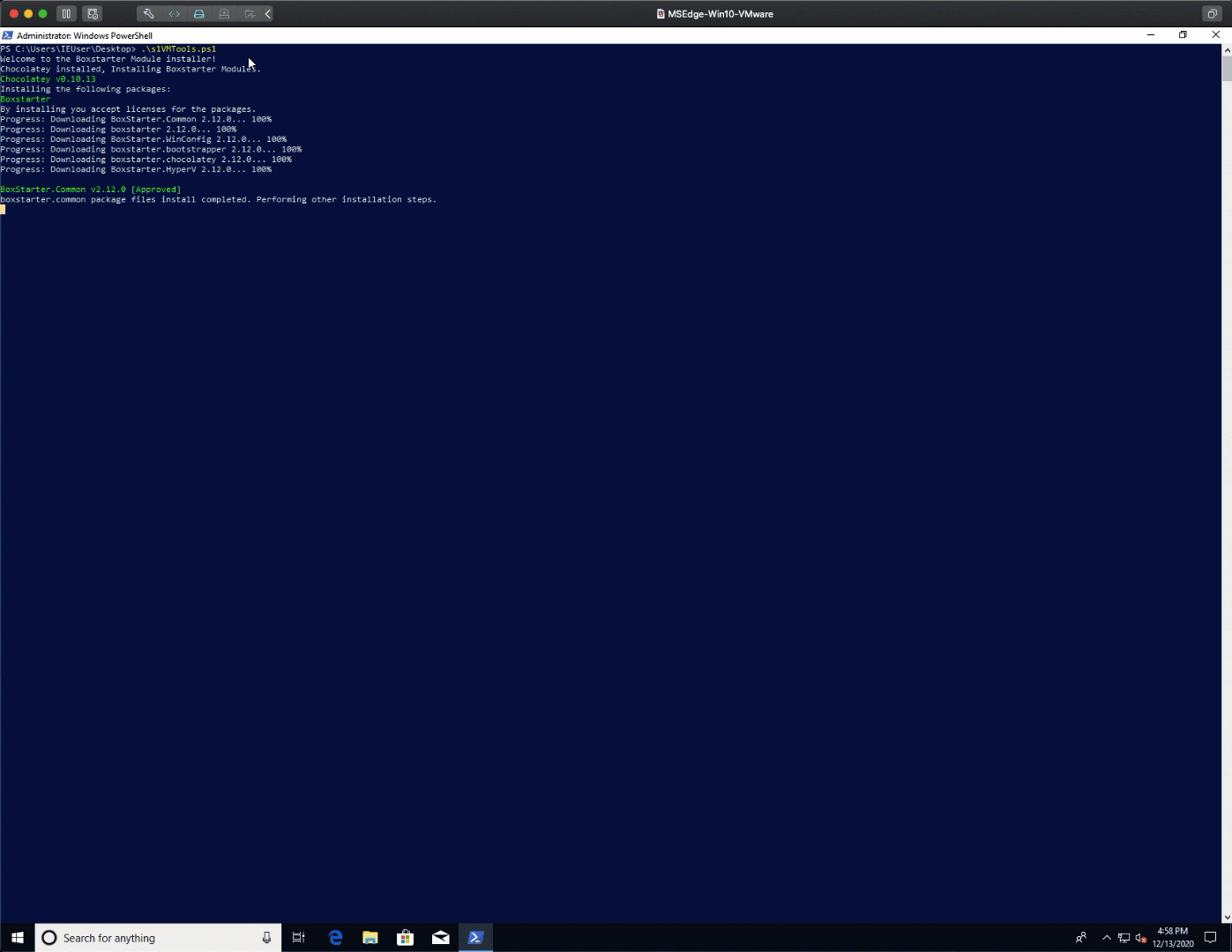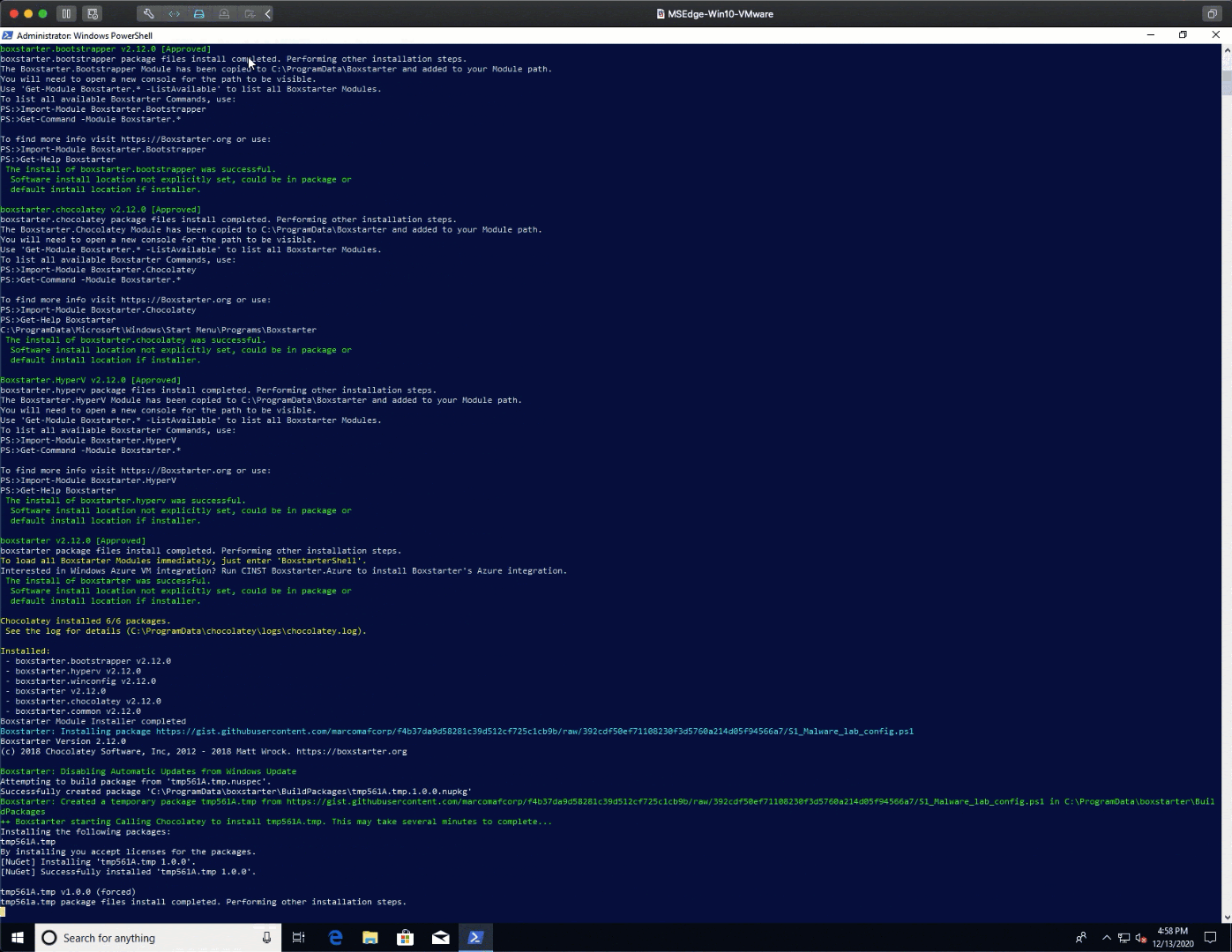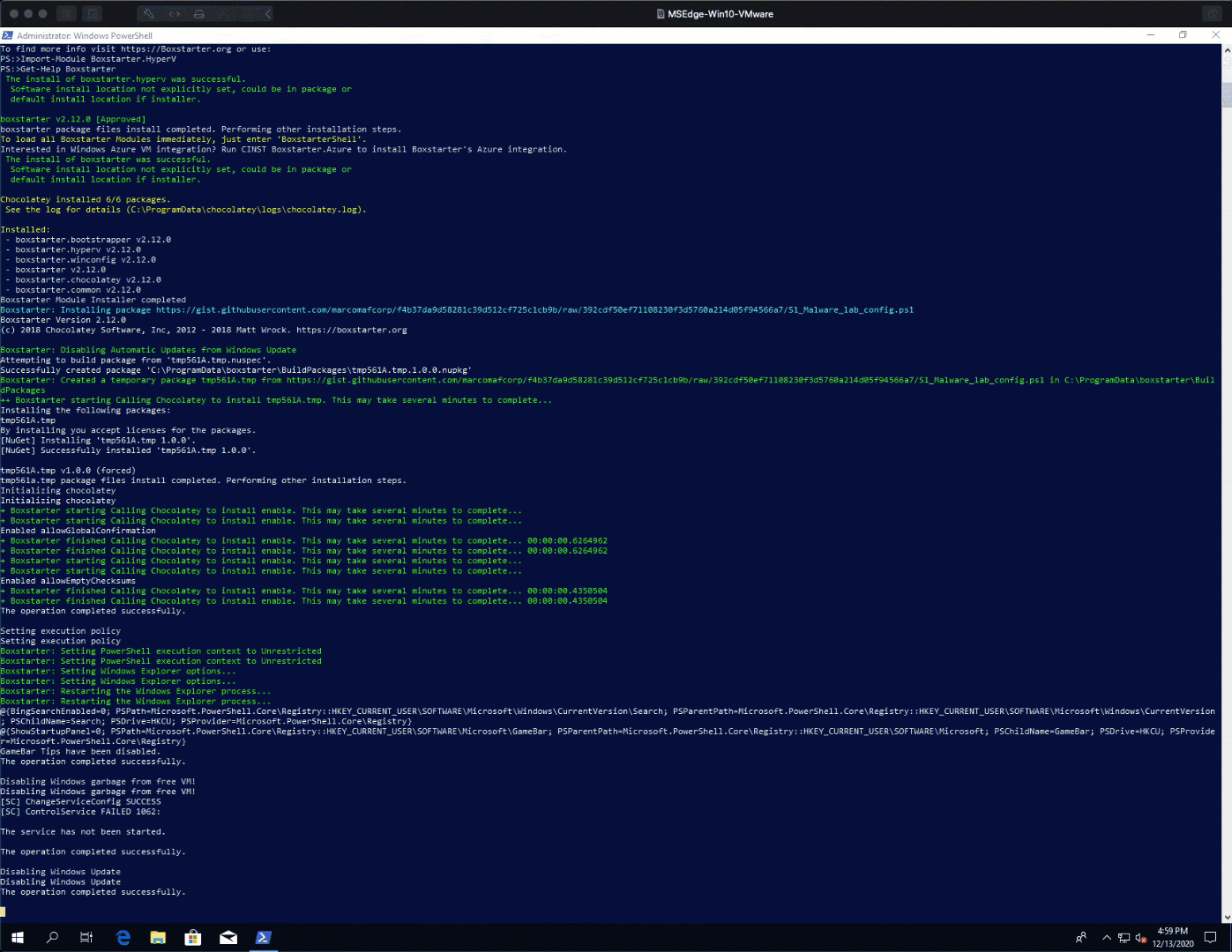
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## Network Traffic Collection
|
||||||
|
|
||||||
|
When analyzing malware, often the malware operation and the C2s are still active, so an excellent way to stay under the radar is to run malware in a controlled environment. Analyzing network traffic is a trivial process in detecting malicious software callouts in real time network traffic. This section will help you configure your virtual machines to capture the detonated malicious software’s network traffic or statically step through debugged code, which allows your investigation to understand the potential threat at hand.
|
||||||
|
|
||||||
|
The first thing that must be configured is the virtual private network communication between the MSEdge Windows 10 and REMnux:
|
||||||
|
|
||||||
|
1. On the Windows 10 virtual machine, select the custom `vmnet2` network (**Virtual Machine->Network Adapter->Custom (vmnet2)**).
|
||||||
|
2. On the Windows 10 VM, right click on the network adapter in the taskbar and choose _Open Network & Internet settings_.
|
||||||
|
3. Select _Ethernet_ and click on **Change adapter options**.
|
||||||
|
4. Right click on _Ethernet0_ and select **Properties**.
|
||||||
|
5. Double click on _Internet Protocol Version 4 (TCP/IPv4)_.
|
||||||
|
6. Click the radio button to select “_Use the following IP address:_”, then add the IP address, Subnet mask, Default gateway, and Preferred DNS server as follows:
|
||||||
|
1. IP Address: 10.1.2.100
|
||||||
|
2. Subnet mask: 255.255.255.0
|
||||||
|
3. Default Gateway: 10.1.2.1
|
||||||
|
4. Click the radio button to select _“Use the following DNS server address:”_ and add:
|
||||||
|
- Preferred DNS Server: 10.1.2.1
|
||||||
|
5. Click **OK** to complete configuration of the network settings.
|
||||||
|
|
||||||
|
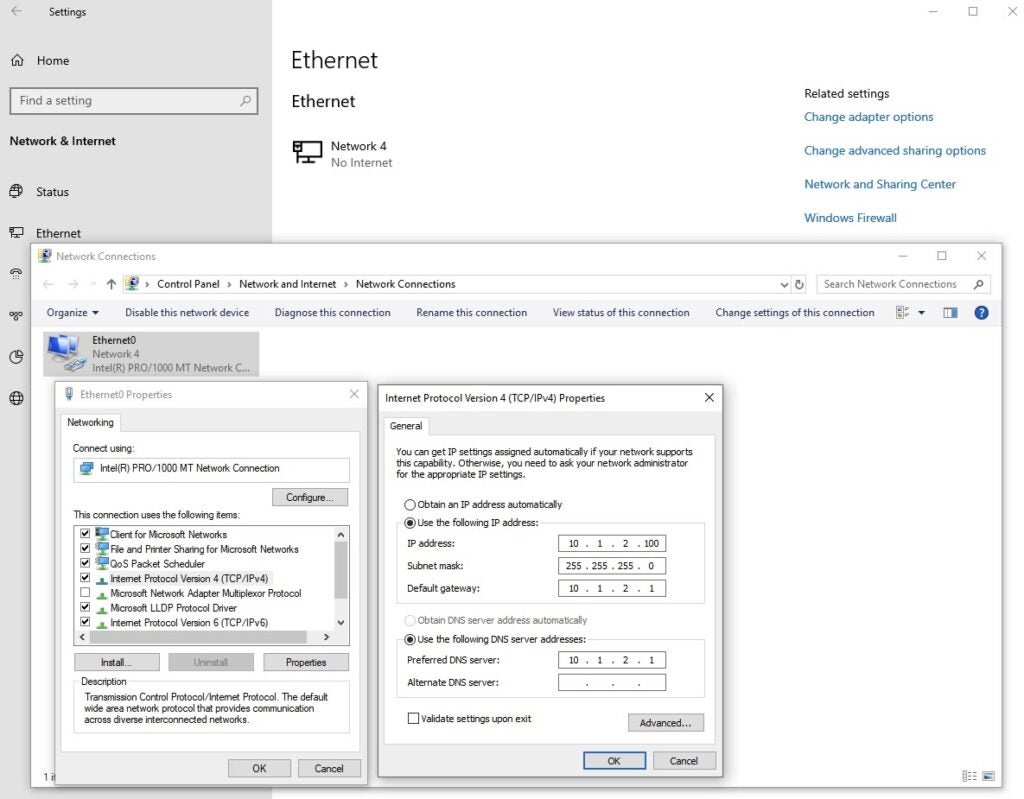
|
||||||
|
|
||||||
|
The REMnux adapter for the virtual private network has already been configured from the previous section.
|
||||||
|
|
||||||
|
Now that the virtual machines are networked and can communicate with each other, it is time to configure a few tools on the REMnux virtual machine to capture traffic.
|
||||||
|
|
||||||
|
Installed on REMnux are various tools you can use to capture network traffic. We will configure Burp Suite and INetSim. Burp Suite is typically used to test web application firewalls, but in our case we want to configure it so that when Windows 10 detonates malware, it will try to establish a connection to a domain or C2. The traffic will potentially use HTTPS and pass through Burp Suite, which will be bound to INetSim. INetSim is a software suite that simulates common services for lab environments to analyze malware’s network behavior.
|
||||||
|
|
||||||
|
## Burp Suite Configuration
|
||||||
|
|
||||||
|
The Burp Suite setup is straightforward, but there are a couple of steps that we must configure before we can begin using it.
|
||||||
|
|
||||||
|
- Open a command prompt and type: `$ sudo Burp Suite`.
|
||||||
|
- select _Temporary project_, then hit **Next** and then **Start Burp**.
|
||||||
|
- Select the **Proxy** tab and then “Options”. Under _Proxy Listeners_, select the default interface and click the **Edit** button.
|
||||||
|
- Under the **Binding** tab, set _Bind to address_ to _Specific address: 10.1.2.1_ and click **OK**.
|
||||||
|
|
||||||
|
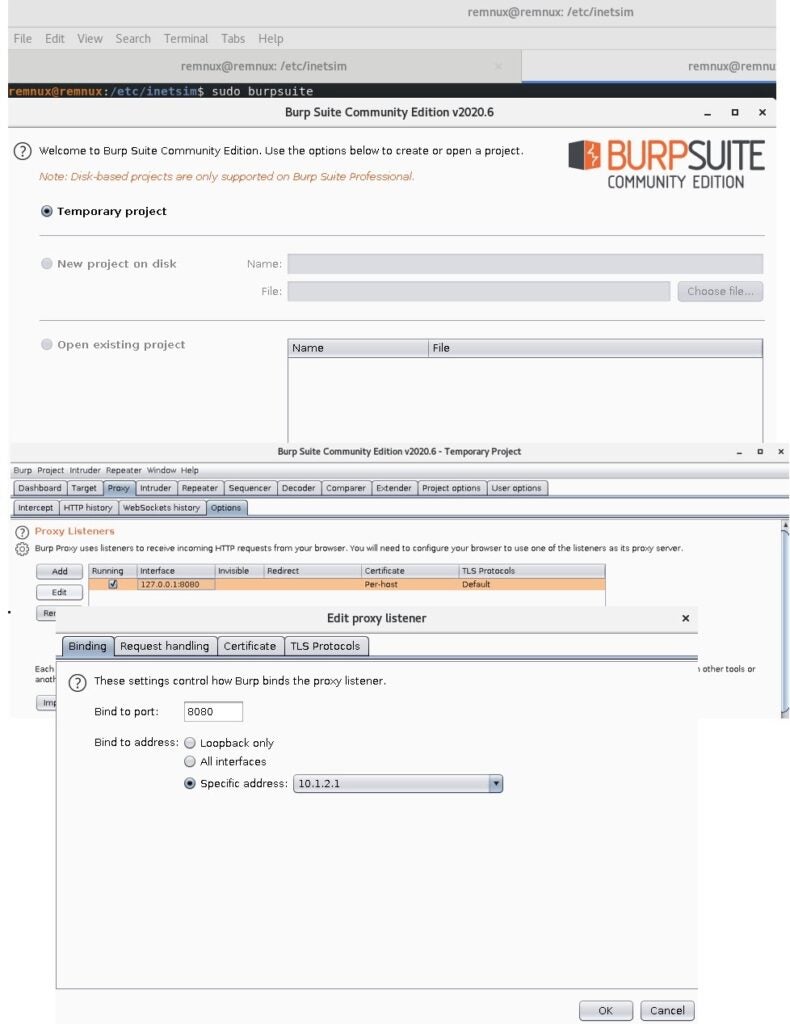
|
||||||
|
|
||||||
|
- IMPORTANT STEP:
|
||||||
|
- Go back to you MSEDGE Windows 10 virtual machine and open up the Edge browser.
|
||||||
|
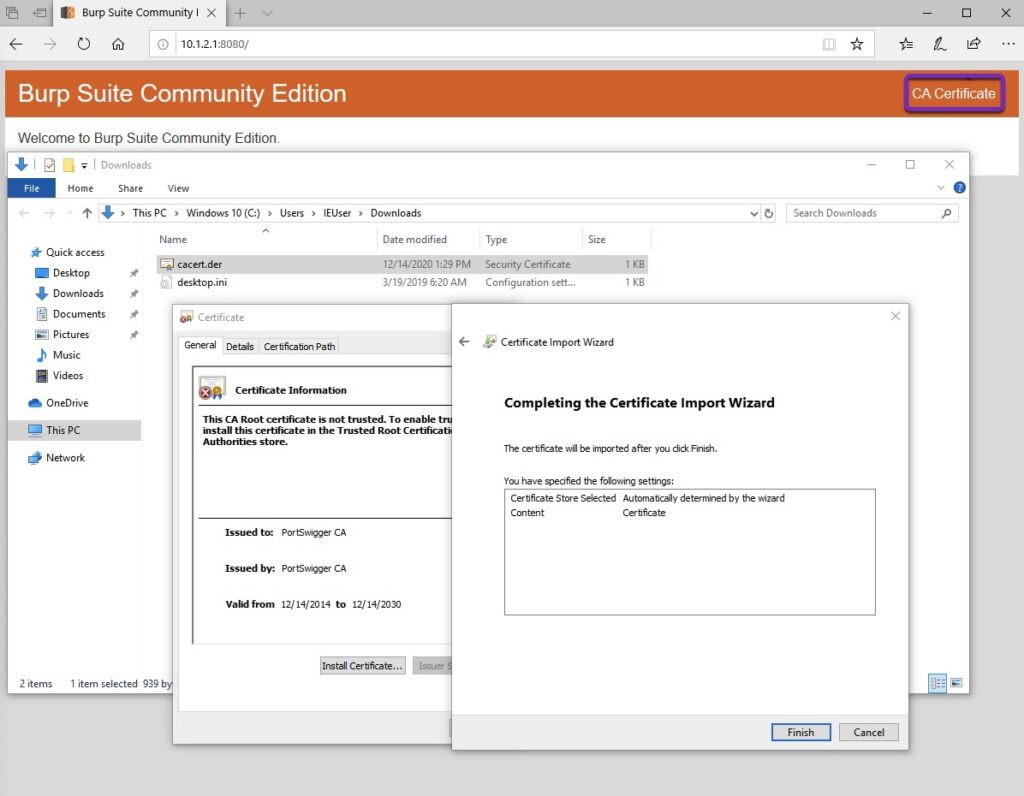
- Type in the address bar: [`http://10.1.2.1:8080`](http://10.1.2.1:8080/). You should see “Burp Suite Community Edition”.
|
||||||
|
- Download the CA Certificate on the top right side of the page.
|
||||||
|
- Open the location of the file and double click on the certificate file.
|
||||||
|
- Select `Install Certificate...`.
|
||||||
|
- Select `Current User` as the Store Location and click `Next`.
|
||||||
|
- Select `Automatically select the certificate store based on the type of certificate`. Click `Next` and then click `Finish`.
|
||||||
|
- Go into the settings of the EDGE Browser and disable all security functionalities; this will help with testing the connection to INetSim in the next section.
|
||||||
|
- Make sure you take a snapshot.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
Go back to the REMnux virtual machine. You should still be in Burp Suite Proxy tab, _Edit proxy listener_ options.
|
||||||
|
|
||||||
|
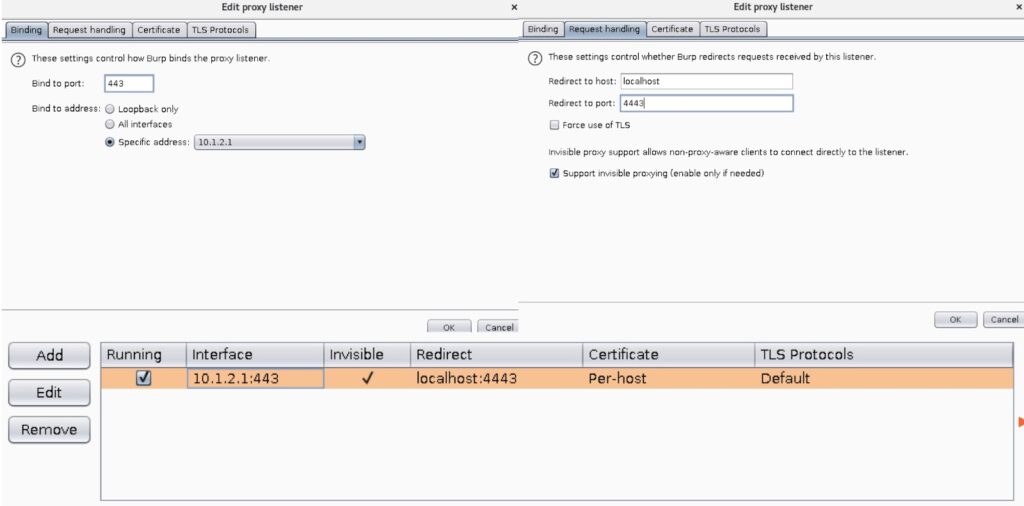
- Under the **Request handling** tab, set _Redirect to host_ to `localhost` and _Redirect to port_ to `4443`. Select _support for invisible proxying_.
|
||||||
|
- Now go to the **Intercept** tab and make sure _intercept_ is **off**.
|
||||||
|
- Under **Proxy Listeners**, select the default and click `Edit`
|
||||||
|
- Under the Binding tab, `Bind to address: Specific address: 10.1.2.1` should still be kept, but change the _Bind_ to port `443`
|
||||||
|
- Click on the **Request handling** tab and set the _Redirect to host_ option to `localhost` and `Redirect to port` to `4443.`
|
||||||
|
- Select the _Support invisible proxying (enable only if needed.)_ and click **OK**.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
## INetSim Configuration Setup
|
||||||
|
|
||||||
|
REMnux has INetSim preinstalled. Use your favorite text editor and open up the `inetsim.conf` file located in `/etc/inetsim/`. Follow the steps to configure INetSim:
|
||||||
|
|
||||||
|
1. `$ sudo vi /etc/inetsim/inetsim.conf` and enable all the services by uncommenting out the services by deleting the `#` character._Pro Tip:_ Be aware that malware could potentially detect it is running in a virtual environment by checking whether everything in this file is uncommented. I have yet to come across this, but it is good to be aware of the possibility. You could take a more conservative approach and only uncomment services you intend to use.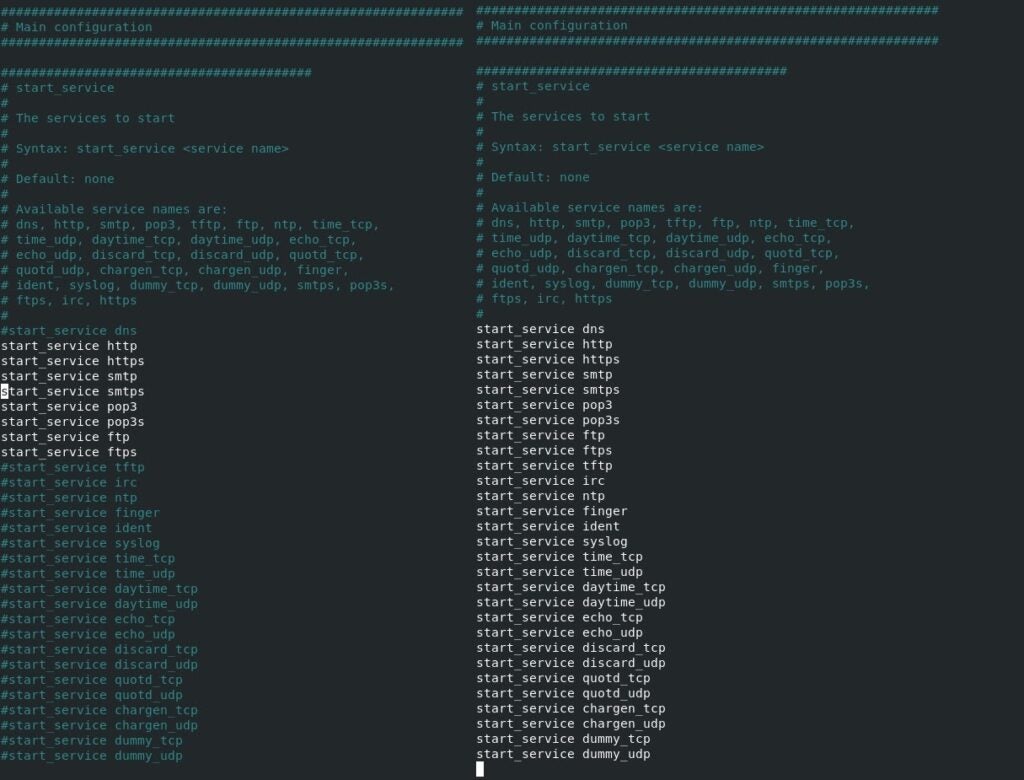
|
||||||
|
2. The next step is to bind the REMnux network adapter IP in the `inetsim.conf` file. The next section after the services menu is the `service_bind_address`. Uncomment the `#` and change the default IP address from 10.10.10.1 to `0.0.0.0`.
|
||||||
|
3. Scroll down to the `dns_default_ip` section, uncomment the `#` and change the IP address from 10.10.10.1 to `10.1.2.1`.
|
||||||
|
4. The last thing to do is to bind the HTTPS port so Burp Suite can route the traffic to the port 4443. Scroll down to the `https_bind_port` section, uncomment the `#` character and replace 443 with `4443`.
|
||||||
|
5. Save the changes and exit the editor.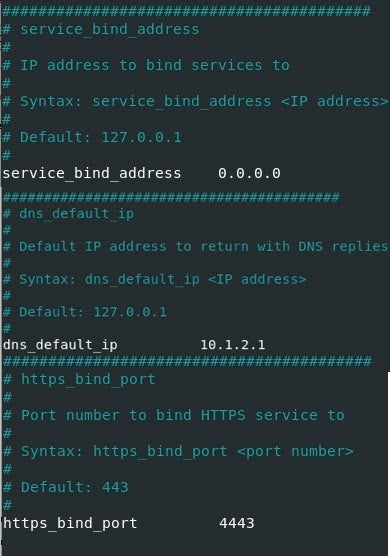
|
||||||
|
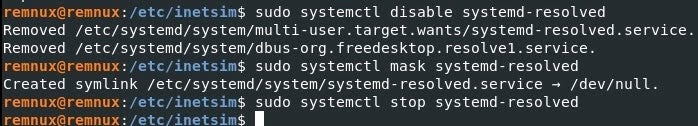
6. The next step is to run the following commands which are VERY IMPORTANT to execute or INetSim will not work correctly. Ubuntu has a system-resolved system service which provides network name resolution to local applications. This conflicts with INetSim so we need to disable the service.We have to disable `system-resolve` and also mask it so that it doesn’t auto start on reboot. Finally, we will stop the service.
|
||||||
|
|
||||||
|
$ sudo systemctl disable systemd-resolved
|
||||||
|
$ sudo systemctl mask systemd-resolved
|
||||||
|
$ sudo systemctl stop systemd-resolved
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
7. The final step is to run INetSim:
|
||||||
|
`$ sudo inetsim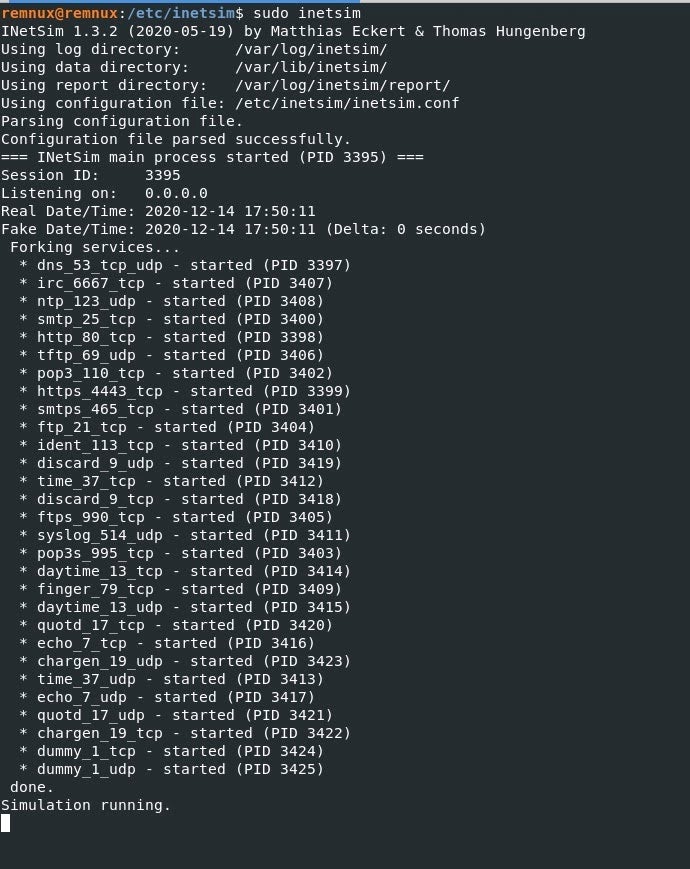`
|
||||||
|
|
||||||
|
To test network connectivity from your Windows 10 virtual machine, open a command prompt and ping 10.1.2.1, then open Edge browser and type 10.1.2.1. You should see the following message “_This is the default HTML page for INetSim HTTP server fake mode._”
|
||||||
|
|
||||||
|
The final test is to make sure the DNS is working correctly and serving up requests. For this example, I type in the search bar `https://www.mymaliciousdomain.com/malwaretrojan.exe`. If everything is working, you should see a web page warning that the requested site is not secure.
|
||||||
|
|
||||||
|
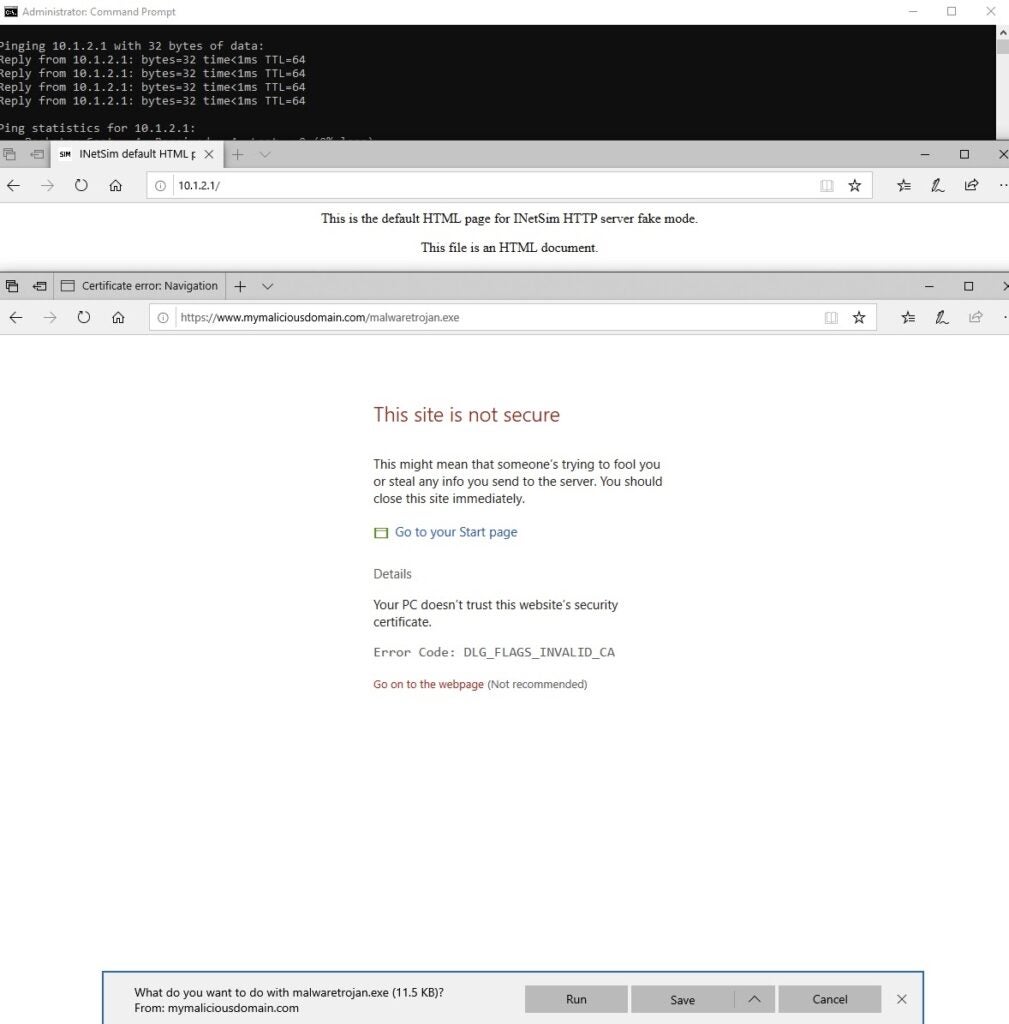
|
||||||
|
|
||||||
|
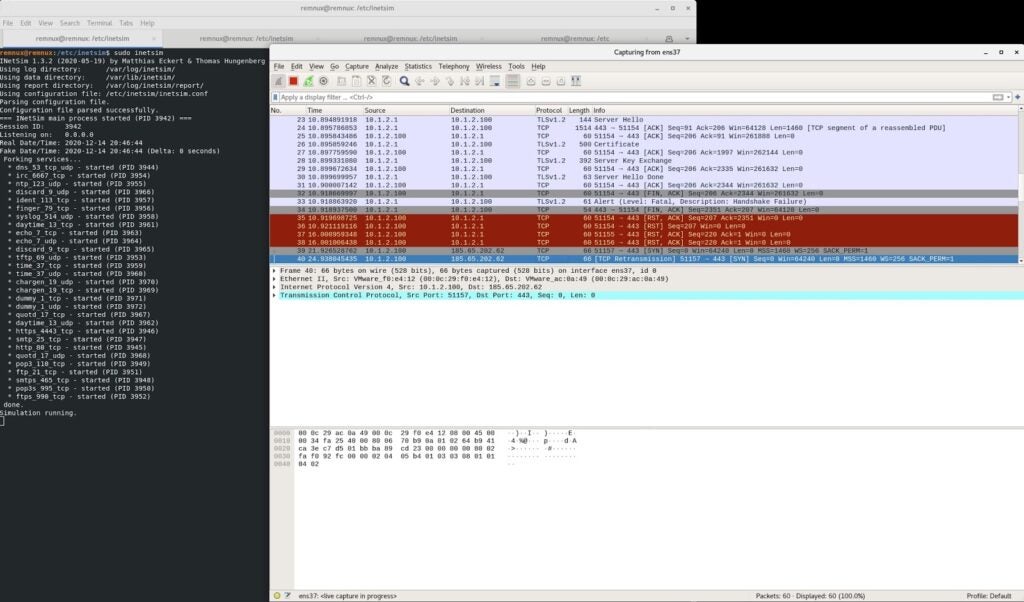
I also like using Wireshark to capture packets to analyze the pcaps when investigating malware.
|
||||||
|
|
||||||
|
Open a new tab in your terminal in REMnux and type `$ wireshark`.
|
||||||
|
|
||||||
|
Once the application has opened, click on the shark fin icon on the far left of the toolbar to begin capturing packets.
|
||||||
|
|
||||||
|
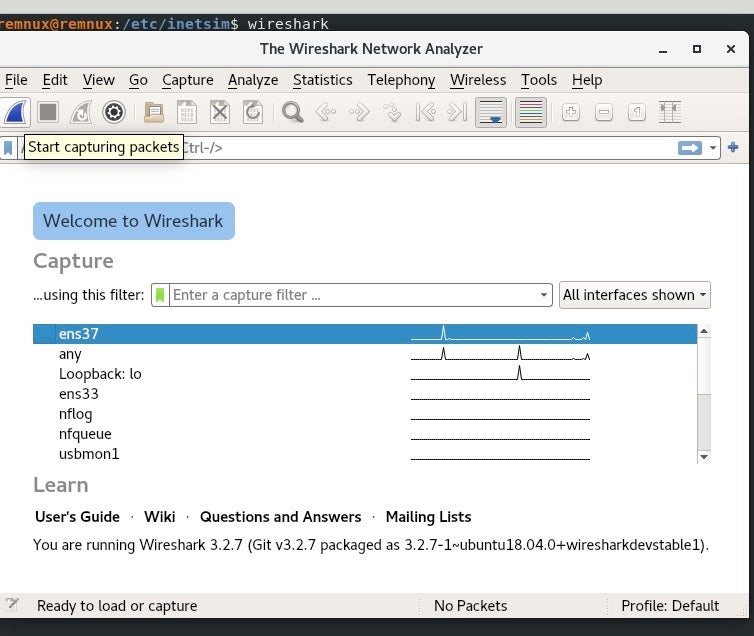
|
||||||
|
|
||||||
|
## Detonating Malware
|
||||||
|
|
||||||
|
When malware is executed, it usually makes some request to a domain or IP address. INetSim helps with this by spoofing the responses to the malware that is waiting for a response. An example would be if malware was executed and reached out to a domain and will not proceed without a response unless the conditions were met, which is the response. If the malware doesn’t receive the response, it would terminate and not continue its malicious actions. This is where the live environment assists us with responding to callouts and capturing network traffic.
|
||||||
|
|
||||||
|
For the final step of the lab environment setup, we will detonate a notorious binary trojan (or any malware you choose) to test the configuration is working correctly.
|
||||||
|
|
||||||
|
I’m testing with a Trickbot binary (**SHA256:** `49d95cae096f7f73b3539568b450076227b4ca42c0240044a7588ddc1f1b6985`). I’ve opened Process Explorer and TCPView to monitor the execution of this variant of Trickbot.
|
||||||
|
|
||||||
|
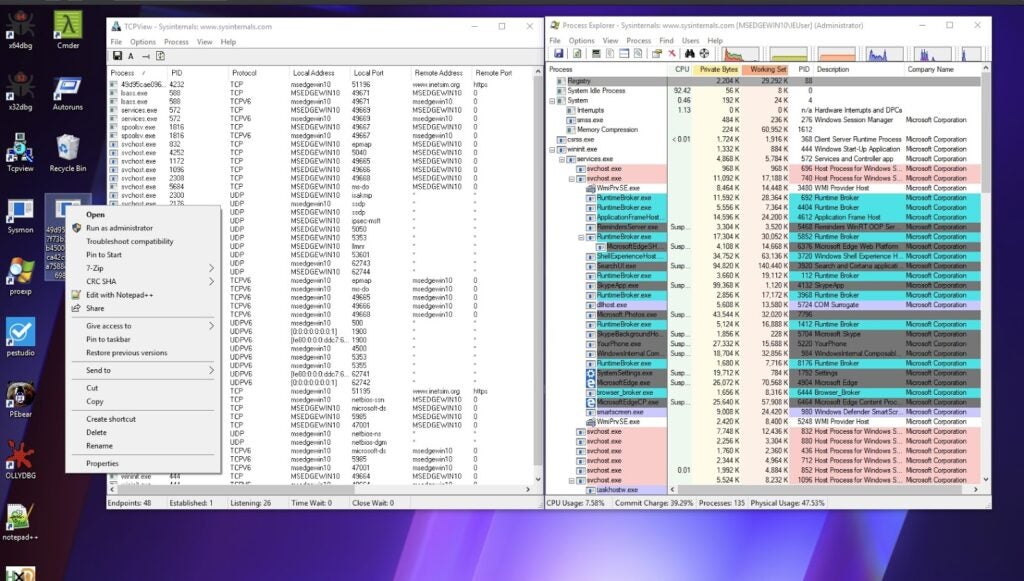
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
Detonating malware can save a lot of time before diving deep into reverse engineering as it allows you to gather insight and create an unbiased hypothesis. In this example, when we detonated this trickbot sample there were three callouts that stuck out:
|
||||||
|
|
||||||
|
- The callouts were to fetch files from Microsoft Updates site; these cab files called were automatic updaters of untrusted certificates. A certificate trust list is a predefined list of items signed by a trusted entity. These requested cab files are used to update and expand the existing functionality by adding known untrusted certificates to the untrusted certificate store by using a certificate trust list.
|
||||||
|
|
||||||
|
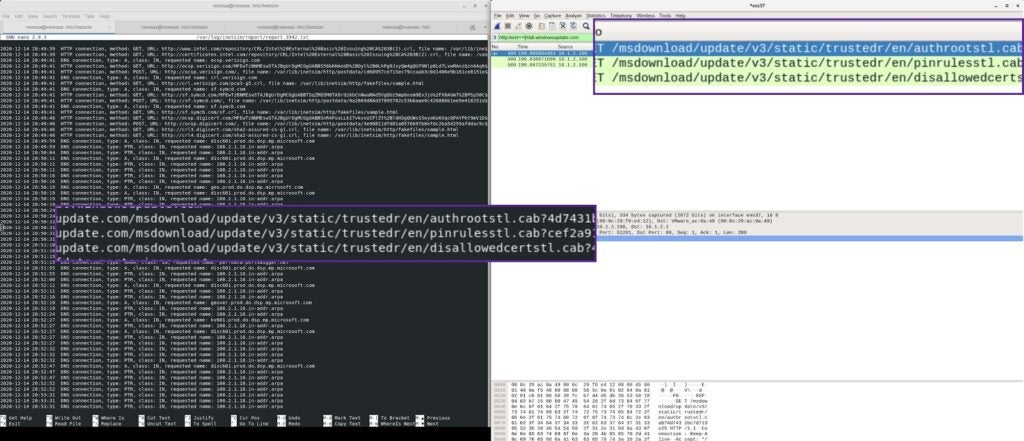
|
||||||
|
|
||||||
|
Although Trickbot is one of the more prolific malware strains today and is more complex than a few callouts, it is a good starting point if you are in the beginning stages of research and have never encountered this binary.
|
||||||
|
|
||||||
|
I’ve been successfully using this lab setup for many years. A real-world example of using this lab setup occurred when I was brought in to help with an incident at short notice back in 2016. I didn’t have time for an initial triage of the binary as I was joining a war room call for the briefing by the investigation team lead. I started both VMs from snapshots and detonated the binary while being brought up to speed about the incident. Within 5 minutes, I informed the investigation lead about an IP that the specific binary was calling out to, which was enough to give the threat hunters a place to begin. After the war room call, I started reversing the malware and extracting additional IOCs and TTPs.
|
||||||
|
|
||||||
|
## Conclusion
|
||||||
|
|
||||||
|
A lab environment setup and configuration varies during malware analysis. When analyzing malware you need different tools to dissect and do deep analysis. I hope the SentinelLabs RevCore Tools and configurations in this setup assists, but there might be a time that you need to analyze something different, like a dot net file, and may need an additional tool to fully disassemble the binary. The journey of reversing malware is a marathon and not a sprint; growing your skill and learning from every malware analyzed should be the goal.
|
||||||
|
|
||||||
|
## Resources
|
||||||
|
|
||||||
|
[https://support.microsoft.com/en-us/help/2677070/an-automatic-updater-of-untrusted-certificates-is-available-for-window](https://support.microsoft.com/en-us/help/2677070/an-automatic-updater-of-untrusted-certificates-is-available-for-window)
|
||||||
|
|
||||||
|
[https://askubuntu.com/questions/191226/dnsmasq-failed-to-create-listening-socket-for-port-53-address-already-in-use](https://askubuntu.com/questions/191226/dnsmasq-failed-to-create-listening-socket-for-port-53-address-already-in-use)
|
||||||
|
|
||||||
|
[https://gallery.technet.microsoft.com/scriptcenter/Change-the-Desktop-b5b2141c](https://gallery.technet.microsoft.com/scriptcenter/Change-the-Desktop-b5b2141c)
|
||||||
|
|
||||||
|
[https://gist.github.com/trietptm/b84ccad9db01f459ac7e](https://gist.github.com/trietptm/b84ccad9db01f459ac7e)
|
||||||
|
|
||||||
|
https://www.amazon.com/Building-Virtual-Machine-Labs-Hands/dp/1546932631
|
||||||
|
|
||||||
86
_posts/2023-06-05-SANS SEC 504 - Resources.md
Normal file
86
_posts/2023-06-05-SANS SEC 504 - Resources.md
Normal file
@ -0,0 +1,86 @@
|
|||||||
|
---
|
||||||
|
title: SANS SEC 504 - Resources
|
||||||
|
date: 06-05-2023
|
||||||
|
catagories: [cybersecurity, malware, red team tools]
|
||||||
|
tags: [SANS, SEC504, GCIH, cybersecurity]
|
||||||
|
---
|
||||||
|
|
||||||
|
#### Malware stuff
|
||||||
|
https://digitalcommons.lsu.edu/cgi/viewcontent.cgi?article=6527&context=gradschool_theses
|
||||||
|
|
||||||
|
https://github.com/volatilityfoundation/volatility/wiki/Mac
|
||||||
|
|
||||||
|
#### Volatility
|
||||||
|
A few volatility resources:
|
||||||
|
|
||||||
|
- [https://github.com/volatilityfoundation/volatility/wiki](https://github.com/volatilityfoundation/volatility/wiki)
|
||||||
|
- [https://forwarddefense.com/media/attachments/2021/05/15/memory-analysis-with-volatlity-analyst-reference-20200131.pdf](https://forwarddefense.com/media/attachments/2021/05/15/memory-analysis-with-volatlity-analyst-reference-20200131.pdf)
|
||||||
|
- [https://andreafortuna.org/2019/04/03/how-to-analyze-a-vmware-memory-image-with-volatility/](https://andreafortuna.org/2019/04/03/how-to-analyze-a-vmware-memory-image-with-volatility/)
|
||||||
|
|
||||||
|
(edited)
|
||||||
|
|
||||||
|
Andrea Fortuna
|
||||||
|
|
||||||
|
[How to analyze a VMware memory image with Volatility](https://andreafortuna.org/2019/04/03/how-to-analyze-a-vmware-memory-image-with-volatility/)
|
||||||
|
|
||||||
|
A very brief post, just a reminder about a very useful volatility feature. The process on a VMware machine is more simple than VirtualBox, just 4 simple steps: Suspend the virtual machine Navigate to the virtual machine's directory and identify the `*.vmem` file Copy the vmem image to you analysis workstation Finally use the following Volatility command to convert the memory image to a dump ready for analysis: `$ volatility -f memory_image.vmem -O raw_image --profile=Win8SP0x86 raw2dmp` Now the memory dump can be analyzed with the usual methods.
|
||||||
|
|
||||||
|
#### Berkley Packet Filters
|
||||||
|
|
||||||
|
https://www.ibm.com/docs/en/qsip/7.4?topic=queries-berkeley-packet-filters
|
||||||
|
|
||||||
|
https://github.com/sbabicz/tcpdump-bpf-cheatsheet
|
||||||
|
|
||||||
|
#### Grouped Managed Service Accounts Overview
|
||||||
|
|
||||||
|
https://learn.microsoft.com/en-us/windows-server/security/group-managed-service-accounts/group-managed-service-accounts-overview
|
||||||
|
|
||||||
|
#### Placeholder
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
#### How much does a DDoS cost?
|
||||||
|
|
||||||
|
As per the Dark Web Price Index 2022, a 24-hour DDoS attack with 20-50k requests per second can cost the attacker as little as $200 USD. This low cost of entry means that even small-time attackers can launch devastating DDoS attacks that can cripple businesses and cause significant financial losses. Mar 10, 2023
|
||||||
|
|
||||||
|
https://sans-live-training.slack.com/archives/C059WKMLLDB/p1686064393422589
|
||||||
|
|
||||||
|
[https://www.linkedin.com/pulse/true-cost-ddos-attack-protect-your-business-proactive-ali-el-tom/](https://www.linkedin.com/pulse/true-cost-ddos-attack-protect-your-business-proactive-ali-el-tom/)
|
||||||
|
|
||||||
|
linkedin.com
|
||||||
|
|
||||||
|
[The True Cost of a DDoS Attack: Protect Your Business with Proactive Measures](https://www.linkedin.com/pulse/true-cost-ddos-attack-protect-your-business-proactive-ali-el-tom/)
|
||||||
|
|
||||||
|
Launching a DDoS attack can be relatively inexpensive for the attacker. As per the Dark Web Price Index 2022, a 24-hour DDoS attack with 20-50k requests per second can cost the attacker as little as $200 USD.
|
||||||
|
|
||||||
|
#### MITRE ATT&CK
|
||||||
|
|
||||||
|
- CWE (Common Weakness Enumeration)
|
||||||
|
|
||||||
|
#### Background Reports
|
||||||
|
|
||||||
|
Our disclaimer on Background Reports:
|
||||||
|
DISCLOSURE/DISCLAIMERThe information in this report is based on public, non-public, private, and proprietary databases. Search results may not be complete or accurate. Not all states or counties report or make available all records in electronic format. Online databases could contain incomplete information, duplication, inaccuracies, or false matches based on common names.Certified copies can be obtained and in-person/on-site verification of research results can be performed but will require additional investigative time and expenses that must be authorized.The general format of this report and parts of this report are produced from xxxxxxx. Information obtained from xxxxxx, and other public and private databases, does not constitute a "consumer report" as that term is defined in the federal Fair Credit Reporting Act, 15 USC 1681 et seq.(FCRA).As data from xxxxxxxx and other data sources is not specifically segregated, this report may not be used in whole or in part as a factor in determining eligibility for credit, insurance, employment, or another permissible purpose under the FCRA.Any questions, comments or concerns related to the information contained in this report should be directed to:
|
||||||
|
Keith Olive Enterprises, LLC
|
||||||
|
PO Box 26
|
||||||
|
Mountain Home, Texas 78058
|
||||||
|
Texas Private Security Bureau License #A19867
|
||||||
|
|
||||||
|
```ad-important
|
||||||
|
OSINT on employees without permission will bite you big time if they ever bring up a LABOR board issue or lawsuit
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
|
#### Cheat sheets
|
||||||
|
|
||||||
|
https://packetlife.net/library/cheat-sheets/
|
||||||
|
|
||||||
|
##### Amazon Books
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
#### What 2 Log
|
||||||
|
|
||||||
|
https://what2log.com/
|
||||||
|
|
||||||
34
_posts/2023-06-07-Diablo 4 Helltide Events.md
Normal file
34
_posts/2023-06-07-Diablo 4 Helltide Events.md
Normal file
@ -0,0 +1,34 @@
|
|||||||
|
---
|
||||||
|
title: Diablo 4 HellTide Events
|
||||||
|
date: 06-07-2023
|
||||||
|
catagories: [Diablo 4, Gaming, ARPG]
|
||||||
|
tags: [diablo, diablo 4, docs]
|
||||||
|
---
|
||||||
|
|
||||||
|
## Diablo 4 HellTide Events
|
||||||
|
|
||||||
|
When you guys hit World Tier 3, do helltide events everytime you can, they're stupidly important because they're the only source of Forgotten Souls and you need a lot of them to keep upgrading/rerolling gear. I skimped out on them and wish I didn't now.
|
||||||
|
|
||||||
|
- There is a timer for the Helltide Event here: [https://d4events.live/](https://d4events.live/) - The event is up for one hour and then down for 1 hour 15 minutes until the next one.
|
||||||
|
|
||||||
|
- The general gist of Helltides is roam around, kill packs for cinders, do world events (more mobs more cinders) and open Helltide Chests
|
||||||
|
|
||||||
|
- When Hellfire meteors rain down, it means a Helltide Elite is spawning nearby and they drop a fair amount as well
|
||||||
|
|
||||||
|
- Forgotten Souls can also come from normal helltide chests, and Screaming Hell Veins
|
||||||
|
|
||||||
|
- This site shows the POSSIBLE spawn locations of the mystery chests - [https://d4armory.io/map/](https://d4armory.io/map/) These require 175 cinders to open and can give a bunch of legs and crafting mats (ex - [https://i.imgur.com/oGb2dvc.jpeg](https://i.imgur.com/oGb2dvc.jpeg)) The chests DO NOT SHOW on the map (until you are very close, and when you go away, the icon will disappear) so if you find it, pin NEAR it (not on the chest icon otherwise it will disappear) and come back if you can't open it. PRIO THESE CHESTS OVER ALL
|
||||||
|
|
||||||
|
- Mystery Chests will move at the top of the hour (When the IRL clock hits xx:00) meaning you can get multiple chests. Multiple can spawn at once with one per large region zone.
|
||||||
|
|
||||||
|
- The official D4 server has a channel for people to post where the chests are located during events - [https://discord.com/invite/diablo4#discord](https://discord.com/invite/diablo4#discord)
|
||||||
|
|
||||||
|
|
||||||
|
Edit 1: - [/u/Prowner1](https://www.reddit.com/u/Prowner1/) has made a site and added a Helltide Tracker to it which allows inputs from users to show where the chests are on the current event - [https://diablo4.life/trackers/helltide](https://diablo4.life/trackers/helltide)
|
||||||
|
|
||||||
|
Edit 2: Changed the Mystery Chest movement time, it appears to be top of the hour. (The chests moving is honestly the most confusing part)
|
||||||
|
|
||||||
|
I fucking hate this event and hope they allow you to get Forgotten Souls somewhere else in the game.
|
||||||
|
|
||||||
|
https://d4events.live/
|
||||||
|
|
||||||
157
_posts/2023-06-12-Diablo 4 - Shadow Rogue Build.md
Normal file
157
_posts/2023-06-12-Diablo 4 - Shadow Rogue Build.md
Normal file
@ -0,0 +1,157 @@
|
|||||||
|
---
|
||||||
|
title: Diablo 4 - Shadow Rouge Build
|
||||||
|
date: 06-12-2023
|
||||||
|
catagories: [Diablo 4, Gaming, ARPG]
|
||||||
|
tags: [diablo, diablo 4, docs]
|
||||||
|
---
|
||||||
|
|
||||||
|
```ad-important
|
||||||
|
This is a beginner friendly build.
|
||||||
|
```
|
||||||
|
|
||||||
|
#### Skill Tree
|
||||||
|
|
||||||
|
https://d4builds.gg/builds/a175bae2-7adf-4155-a347-509d4efbb86c/
|
||||||
|
|
||||||
|
#### Skill Tree Guide
|
||||||
|
|
||||||
|
https://fextralife.com/diablo-4-shadow-rogue-build-twisting-blades/
|
||||||
|
|
||||||
|
Youtube Video: https://www.youtube.com/watch?v=IRgXnTgvZiE
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
# Diablo 4 Shadow Rogue Build – Twisting Blades
|
||||||
|
|
||||||
|
 May 31, 2023,  [Ryuga](https://fextralife.com/author/ryuga/),  0
|
||||||
|
|
||||||
|
**Diablo 4 Shadow Rogue Build Guide**: In this Diablo 4 **[Rogue Class](https://diablo4.wiki.fextralife.com/Rogue)** Build, I’ll show you how to play a Shadow Imbuement – Twisting Blades Rogue, which is a melee Diablo 4 Build for the Rogue that impales enemies with the **[Twisting Blades Skill](https://diablo4.wiki.fextralife.com/Twisting+Blades)** to inflict massive AoE damage. If you’ve been looking for a good **Diablo 4 Twisting Blades Rogue Build** that allows you to quickly explode all your enemies, then this guide is for you!
|
||||||
|
|
||||||
|
- The Level 50 version of this build evolves into the [Shadowblade Build](https://fextralife.com/diablo-4-twisting-blades-rogue-build-shadowblade/).
|
||||||
|
|
||||||
|
Also, be sure to check out our [Diablo 4 Wiki](https://diablo4.wiki.fextralife.com/) and [Interactive Map](https://diablo4.wiki.fextralife.com/Interactive+Map) if you need help finding specific [Altars of Lilith](https://diablo4.wiki.fextralife.com/Altar+of+Lilith), [Dungeons](https://diablo4.wiki.fextralife.com/Dungeons), or [Side Quests](https://diablo4.wiki.fextralife.com/Side+Quests)!
|
||||||
|
|
||||||
|
## Diablo 4 Shadow Rogue Build Guide – Twisting Blades
|
||||||
|
|
||||||
|
The way this Diablo 4 Shadow Rogue Build works is by using [**Shadow Imbuement**](https://diablo4.wiki.fextralife.com/Shadow+Imbuement) in combination with **[Twisting Blades](https://diablo4.wiki.fextralife.com/Twisting+Blades)** to generate a chain reaction of explosions that decimates big groups of enemies. To achieve this, you’ll start the fight by casting the **[**Shadow Imbuement**](https://diablo4.wiki.fextralife.com/Shadow+Imbuement)** buff, then you’ll head straight into a pack of enemies and perform two attacks with **[Twisting Blades](https://diablo4.wiki.fextralife.com/Twisting+Blades)** (you can hit the same enemy or two different enemies).
|
||||||
|
|
||||||
|
Now, you’ll use [**Dash**](https://diablo4.wiki.fextralife.com/Dash) to pass through the group and get on the exact opposite side and start attacking using your [**Invigorating Strike**](https://diablo4.wiki.fextralife.com/Invigorating+Strike) (this will build up combo points and increase your Energy regeneration). At this point, the first two attacks you made with **[Twisting Blades](https://diablo4.wiki.fextralife.com/Twisting+Blades)** will return to you passing through the pack of enemies. This will deal damage to all of them and apply the [**Shadow Imbuement**](https://diablo4.wiki.fextralife.com/Shadow+Imbuement) debuff, which will generate a chain-reaction of explosions. Also, because of the **[Advanced Twisting Blades Upgrade](https://diablo4.wiki.fextralife.com/Advanced+Twisting+Blades)**, both your [**Shadow Imbuement**](https://diablo4.wiki.fextralife.com/Shadow+Imbuement) and [**Dash**](https://diablo4.wiki.fextralife.com/Dash) cooldown’s will be reduced, and thanks to **[Consuming Shadows](https://diablo4.wiki.fextralife.com/Consuming+Shadows)** you’ll get back the energy you spent, allowing you to restart the sequence.
|
||||||
|
|
||||||
|
Once you are on the opposite side, you can use [**Invigorating Strike**](https://diablo4.wiki.fextralife.com/Invigorating+Strike) to increase Energy Regeneration and to build up 3 combo points, which will greatly increase the damage of your Twisting Blades, so even if you are not able to cast Shadow Imbuement right away, the daggers will deal even more damage on the second pass, allowing you to finish off any remaining enemies.
|
||||||
|
|
||||||
|
The aspect that will help the most here is the [**Bladedancer’s Aspect**](https://diablo4.wiki.fextralife.com/Bladedancer's+Aspect), making it so that the returning blades orbit around you in the end to deal extra damage, which is very useful to finish off the enemies or to deal with Elites. This new Orbit Damage is further amplified based on the enemies pierced by the boomerang effect. You can acquire the Codex of Power of this aspect by completing the **Jalal’s Vigil Dungeon**, located at **Scosglen**.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
I recommend using **[Combo Points Specialization](https://diablo4.wiki.fextralife.com/Specialization)** to fight regular enemies, as it’ll increase the damage of your Twisting Blades, and also give you a Speed Buff, but you should swap to [**Inner Sight Specialization**](https://diablo4.wiki.fextralife.com/Inner+Sight) when fighting Bosses. Doing so will allow you to spam the Twisting Blades skill when Inner Sight is active, dealing a ton amount of damage and generating a massive amount of orbiting blades that quickly ticks the boss health’s down. Remember that you’ll also invest points into the [**Shadow Clone Ultimate**](https://diablo4.wiki.fextralife.com/Shadow+Clone) to be able to summon your shadow who will mimic this action, further increasing the burst damage.
|
||||||
|
|
||||||
|
### Diablo 4 Twisting Blades Rogue Build Guide – Skill Distribution
|
||||||
|
|
||||||
|
Each Diablo 4 Shadow Rogue Build is made up of the 6 Active Skills they have equipped and changing these [**Skills**](https://diablo4.wiki.fextralife.com/Barbarian+Skills) can drastically alter the way the Rogue Class in Diablo IV plays. In this section, we’ll take a look at what Skills you should slot for the Twisting Blades Rogue Diablo 4 Build. Your Skill distribution should look something like this:
|
||||||
|
|
||||||
|
| | |
|
||||||
|
|---|---|
|
||||||
|
|LEVEL 25 SHADOW ROGUE SKILLS| |
|
||||||
|
|**Skill**|**Points Spent**|
|
||||||
|
|Invigorating Strike|1|
|
||||||
|
|Enhanced Invigorating Strike|1|
|
||||||
|
|Twisting Blades|5|
|
||||||
|
|Enhanced Twisting Blades|1|
|
||||||
|
|Advanced Twisting Blades|1|
|
||||||
|
|Shadow Step|1|
|
||||||
|
|Dash|1|
|
||||||
|
|Exploit|3|
|
||||||
|
|Malice|2|
|
||||||
|
|Shadow Crash|1|
|
||||||
|
|Consuming Shadows|2|
|
||||||
|
|Shadow Imbuement|3|
|
||||||
|
|Enhanced Shadow Imbuement|1|
|
||||||
|
|Blended Shadow Imbuement|1|
|
||||||
|
|Shadow Clone|1|
|
||||||
|
|Prime Shadow Clone|1|
|
||||||
|
|
||||||
|
The above list gives you the general order to invest in Skills, but keep in mind that you should prioritize picking up new Active Skills over investing in passives, so pick up passives later if you can get new Active Skills when you level up.
|
||||||
|
|
||||||
|
### Diablo 4 Shadow Rogue Build – How to Handle Packs of Enemies
|
||||||
|
|
||||||
|
So there are several different strategies to employ with this Diablo IV Build for the Twisting Blades Rogue, and these change depending on whether you’re facing a large group of enemies or a Boss. Let’s start with a group of enemies first, and we’ll cover how to handle Bosses in the next section.
|
||||||
|
|
||||||
|
#### [Shadow Imbuement](https://diablo4.wiki.fextralife.com/Shadow+Imbuement)
|
||||||
|
|
||||||
|
As with the rest of the Diablo IV Builds for the Rogue Class, you’ll be able to choose the type of damage you deal. For this Twisting Blades Rogue, we’re going to pick Shadow Imbuement to convert your damage into Shadow Damage and infect multiple targets. To infect a target you must strike it with a Shadow Imbued skill, we’ll achieve this by first sticking a shadow imbued Twisting Blade into an enemy, and then making it pass through the other enemies when it returns to us.
|
||||||
|
|
||||||
|
When an infected target is killed, it will explode, dealing massive damage to all surrounding enemies, generating a chain reaction that decimate big groups. In addition to this, our [**Blended Shadow Imbuement**](https://diablo4.wiki.fextralife.com/Blended+Shadow+Imbuement) upgrade will make them [**Vulnerable**](https://diablo4.wiki.fextralife.com/Vulnerable), so after the first explosion everything else will die even faster.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
#### [Twisting Blades](https://diablo4.wiki.fextralife.com/Twisting+Blades)
|
||||||
|
|
||||||
|
Twisting Blades is key to this build, because of its boomerang effect. Enemies often attack you in a line pattern, so you’ll want to strike the first one or two enemies and then reposition behind them. After 1.5 second, the blades will return to you, passing through the pack and applying the Shadow Debuff and dealing massive individual damage thanks to the [**Enhanced Twisting Blades**](https://diablo4.wiki.fextralife.com/Enhanced+Twisting+Blades), which will allow you to kill some enemies and trigger the chain explosion. You’ll want to prioritize positioning to maximize the amount of enemies you hit when the blade returns, as each enemy hit will reduce all of your active cooldowns by 0.25 second for each enemy hit thanks to the **[Advanced Twisting Blades Upgrade](https://diablo4.wiki.fextralife.com/Advanced+Twisting+Blades)**.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Since this is the main skill of your Twisting Blades Rogue Diablo 4 Build, you’ll want to max it out and then get [**Enhanced Twisting Blades**](https://diablo4.wiki.fextralife.com/Enhanced+Twisting+Blades) together with [**Advanced Twisting Blades**](https://diablo4.wiki.fextralife.com/Advanced+Twisting+Blades) as soon as possible.
|
||||||
|
|
||||||
|
#### **[Invigorating Strike](https://diablo4.wiki.fextralife.com/Invigorating+Strike)**
|
||||||
|
|
||||||
|
Invigorating Strike is a Basic Skill for this D4 Build that allows you to deal a small amount of damage, but also increases your Energy Regeneration and has a 50% Lucky Hit Chance, which is very nice to have. Since you’ll be using the Combo Points Specialization against regular enemies, so each attack you perform will give you 1 combo point. Ideally, you’ll want to use your starter combination of Shadow Imbue and Twisting Blades to then dash behind the enemy group and start attack perform three attacks with Invigorating Strike. This will give you 20% Energy Regeneration, or 50% if the enemy is either Injured or Crowed Controlled.
|
||||||
|
|
||||||
|
Also, if you happen to have a very good Lucky Hit Chance skill on your equipment, you can also go for [**Primary Invigorating Strike**](https://diablo4.wiki.fextralife.com/Primary+Invigorating+Strike) to further increase the proc chance, but it’s not mandatory for this build.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
#### [Dash](https://diablo4.wiki.fextralife.com/Dash)
|
||||||
|
|
||||||
|
We’ll be using dash to quickly navigate through the open map, and also to quickly reposition behind the pack of enemies at the beginning of the fight. Note that Dash has 2 charges, so make sure you always have at least 1 charge available when engaging a group of enemies, or you won’t be able to reposition to activate your combo. You won’t need enhancements for this Skill since it’ll be primarily used for movement
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
#### [Shadow Step](https://diablo4.wiki.fextralife.com/Shadow+Step)
|
||||||
|
|
||||||
|
Shadow Step is an essential survivability tool of this Twisting Blades Rogue D4 Build, since your Health and defenses aren’t all that great. When activated, you’ll automatically gain [**Unstoppable**](https://diablo4.wiki.fextralife.com/Unstoppable), which removes and prevents all control impairing effects. This allows you to break out of critical situations, such as getting froze or stunned.
|
||||||
|
|
||||||
|
In addition, the skill will perform a lucky hit with a 100% chance on the target enemy, and provide you 50% movement speed for 2 seconds, giving you the chance to drink a potion and reposition to a safe place.
|
||||||
|
|
||||||
|
You can also use Shadow Step to quickly reposition behind an enemy to take full advantage of the Twisting Blades Boomerang effect, but you should only do this if you are certain you are not going to get affected by a control impairing effect.
|
||||||
|
|
||||||
|
You won’t need the enhancement or upgrade, since we’ll be mainly using it as an emergency survival tool.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Passives
|
||||||
|
|
||||||
|
For passives of this Diablo 4 Twisting Blades Rogue Build, you’ll be taking [**Shadow Crash**](https://diablo4.wiki.fextralife.com/Shadow+Crash) to gain access to [**Consuming Shadows**](https://diablo4.wiki.fextralife.com/Consuming+Shadows). Shadow Crash raises the chances of Stunning enemies when they receive Shadow Damage which works great for elites, but the Skill you’ll want more is Consuming Shadows, hence the 2-point investment. This lets you generate all the Energy you spent in the combo, provided that you kill them with the Shadow Imbuement.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
The other passive that you’ll want to take are **[Exploit](https://diablo4.wiki.fextralife.com/Exploit)** and **[Malice](https://diablo4.wiki.fextralife.com/Malice)**.
|
||||||
|
|
||||||
|
Exploit increases the damage you deal to both **[Healthy](https://diablo4.wiki.fextralife.com/Healthy)** and **[Injured](https://diablo4.wiki.fextralife.com/Injured)** enemies. Since you’ll first deal damage to enemies with full health, and then deal with the remaining ones, this passive is active practically all the time.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Malice increases the damage you deal to Vulnerable enemies, which synergizes perfectly with the [**Blended Shadow Imbuement**](https://diablo4.wiki.fextralife.com/Blended+Shadow+Imbuement) that makes enemies vulnerable after the explosions.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
### Rogue Build for Boss Fights
|
||||||
|
|
||||||
|
Boss fights are handled a bit differently with this Diablo 4 Twisting Blades Rogue Build. First, you’ll want to swap your specialization from Combo Points for Inner Sight. Inner Sight allows you’ll fill up a gauge when attacking the marked enemy, Bosses are often alone, so you’ll be filling the gauge by attacking it. Once the gauge is full, you’ll gain unlimited energy for 4 seconds. At that moment, you’ll want to spawn your **[Shadow Clone](https://diablo4.wiki.fextralife.com/Shadow+Clone)**, cast Shadow Imbuement and then start spamming Twisting Blade as much as you can. As the blades return, they’ll start circling around you, stacking tons of damage into the boss.
|
||||||
|
|
||||||
|
#### [Shadow Clone](https://diablo4.wiki.fextralife.com/Shadow+Clone)
|
||||||
|
|
||||||
|
Shadow Clone is an ultimate ability that will provide you with aid by conjuring your own shadow to copy the actions you’re pulling off. Although the damage won’t be as potent, it’s still a great way of increasing our single target damage. You can also invest in [**Prime Shadow Clone**](https://diablo4.wiki.fextralife.com/Prime+Shadow+Clone) to have another option to make you Unstoppable every time Shadow Clone is activated.
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Make sure to use your dash to avoid boss attacks or to quickly disengage from combat to drink a potion and recover your health. Same as with regular enemies, you’ll want to save Shadow Step for when you are affected by a movement impairing effect. Finally, remember that you can also use your **[Shadow Clone Ultimate](https://diablo4.wiki.fextralife.com/Shadow+Clone)** to the same end, thanks to **[Prime Shadow Clone](https://diablo4.wiki.fextralife.com/Prime+Shadow+Clone)** which provides you [**Unstoppable**](https://diablo4.wiki.fextralife.com/Unstoppable) for 5 seconds.
|
||||||
|
|
||||||
|
### Final Tips
|
||||||
|
|
||||||
|
For this Diablo 4 Twisting Blades Rogue Build, you should be on the lookout for gear that gives bonuses to [**Dexterity**](https://diablo4.wiki.fextralife.com/Dexterity), [**Intelligence**](https://diablo4.wiki.fextralife.com/Intelligence), Maximum Energy, +Rank to relevant skills, Critical Strike Chance, [**Critical Strike Damage Bonus**](https://diablo4.wiki.fextralife.com/Critical+Strike+Damage+Bonus), [**Damage to Close Enemies**](https://diablo4.wiki.fextralife.com/Damage+to+Close+Enemies), Imbuement Skill Damage, [**Core Skill Damage**](https://diablo4.wiki.fextralife.com/Core+Skill+Damage), [**Energy Cost Reduction**](https://diablo4.wiki.fextralife.com/Energy+Cost+Reduction), and [**Cooldown Reduction**](https://diablo4.wiki.fextralife.com/Cooldown+Reduction). [**Damage Reduction**](https://diablo4.wiki.fextralife.com/Damage+Reduction) is also good to pick up where you’re often susceptible to taking in lots of damage in the melee range. It’s a pretty OP D4 Rogue Build due to the massive burst damage you deal.
|
||||||
|
|
||||||
|
You can run around the map and stack a couple of enemy groups and engage all of them at the same time for maximum efficiency. Make sure to prioritize positioning over attacking individual targets.
|
||||||
|
|
||||||
|
When it comes to Legendary Aspects, you’ll also want to get the **[Aspect of Lethal Dusk](https://diablo4.wiki.fextralife.com/Aspect+of+Lethal+Dusk)** and [**Ravenous Aspect**](https://diablo4.wiki.fextralife.com/Ravenous+Aspect) for this Diablo 4 Build. Lethal Dusk grants Stealth when evading through a Shadow Imbuement infect enemy, which is great if you need to recover or reposition, and on top of that, it will give you a buff that grants you 1~5% of maximum life recovered on kill for 4 seconds. Meanwhile, Ravenous Aspect rewards you with increased Energy regeneration when a Vulnerable enemy is slain, which works hand-in-hand with Blended Shadow Imbuement.
|
||||||
|
|
||||||
|

|
||||||
@ -0,0 +1,67 @@
|
|||||||
|
---
|
||||||
|
title: M1 Mac - How to Switch the Terminal between x86_64 and arm64
|
||||||
|
date: 06-12-2023
|
||||||
|
catagories: [macbook pro, mac m1, macOS, terminal]
|
||||||
|
tags: [terminal, macOS, M1]
|
||||||
|
---
|
||||||
|
|
||||||
|
## How to Switch the Terminal between x86_64 and arm64
|
||||||
|
https://vineethbharadwaj.medium.com/m1-mac-switching-terminal-between-x86-64-and-arm64-e45f324184d9
|
||||||
|
|
||||||
|
Here is a simple writeup on how I switch between x86_64 and arm64 in the Terminal app on my MacBook Pro with Apple Silicon.
|
||||||
|
|
||||||
|
So you have the new Mac with Apple Silicon. However, a lot of your projects are compiled in x86 and/or you are still building apps for x86, or whatever it is, you still want to compile the x86_64 code on your new Mac in the Terminal. You know it is possible with the Rosetta 2 (personally love it!). But how do you do it efficiently?
|
||||||
|
|
||||||
|
While there are many ways of doing it, the following is the best one I have found to easily switch between the two architectures using just a simple Terminal command as below (actually hiding the command under an alias)..
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
switching efficiently between x86_64 and arm64 using created alias
|
||||||
|
|
||||||
|
So let’s look at what’s behind it, and how you too can easily set it up!
|
||||||
|
|
||||||
|
The main command which does the magic is the one below:
|
||||||
|
|
||||||
|
$env /usr/bin/arch -<architecture> /bin/zsh --login
|
||||||
|
|
||||||
|
… just replace the _<architecture>_ with your preferred one..
|
||||||
|
|
||||||
|
**For example:**
|
||||||
|
|
||||||
|
- To see your current architecture, type:
|
||||||
|
|
||||||
|
$arch
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
see current architecture the Terminal is using
|
||||||
|
|
||||||
|
As we see in the image above, I am currently using arm64, hence any code I compile will be for this architecture.
|
||||||
|
|
||||||
|
- To switch to x86_64, type:
|
||||||
|
|
||||||
|
==$env /usr/bin/arch -x86_64 /bin/zsh —-login==
|
||||||
|
|
||||||
|
Now if you type the arch command again, you will see that the target architecture has been changed. Now you can go ahead and compile your code using Rosetta 2 for the x86_64 architecture.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
# Creating alias in .zshrc:
|
||||||
|
|
||||||
|
I don’t want to remember the whole command and type it all the time (obviously it’s not efficient). The simplest solution is to create an alias to it in the _.zshrc_
|
||||||
|
|
||||||
|
Just _cd_ into your home directory and open the .zshrc file.. If you don’t have one, you can easily create it using the _touch_ command. (If you don’t know about it, there are already plenty of tutorials/write-ups online)..
|
||||||
|
|
||||||
|
Here’s how my _.zshrc_ file looks like.. I have named my aliases arm and intel for the arm and x86_64 architectures respectively. You can name your aliases whatever you want. Just remember to relaunch the Terminal after updating and saving the _.zshrc_ file.
|
||||||
|
|
||||||
|
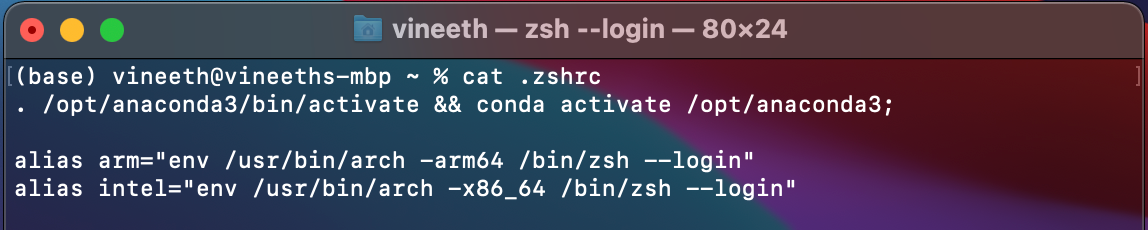
|
||||||
|
|
||||||
|
adding alias to .zshrc
|
||||||
|
|
||||||
|
Ignoring the first line, you can see the two alias I have created for arm and intel. To switch, I just need to type the alias and that’s it!
|
||||||
|
|
||||||
|
# **Bonus:**
|
||||||
|
|
||||||
|
If you only want to use the Terminal app with Rosetta 2 for the x86_64 architecture, you can simple right click on the Terminal app in the _Applications>Utilities_, go the _‘Get Info’ and tick on “Open using Rosetta”_
|
||||||
|
|
||||||
|
|
||||||
29
_posts/2023-06-12-Mac M1 Run Diablo 4.md
Normal file
29
_posts/2023-06-12-Mac M1 Run Diablo 4.md
Normal file
@ -0,0 +1,29 @@
|
|||||||
|
---
|
||||||
|
title: Mac M1 Run Diablo 4 - Links
|
||||||
|
date: 06-12-2023
|
||||||
|
catagories: [macOS, macbook pro, M1]
|
||||||
|
tags: [terminal, diablo 4, apple silicon, M1]
|
||||||
|
---
|
||||||
|
|
||||||
|
Resources:
|
||||||
|
|
||||||
|
https://www.outcoldman.com/en/archive/2023/06/07/playing-diablo-4-on-macos
|
||||||
|
|
||||||
|
https://vineethbharadwaj.medium.com/m1-mac-switching-terminal-between-x86-64-and-arm64-e45f324184d9
|
||||||
|
|
||||||
|
https://stackoverflow.com/questions/17980759/xcode-select-active-developer-directory-error
|
||||||
|
|
||||||
|
https://developer.apple.com/download/all/?q=Xcode
|
||||||
|
|
||||||
|
https://wiki.winehq.org/Wine_User's_Guide#Using_Wine
|
||||||
|
|
||||||
|
https://forum.xojo.com/t/problems-with-ditto/32265
|
||||||
|
|
||||||
|
https://www.applegamingwiki.com/wiki/Game_Porting_Toolkit#Steam_login_black_screen
|
||||||
|
|
||||||
|
http://stream-recorder.com/forum/restart-wine-if-you-cant-close-process-t4997.html?s=6d49a94d7d9a590a42d133accc36ae88&
|
||||||
|
|
||||||
|
https://www.youtube.com/watch?v=5Nd-nR3-6lU&t=79s
|
||||||
|
|
||||||
|
https://www.youtube.com/watch?v=5Nd-nR3-6lU
|
||||||
|
|
||||||
67
_posts/2023-06-16-Flaws.cloud - AWS.md
Normal file
67
_posts/2023-06-16-Flaws.cloud - AWS.md
Normal file
@ -0,0 +1,67 @@
|
|||||||
|
---
|
||||||
|
title: Flaws.cloud walkthrough
|
||||||
|
date: 06-16-2023
|
||||||
|
catagories: [cybersecurity, Red Teaming, terminal]
|
||||||
|
tags: [terminal, cloud, cybersecurity]
|
||||||
|
---
|
||||||
|
## Flaws.cloud walkthrough
|
||||||
|
|
||||||
|
**DayCyberWox Walkthrough:** https://www.youtube.com/watch?v=fEjAryrzLSQ
|
||||||
|
**Write up:** https://daycyberwox.com/exploiting-aws-1-a-beginners-guide-flawscloud#heading-level1
|
||||||
|
|
||||||
|
```
|
||||||
|
Through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS). There are no SQL injection, XSS, buffer overflows, or many of the other vulnerabilities you might have seen before. As much as possible, these are AWS specific issues.
|
||||||
|
|
||||||
|
A series of hints are provided that will teach you how to discover the info you'll need. If you don't want to actually run any commands, you can just keep following the hints which will give you the solution to the next level. At the start of each level you'll learn how to avoid the problem the previous level exhibited.
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
**Scope**: Everything is run out of a single AWS account, and all challenges are sub-domains of [flaws.cloud](http://flaws.cloud/).
|
||||||
|
|
||||||
|
**Contact**
|
||||||
|
This was built by Scott Piper ([@0xdabbad00](https://twitter.com/0xdabbad00), [summitroute.com](https://summitroute.com/))
|
||||||
|
|
||||||
|
Feedback is welcome! For security issues, fan mail, hate mail, or whatever else, contact scott@summitroute.com
|
||||||
|
If you manage to find a flaw that breaks the game for others or some other undesirable issue, please let me know.
|
||||||
|
|
||||||
|
**Greetz**
|
||||||
|
Thank you for advice and ideas from Andres Riancho ([@w3af](https://twitter.com/w3af)), [@CornflakeSavage](https://twitter.com/CornflakeSavage), Ken Johnson ([@cktricky](https://twitter.com/cktricky)), and Nicolas Gregoire ([@Agarri_FR](https://twitter.com/Agarri_FR))
|
||||||
|
|
||||||
|
Now for the challenge!
|
||||||
|
|
||||||
|
# Level 1
|
||||||
|
|
||||||
|
This level is *buckets* of fun. See if you can find the first sub-domain.
|
||||||
|
|
||||||
|
Need a hint? Visit [Hint 1](http://flaws.cloud/hint1.html)
|
||||||
|
|
||||||
|
First we begin with `nslookup` and point it to the domain `flaws.cloud`
|
||||||
|
### Syntax
|
||||||
|
``` shell
|
||||||
|
nslookup flaws.cloud
|
||||||
|
```
|
||||||
|
|
||||||
|
### Result
|
||||||
|
|
||||||
|
``` shell
|
||||||
|
Server: 172.31.144.1
|
||||||
|
Address: 172.31.144.1#53
|
||||||
|
|
||||||
|
Non-authoritative answer:
|
||||||
|
Name: flaws.cloud
|
||||||
|
Address: 52.92.196.83
|
||||||
|
Name: flaws.cloud
|
||||||
|
Address: 52.92.227.67
|
||||||
|
Name: flaws.cloud
|
||||||
|
Address: 52.92.243.131
|
||||||
|
Name: flaws.cloud
|
||||||
|
Address: 52.92.250.91
|
||||||
|
Name: flaws.cloud
|
||||||
|
Address: 52.218.132.58
|
||||||
|
Name: flaws.cloud
|
||||||
|
Address: 52.218.218.82
|
||||||
|
Name: flaws.cloud
|
||||||
|
Address: 52.218.237.138
|
||||||
|
Name: flaws.cloud
|
||||||
|
Address: 52.92.163.83
|
||||||
|
|
||||||
163
_posts/2023-08-22-Adding Admonitions to Jekyll.md
Normal file
163
_posts/2023-08-22-Adding Admonitions to Jekyll.md
Normal file
@ -0,0 +1,163 @@
|
|||||||
|
---
|
||||||
|
title: Adding Admonitions to Jekyll
|
||||||
|
date: 08-22-2023
|
||||||
|
catagories: [minima, Themes, Jekyll, GitHub Pages]
|
||||||
|
tags: [minima, jekyll, github pages, themes, admonitions, docs]
|
||||||
|
---
|
||||||
|
|
||||||
|
## What Is An Admonition?
|
||||||
|
A distinct area of text to emphasize significant attention that is not a part of the main body. The purpose of admonition is drawing attention towards what you want a reader to remember without significantly interrupting the document flow. Admonitions are more commonly referred to as a callout or call-out.
|
||||||
|
|
||||||
|
{% include admonition.html type="info" title="Info" body="Example: This is information intended to draw attention." %}
|
||||||
|
|
||||||
|
## The Code
|
||||||
|
My approach was to create a Jekyll include file for the HTML with Liquid template language and Cascading Style Sheets (CSS) with syntactically awesome style sheets (SASS). This will allow for ease of adding admonitions without having to type out all the code manually each time. The styles are not completely identical to Material as I felt it needed to be more fitting to my theme. The Scalable Vector Graphics (SVG) icons I used are from Font Awesome Free. However, I believe one could also use SVG Repo.
|
||||||
|
|
||||||
|
I’ve tested this code on multiple web browsers without issues, so it should work fine under most circumstances.
|
||||||
|
|
||||||
|
#### _includes/admonition.html
|
||||||
|
|
||||||
|
```liquid
|
||||||
|
{% if include.type.size > 0 and include.title.size > 0 and include.body.size > 0 %}
|
||||||
|
{% assign types = "note, abstract, info, tip, success, question, warning, failure, danger, bug, example, quote" | split: ", " %}
|
||||||
|
{% if types contains include.type %}
|
||||||
|
<div class="admonition {{ include.type }} rounded">
|
||||||
|
<p class="admonition-title">{{ include.title }}</p>
|
||||||
|
<p>
|
||||||
|
{{ include.body }}
|
||||||
|
</p>
|
||||||
|
</div>
|
||||||
|
{% endif %}
|
||||||
|
{% endif %}
|
||||||
|
```
|
||||||
|
|
||||||
|
#### _scss/admonition.scss
|
||||||
|
|
||||||
|
```scss
|
||||||
|
$primary-color: #fc0;
|
||||||
|
$primary-bgcolor: rgba(55.59%, 44.41%, 0%, .4);
|
||||||
|
$admonitions:
|
||||||
|
//class (type), icon filename, icon/border color, title bg color
|
||||||
|
('note', 'pen-solid.svg')
|
||||||
|
('abstract', 'align-left-solid.svg')
|
||||||
|
('info', 'info-circle-solid.svg', '#00b0ff', '#293d52')
|
||||||
|
('tip', 'fire-solid.svg', '#ff9100', '#433a38')
|
||||||
|
('success', 'check-circle-solid.svg', '#00c953', '#294040')
|
||||||
|
('question', 'question-circle-solid.svg', '#00b8d4', '#293e4e')
|
||||||
|
('warning', 'exclamation-triangle-solid.svg', '#ff9100', '#564b3c')
|
||||||
|
('failure', 'times-circle-solid.svg', '#ff5252', '#564444')
|
||||||
|
('danger', 'bolt-solid.svg', '#ff1744', '#563e43')
|
||||||
|
('bug', 'bug-solid.svg', '#f50057', '#553c45')
|
||||||
|
('example', 'list-ol-solid.svg', '#9e9e9e', '#4c4c4c')
|
||||||
|
('quote', 'quote-right-solid.svg', '#9e9e9e', '#4c4c4c')
|
||||||
|
;
|
||||||
|
.admonition {
|
||||||
|
margin: 1.5625em 0;
|
||||||
|
overflow: hidden;
|
||||||
|
color: #808080;
|
||||||
|
page-break-inside: avoid;
|
||||||
|
background-color: #212121;
|
||||||
|
border-left: .3rem solid $primary-color;
|
||||||
|
border-radius: .1rem;
|
||||||
|
}
|
||||||
|
.admonition p {
|
||||||
|
padding: 0 1rem;
|
||||||
|
}
|
||||||
|
.admonition .admonition-title {
|
||||||
|
color: #ddd;
|
||||||
|
background-color: $primary-bgcolor;
|
||||||
|
font-weight: 700;
|
||||||
|
line-height: 3rem;
|
||||||
|
}
|
||||||
|
.admonition-title::before {
|
||||||
|
margin-right: .5rem;
|
||||||
|
width: 1.2rem;
|
||||||
|
height: 1.2rem;
|
||||||
|
display: inline-block;
|
||||||
|
content: '';
|
||||||
|
-webkit-mask-size: cover;
|
||||||
|
mask-size: cover;
|
||||||
|
background-color: $primary-color;
|
||||||
|
vertical-align: text-bottom;
|
||||||
|
}
|
||||||
|
@each $name, $icon, $icon-color, $title-color in $admonitions {
|
||||||
|
@if $icon-color {
|
||||||
|
.admonition.#{$name} {
|
||||||
|
border-left-color: #{$icon-color};
|
||||||
|
}
|
||||||
|
}
|
||||||
|
@if $title-color {
|
||||||
|
.admonition.#{$name} .admonition-title {
|
||||||
|
background-color: #{$title-color};
|
||||||
|
}
|
||||||
|
}
|
||||||
|
.admonition.#{$name} .admonition-title::before {
|
||||||
|
-webkit-mask: url("/assets/img/icons/#{$icon}") no-repeat 50% 50%;
|
||||||
|
mask: url("/assets/img/icons/#{$icon}") no-repeat 50% 50%;
|
||||||
|
@if $icon-color {
|
||||||
|
background-color: #{$icon-color};
|
||||||
|
}
|
||||||
|
}
|
||||||
|
}
|
||||||
|
```
|
||||||
|
|
||||||
|
## Assumptions
|
||||||
|
|
||||||
|
- General understanding of using a Linux terminal (command-line interface)
|
||||||
|
- `~ (tilde)` represents the $HOME (/home/username) of the current user when using BASH
|
||||||
|
- Steps prefixed with a “$” (dollar sign) represents the CLI (command-line interface) prompt
|
||||||
|
- Steps prefixed with a “#” (number sign) represents the CLI prompt with elevated user permissions (e.g. root)
|
||||||
|
- The text after the “$” or “#” is to be entered at the CLI
|
||||||
|
- Jekyll is already installed and configured
|
||||||
|
- The directory “project” represents the root of the website
|
||||||
|
|
||||||
|
## Add Admonitions To Jekyll
|
||||||
|
Install the admonition.html file to the _includes/ directory.
|
||||||
|
```shell
|
||||||
|
$ mv ~/Downloads/admonition.html /project/_includes/
|
||||||
|
```
|
||||||
|
|
||||||
|
Install the admonition.scss file to the _sass/ directory.
|
||||||
|
```shell
|
||||||
|
$ mv ~/Downloads/admonition.scss /project/_sass/
|
||||||
|
```
|
||||||
|
|
||||||
|
Edit style sheets to import admonition styles.
|
||||||
|
```shell
|
||||||
|
$ nano /project/assets/css/styles.scss
|
||||||
|
```
|
||||||
|
|
||||||
|
```shell
|
||||||
|
@import "admonition";
|
||||||
|
```
|
||||||
|
|
||||||
|
Add admonition icons.
|
||||||
|
```shell
|
||||||
|
$ mv ~/Downloads/*.svg /project/assets/img/icons/
|
||||||
|
```
|
||||||
|
|
||||||
|
```
|
||||||
|
pen-solid.svg
|
||||||
|
align-left-solid.svg
|
||||||
|
info-circle-solid.svg
|
||||||
|
fire-solid.svg
|
||||||
|
check-circle-solid.svg
|
||||||
|
question-circle-solid.svg
|
||||||
|
exclamation-triangle-solid.svg
|
||||||
|
times-circle-solid.svg
|
||||||
|
bolt-solid.svg
|
||||||
|
bug-solid.svg
|
||||||
|
list-ol-solid.svg
|
||||||
|
quote-right-solid.svg
|
||||||
|
```
|
||||||
|
|
||||||
|
## Usage
|
||||||
|
Adding an admonition to a post or page is a simple line of Liquid code. See the example of an info admonition below.
|
||||||
|
|
||||||
|
```liquid
|
||||||
|
{% include admonition.html type="info" title="Info" body="This is information intended to draw attention." %}
|
||||||
|
```
|
||||||
|
|
||||||
|
### Reference
|
||||||
|
- https://www.adamsdesk.com/posts/admonitions-jekyll/
|
||||||
|
|
||||||
Reference in New Issue
Block a user